Code reuse attach detection method based on virtual function table inheritance relation
A technology of virtual function table and inheritance relationship, applied in error detection/correction, electrical digital data processing, software testing/debugging, etc., can solve the problems of high performance overhead, low accuracy, poor generality, etc. speed, improved accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The following description and drawings sufficiently illustrate specific embodiments of the invention to enable those skilled in the art to practice them. Other embodiments may incorporate structural, logical, electrical, process, and other changes. The examples represent only possible variations. Unless expressly required, individual components and functions are optional and the order of operations may vary. Portions and features of some embodiments may be included in or substituted for those of other embodiments.
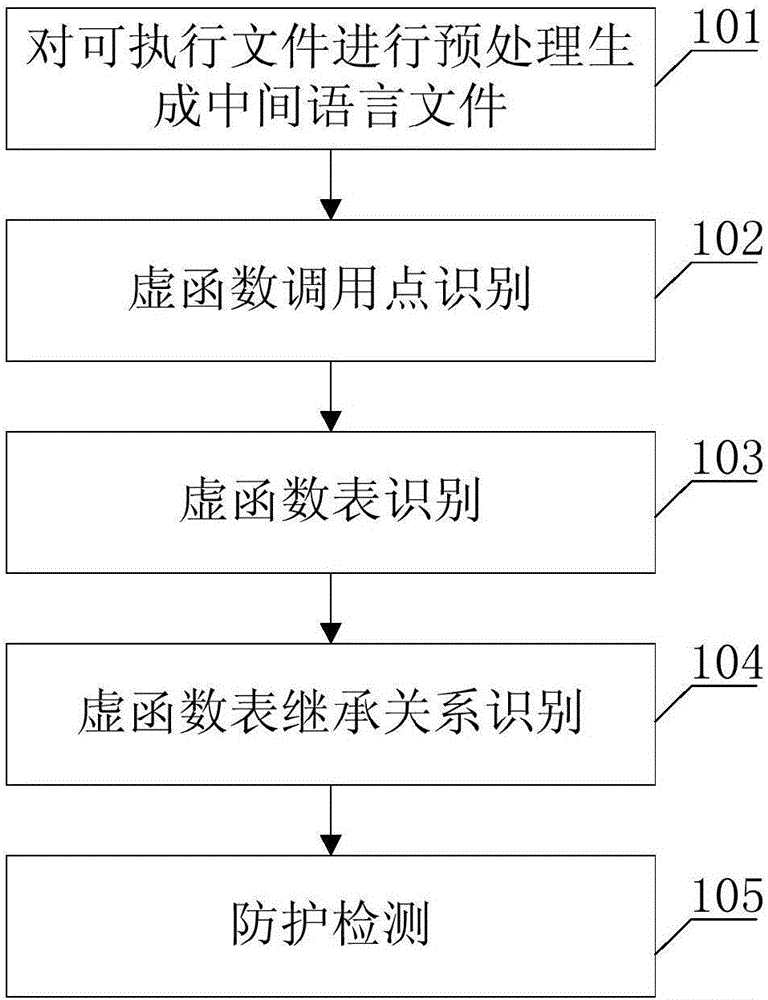
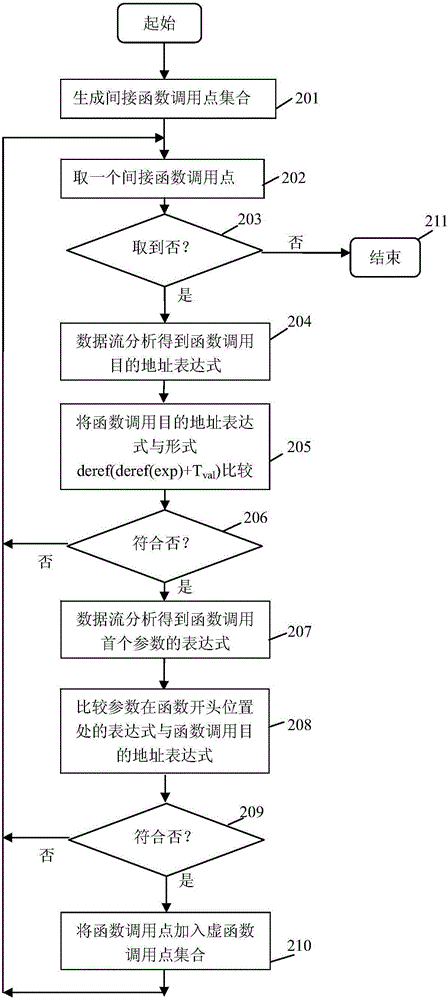
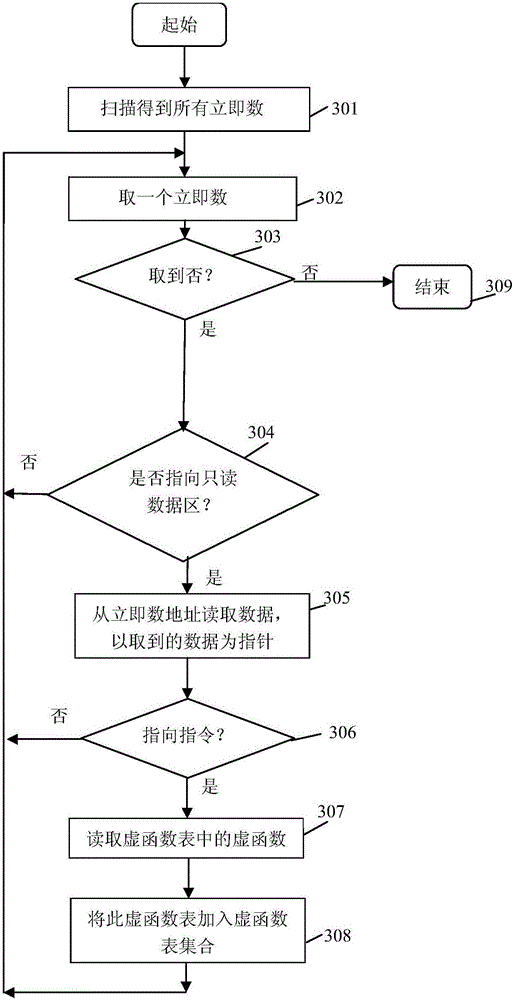
[0043] like figure 1 As shown, in some illustrative embodiments, a method for detecting code reuse attacks based on virtual function table inheritance relationship is provided, including:
[0044] 101: Preprocessing. The executable file is preprocessed to generate an intermediate language file, including: using the tool toil of the binary program behavior monitoring and analysis platform, taking the executable file as input, disassembling and converting ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com