Safety method and system based on asymmetric secret key pair
An asymmetric key and security system technology, which is applied in the field of security methods and systems based on asymmetric key pairs, can solve the problem of interfering with the use of public or private key pairing, the complexity of the asymmetric key pair process, and the impact on chips. operating system issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
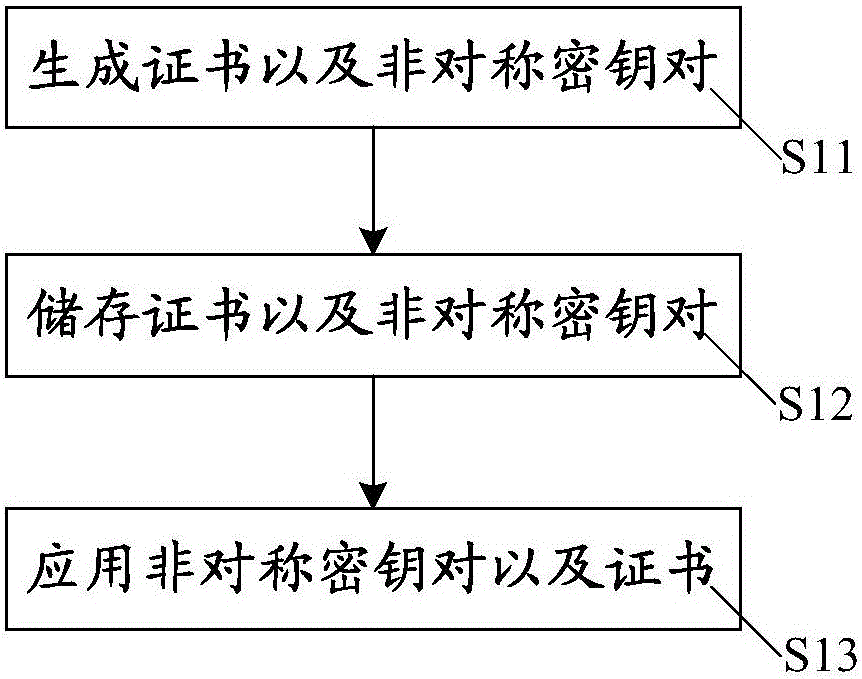
[0044] The embodiment of the present invention provides a security method based on an asymmetric key, such as figure 1 As shown, the above security methods based on asymmetric key pairs include:
[0045] S11. Generate a certificate and an asymmetric key pair corresponding to the certificate according to the generation instruction, where the asymmetric key pair includes a corresponding public key and a private key.
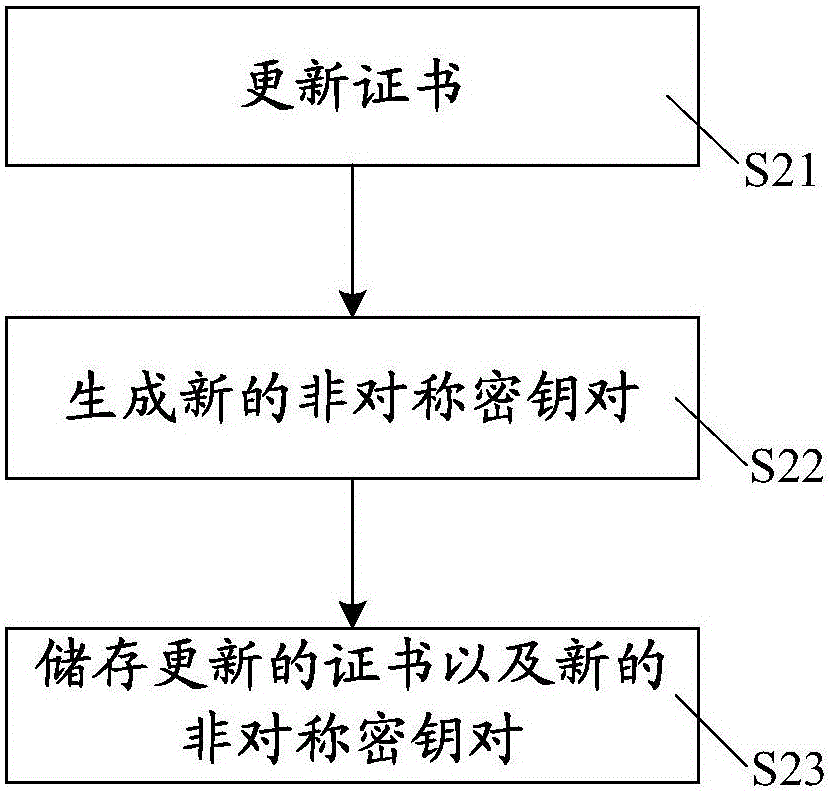
[0046]S12. Store the certificate in the certificate storage; store the public key, the unique identifier of the private key, and the unique identifier of the certificate in the first storage. The private key, the unique identifier of the public key and the unique identifier of the certificate are stored in the second storage. Wherein, the unique identifier of the private key is associated with the private key, the unique identifier of the certificate is associated with the certificate, and the unique identifier of the key is associated with the public key. The ce...
Embodiment 2
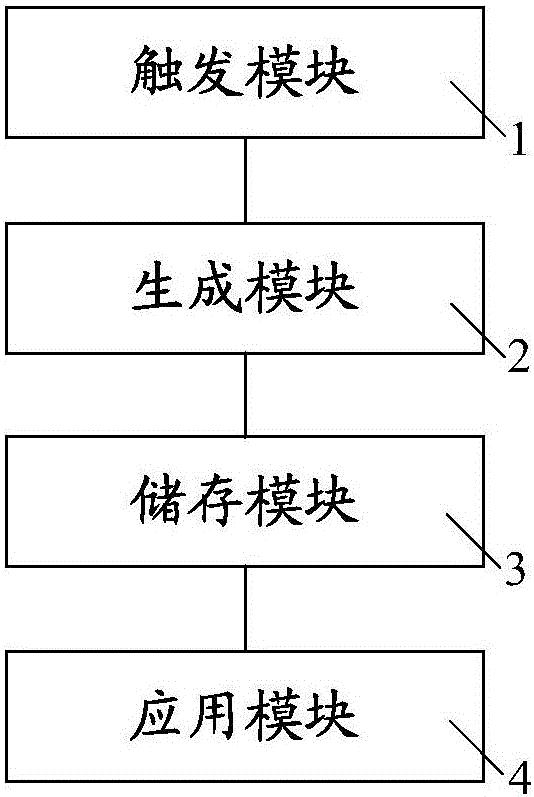
[0070] This embodiment provides a security system based on an asymmetric key pair. The security system based on asymmetric key pair matching mentioned in this embodiment is applicable to the security method based on the asymmetric key pair in the first embodiment. ,Such as image 3As shown, the security system based on an asymmetric key pair in this embodiment includes: a trigger module 1, a generation module 2, a storage module 3, and an application module 4, wherein the trigger module 1 is used to generate a trigger instruction, and the trigger instruction includes generating instruction. The generation module 2 is connected with the trigger module 1, and the generation module 2 is used to generate an asymmetric key pair and a certificate according to the generation instruction. The storage module 3 is connected to the generation module 2, and the storage module 3 includes a certificate storage, a first storage and a second storage which are connected to each other by signa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com