ID card reading method and system
A technology of ID cards and certificates, applied in the field of ID cards, can solve the problems of complex implementation and high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0040] This embodiment provides a method for reading an ID card;
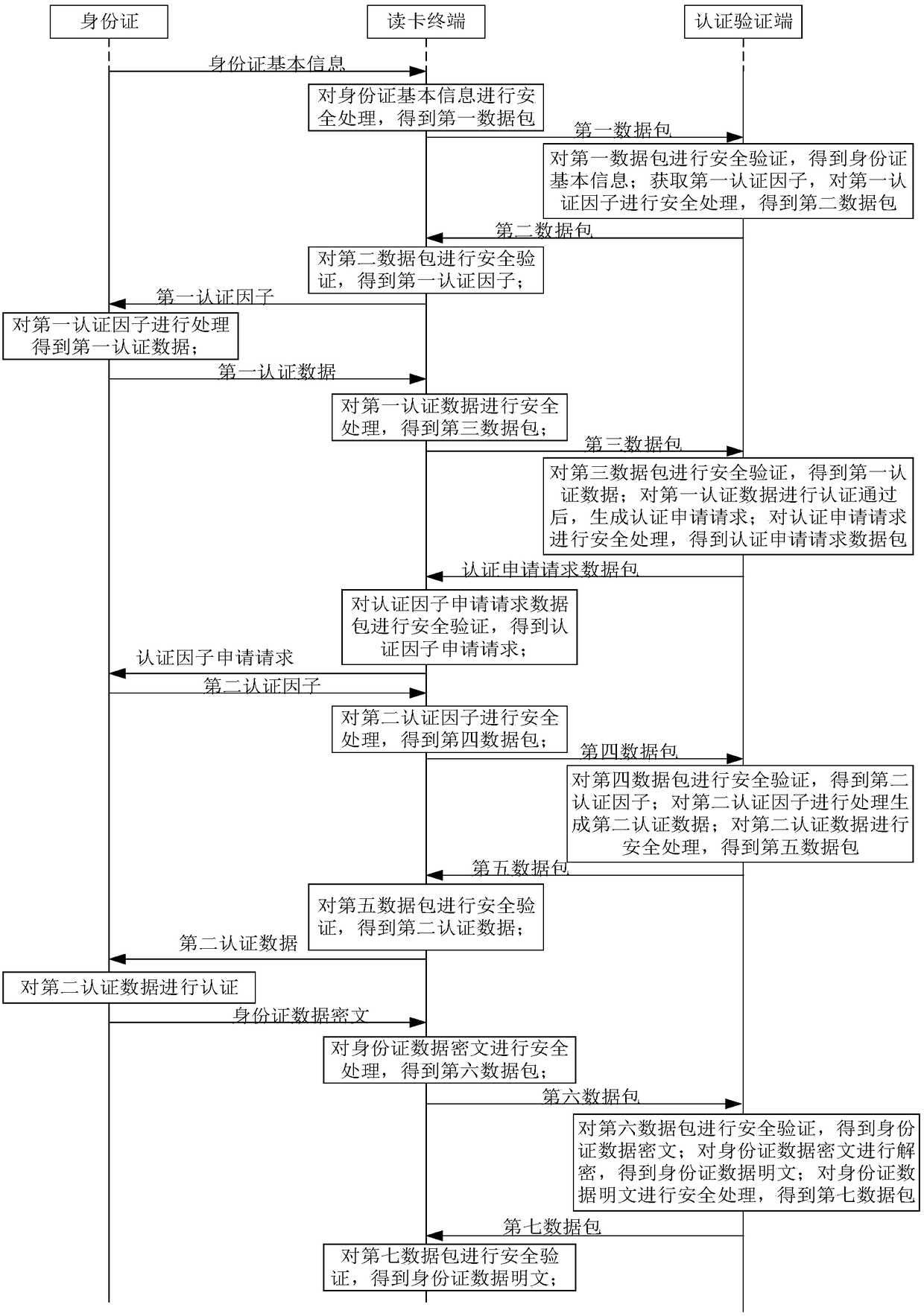
[0041] figure 1 It is a flow chart of the ID card reading method in this embodiment. The ID card reading method in this embodiment includes the following steps (101-109):
[0042] Step 101: the card reading terminal receives the basic information of the ID card sent by the ID card, performs security processing on the basic information of the ID card, and obtains the first data packet; and sends the first data packet to the authentication verification terminal;
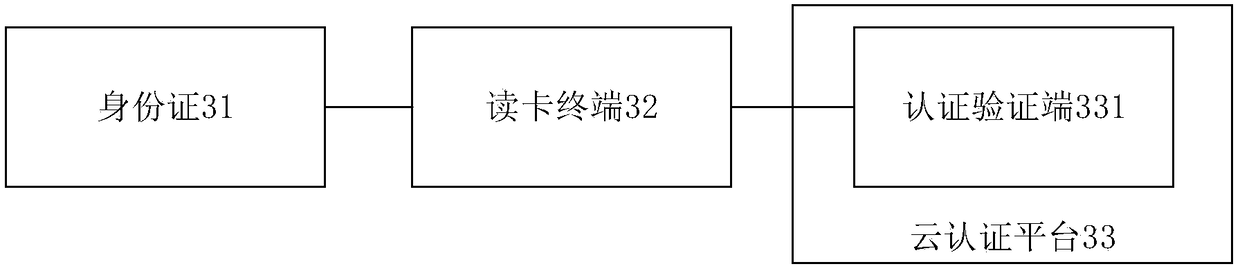
[0043] In this embodiment, the card reading terminal may be a card reader, or other terminals with a card reading function (such as a mobile phone integrated with a card reading function, a USBKEY integrated with a card reading function, etc.).
