Identity-free three-factor remote user authentication method
An authentication method and technology for remote users, applied in the field of remote user authentication, can solve problems such as reducing user experience and system fault tolerance, and violating three-factor authentication, achieving the effect of untraceability and anonymous login.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
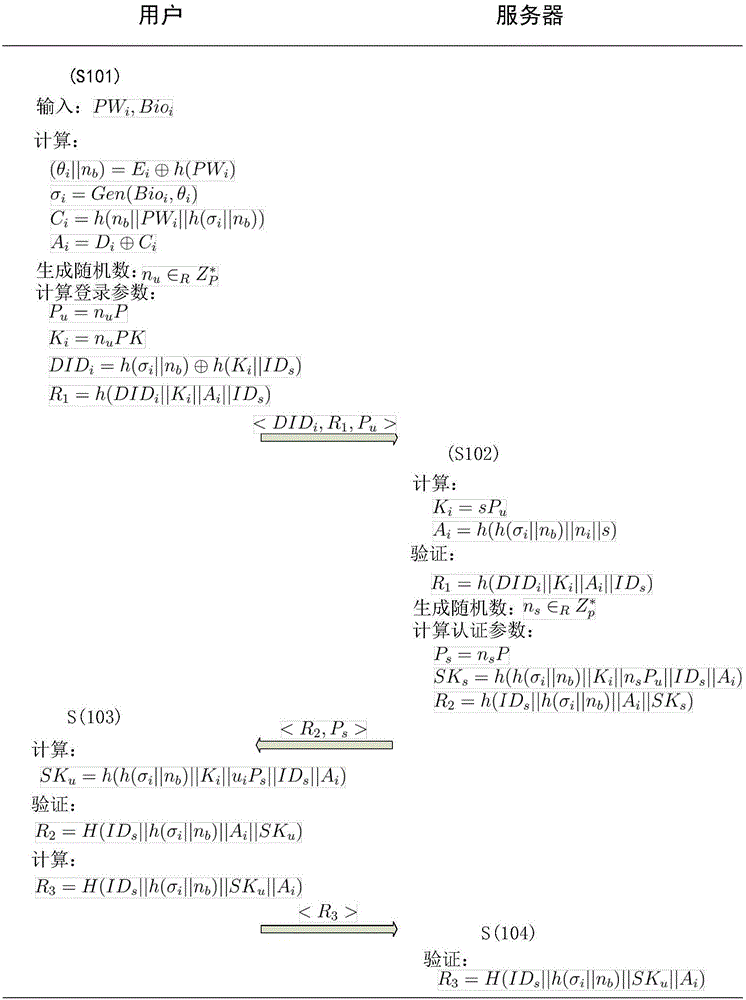
[0029] Specific embodiments of the present invention are described in detail below.
[0030] In step 1, the server initializes the elliptic curve E over the field GF(p) p And generate server private key s and public key PK=sP, select a one-way hash function h(·) and fuzzy extraction function {Gen(·), Rep(·,·)}. Finally, the server publishes the system public parameters p , h(·), Gen(·), Rep(·,·)>.
[0031] In step 2, the following stages are specifically included:
[0032] User U i Just select PW i Instead of selecting a user identity and entering biometric information Bio i , generated by fuzzy extraction function (σ i , θ i ) = Gen(Bio i ), where σ i is the eigenvalue, and θ i for auxiliary strings. Afterwards, the client generates h(σ i ||n b ) and send it to the server as a registration request through a secure channel, where n b is a random number.
[0033] The server receives user U i The registration request h(σ i ||n b ), generate a random number n i ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com