Webpage source code three-layer encryption method
An encryption method and source code technology, applied in the direction of program/content distribution protection, instruments, electronic digital data processing, etc., can solve the problems of single algorithm, limited defense effect, normal website access threats, etc., to consume hardware resources and increase difficulty. , the effect of slowing down the attack speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. Although the present invention will be described and illustrated in conjunction with some specific embodiments, it should be noted that the present invention is not limited to these embodiments. On the contrary, any modification or equivalent replacement made to the present invention shall be included in the scope of the claims of the present invention.
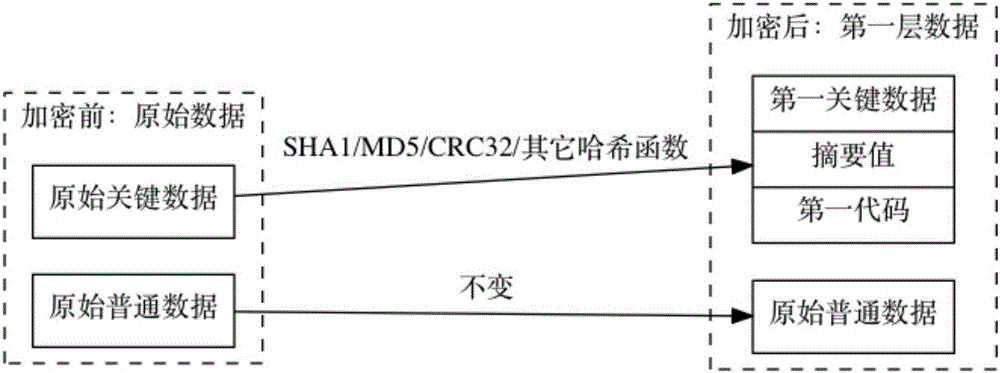
[0020] The method of the present invention not only uses the obfuscation of the prior art to resist non-targeted automatic attacks, but also uses a minimal character set to rewrite some important data in the code. The computer language is also extremely unfriendly; for a small part of the key data in the code, a few characters can be deliberately erased, but providing a digital summary forces the client to perform exhaustive enumeration for a short time.
[0021] The data in the page ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com