[0044] In this embodiment, the basic information of the ID card can be the serial number of the ID card, the application data used to indicate the relevant information of the application set in the ID card, t...
Embodiment approach
[0103] As an optional implementation of this embodiment, the card reader terminal sends a card search request to the scheduling device, and after the scheduling device selects the authentication verification terminal, it sends the port number of the selected authentication verification terminal to the card reader terminal. Specifically, there are the following implementation methods: Mode 1: After the scheduling device selects the authentication verification terminal, the port number of the selected certification verification terminal is directly sent to the card reader terminal; Mode 2: the scheduling device carries the port number of the selected certification verification terminal in the card search Send it to the card reader terminal in the request response; method 3: carry the port number of the authentication verification terminal selected by the dispatching device in the card search request and send it to the authentication verification terminal, and the authentication ve...
Embodiment 2
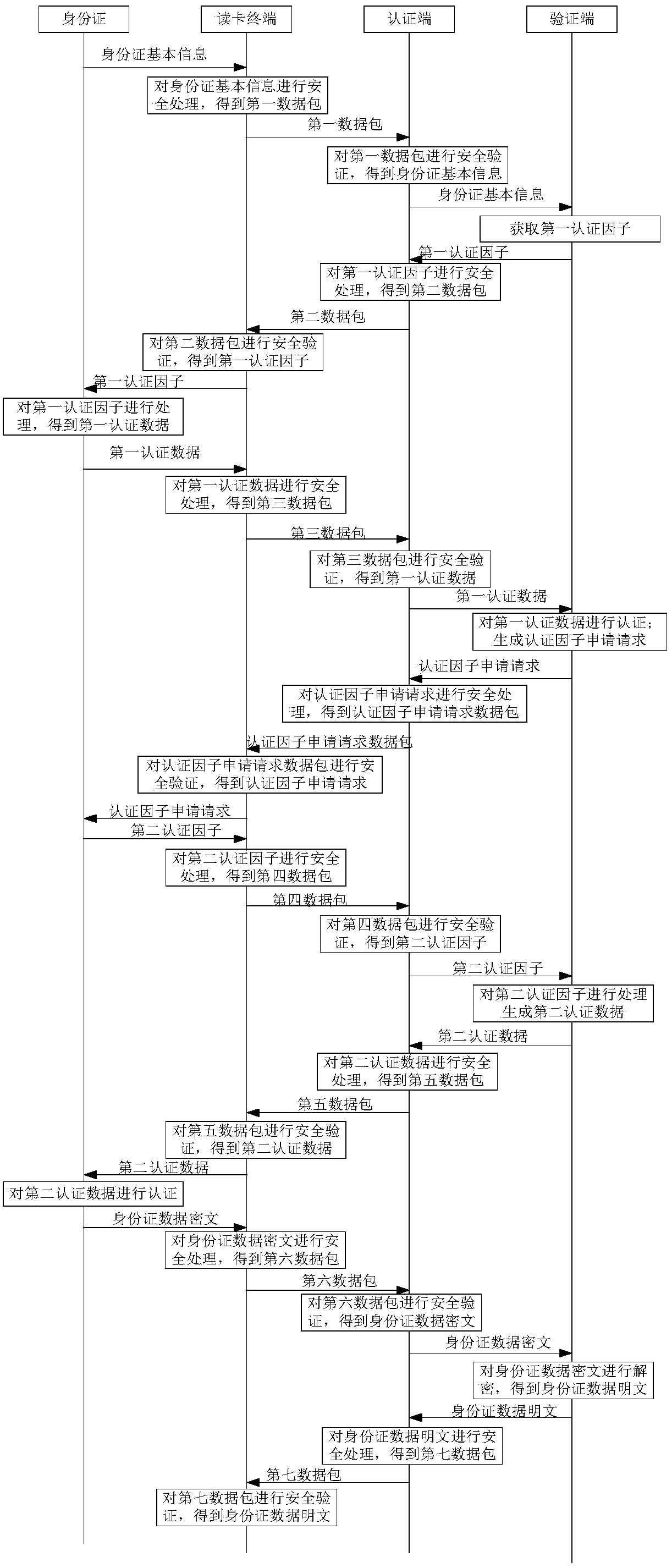
[0148] This embodiment provides another ID card reading method.
[0149] figure 2 It is a working flow chart of an ID card reading method provided in this embodiment. The ID card reading method provided in this embodiment mainly includes the following steps (201-214):
[0150] In this embodiment, the authentication verifier in the cloud authentication platform includes an authenticator and a verifier. Wherein, the authentication terminal may be a security chip, which is used to store digital certificates, private keys, session keys, authentication and decryption keys, and perform encryption and decryption operations to ensure the security of data transmission. The verification end is the verification security control module, which is used to decrypt the ciphertext data read from the ID card to obtain the plain text of the ID card data that can be displayed.
[0151] Step 201: the card reading terminal receives the basic information of the ID card sent by the ID card, perfo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com