Two-factor authentication system and method based on smart phone and user password
A user password, smart phone technology, applied in the field of computer networks, can solve the problems of high cost of identification equipment, no definite conclusion about the identification accuracy, unrealistic and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0096]An embodiment of the present invention will be described in detail below in conjunction with the accompanying drawings.
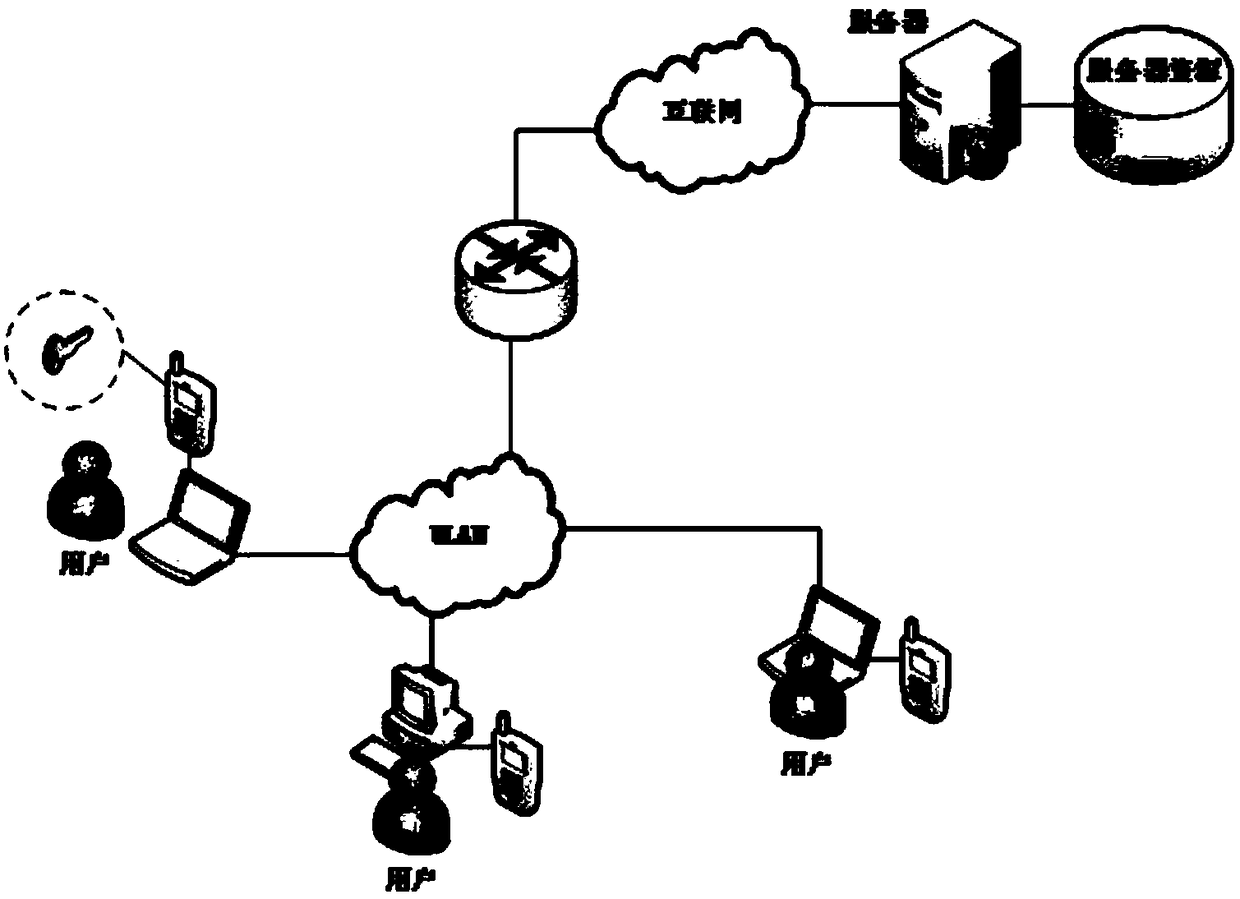
[0097] like figure 1 As shown, the two-factor authentication system based on smart phones and user passwords in this embodiment includes three entities: user smart phones, browsers and Web servers.
