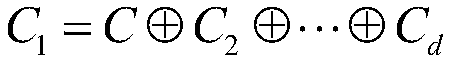An Arbitrary Order Mask Protection Method with Variable Complexity
A complex and variable technology, applied in the field of password security, can solve the problems of high-order masking overhead, high-order masking schemes are difficult to apply, and first-order masking schemes cannot meet security requirements, etc., to achieve resource overhead Low-cost, practical, and scalable effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to facilitate those of ordinary skill in the art to understand and implement the present invention, the present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the implementation examples described here are only used to illustrate and explain the present invention, and are not intended to limit this invention.
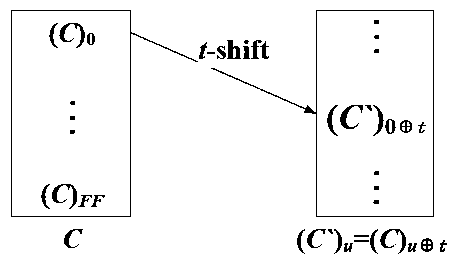
[0048] The present invention proposes a lightweight arbitrary-order mask protection scheme, which is called a PFD scheme (Polynomial Function Division Scheme), to effectively resist arbitrary-order side channel attacks.
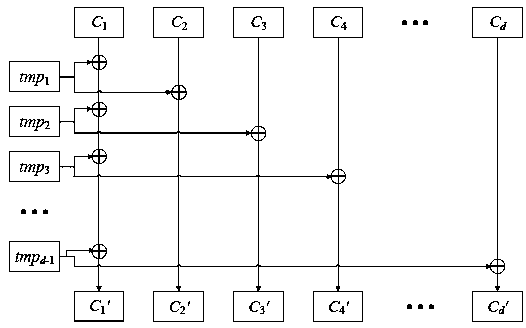
[0049] The embodiments of the present invention reconstruct nonlinear operations to replace nonlinear components in the original encryption algorithm, including logic function splitting algorithms, logic function adjustment algorithms, logic function refresh algorithms and a complete PFD solution.
[0050] The nonlinear component S(x) of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com