Method and system for malicious code detection based on virtual technology in Android system
A malicious code detection and Android system technology, applied in the field of malicious code detection based on virtual technology, to achieve the effect of real and more accurate simulation execution results, guaranteed detection results, and small memory usage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the above-mentioned purposes, features and advantages of the present invention more obvious and easy to understand, the technical solutions in the present invention will be further detailed below in conjunction with the accompanying drawings illustrate.
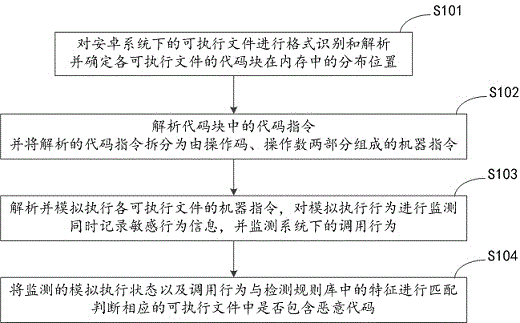
[0035] The present invention provides an embodiment of a method for detecting malicious codes based on virtual technology under the Android system, such as figure 1 shown, including:
[0036]S101: Perform format identification and analysis on executable files under the Android system, and determine the distribution position of the code blocks of each executable file in the memory. This process supports format identification and analysis of various executable files, including APK, DEX , ELF, OAT and other formats of executable files;
[0037] S102: Parse the code instruction...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com