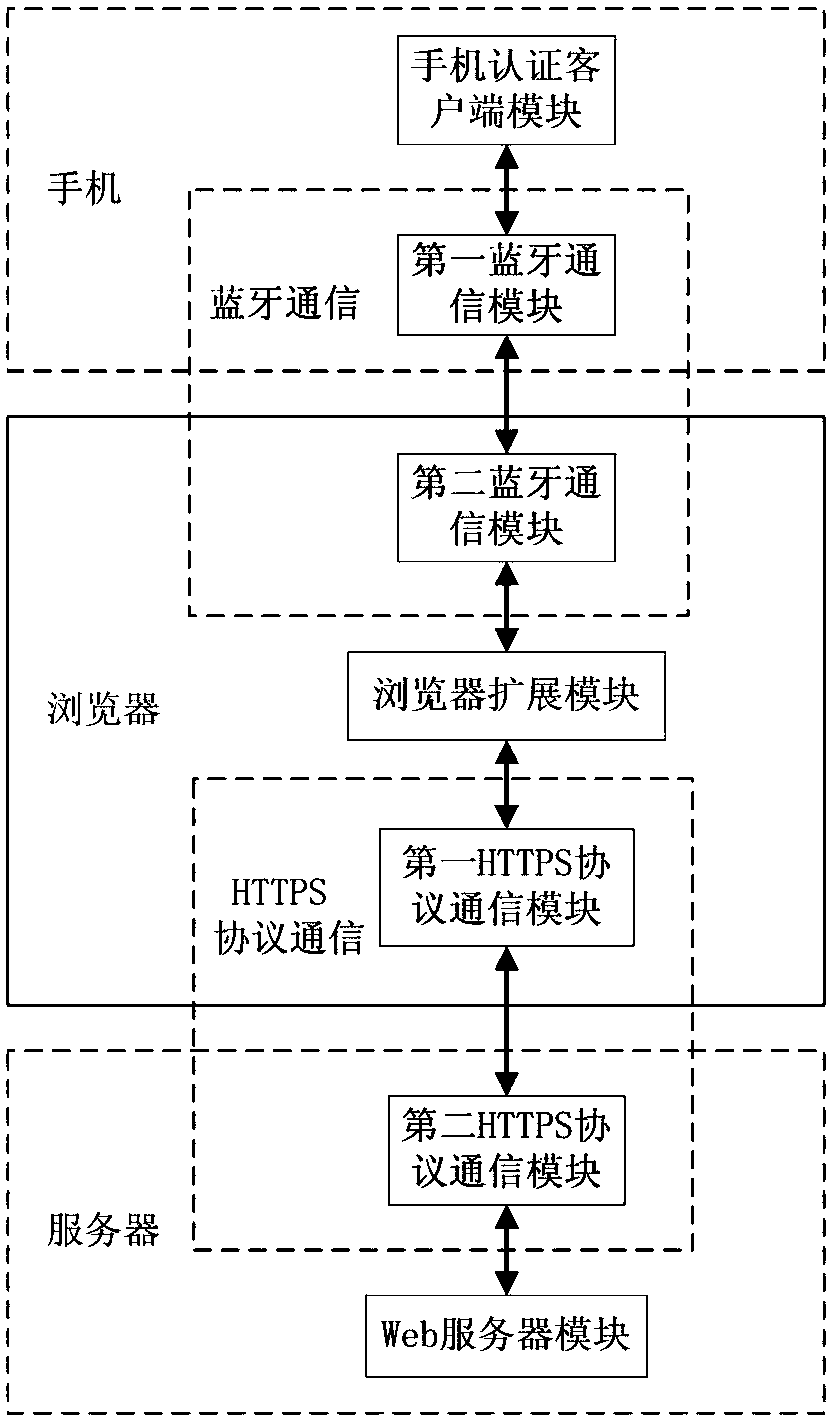
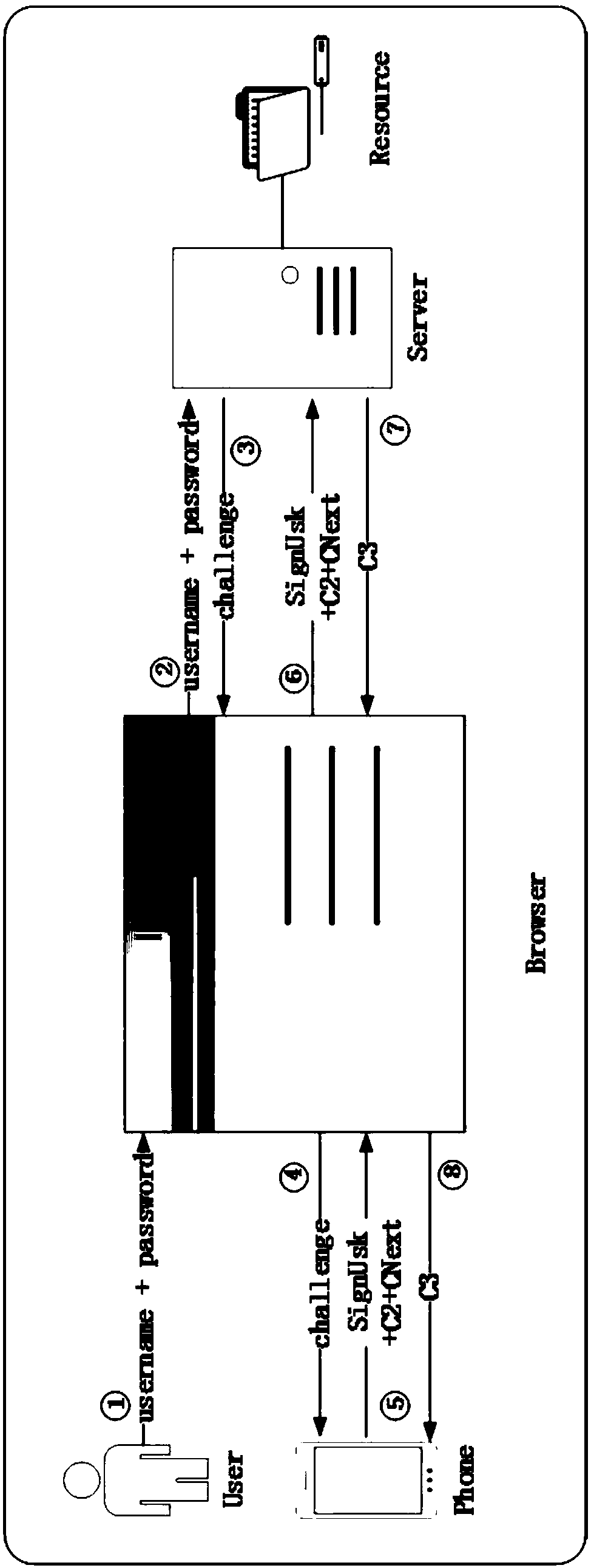
[0098] like figure 2 As shown, the two-factor identity authentication system based on smart phones and user passwords in this embodiment, the smart phone is the smart phone that the user carries and uses daily, and the system includes: a mobile phone authentication client set in the user's smart phone The terminal module and the first bluetooth communication module, the second bluetooth communication module, the browser extension module and the first HTTPS protocol communication module arranged in the browser, the second HTTPS protocol communication module and the web server module arranged in the web server. The user's smart phone and the browser real...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com