Clustering method for network behavior habits based on K-means and LDA (Latent Dirichlet Allocation) two-way authentication
A technology of two-way verification and clustering methods, applied in text database clustering/classification, character and pattern recognition, instruments, etc., can solve problems such as poor efficiency and very bad answers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
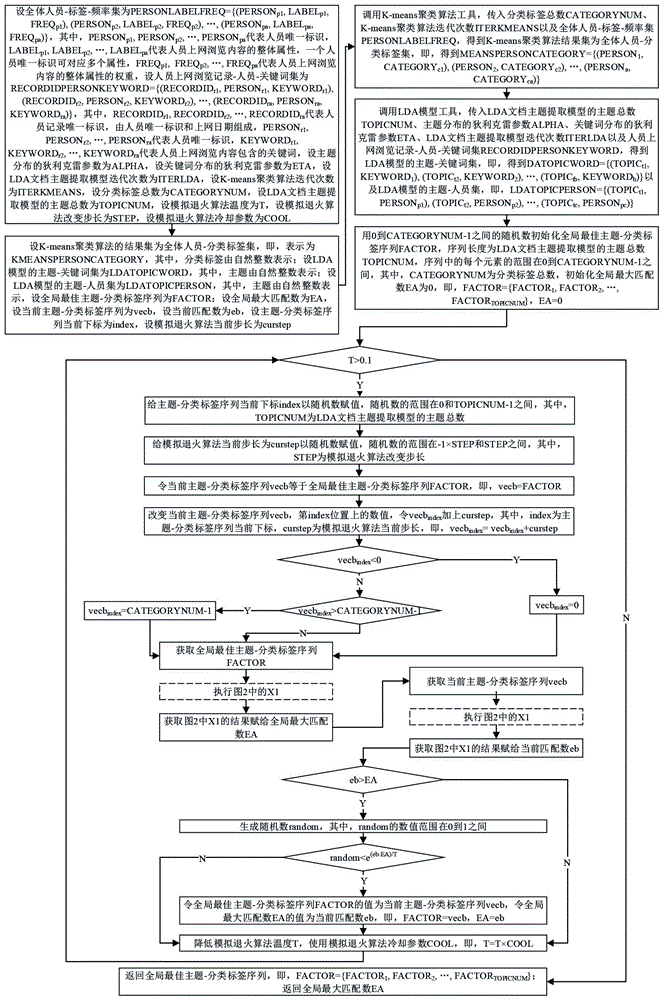
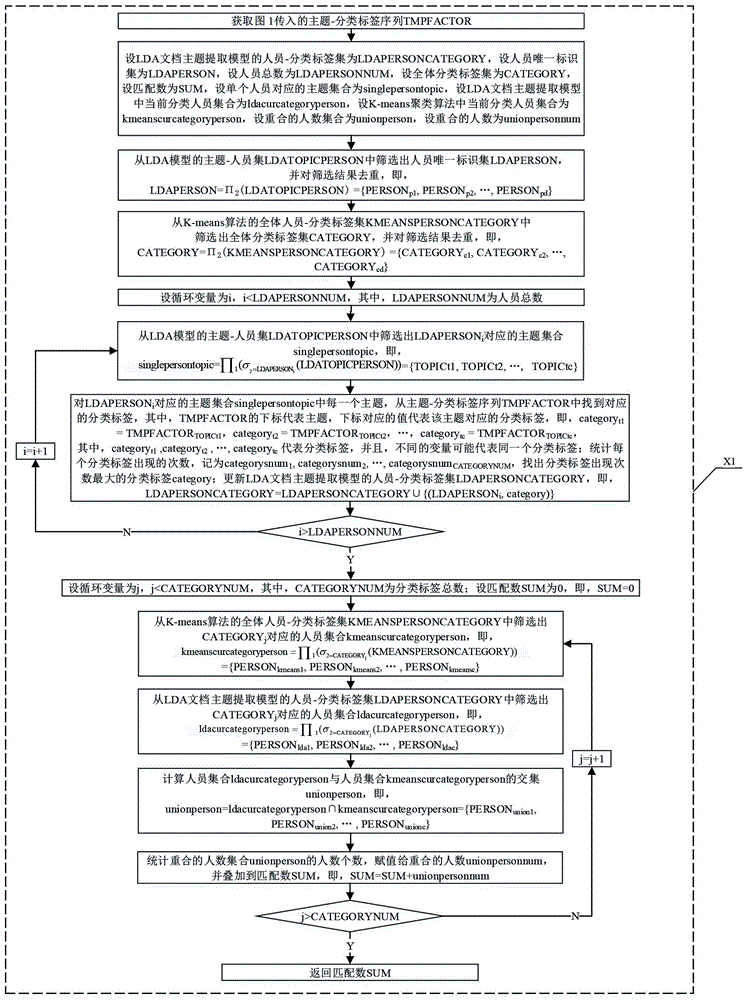
[0065] The technical solution of the present invention will be described in detail below in conjunction with the drawings:
[0066] As attached figure 1 , Step A1 to Step A26 of the main process of the simulated annealing algorithm:
[0067] Step A1: Set the set of all personnel-label-frequency as PERSONLABELFREQ={(PERSON p1 , LABEL p1 ,FREQ p1 ), (PERSON p2 , LABEL p2 , FREQ p2 ), …, (PERSON pa , LABEL pa , FREQ pa )}, where PERSON p1 , PERSON p2 , …, PERSON pa The unique identification of the representative, LABEL p1 , LABEL p2 , …, LABEL pa Represents the overall attributes of personnel browsing content on the Internet. A unique identifier of a person can correspond to multiple attributes, FREQ p1 ,FREQ p2 , …,FREQ pa On behalf of the weight of the overall attribute of the personnel browsing content, set the personnel browsing record-person-keyword set as RECORDIDPERSONKEYWORD={(RECORDID r1 , PERSON r1 , KEYWORD r1 ), (RECORDID r2 , PERSON r2 ,KEYWORD r2 ), …, (RECORDID ra ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com