Information processing device and method
The technology of an information processing device and an information processing method is applied in the field of information security and can solve the problems of easy cracking of algorithms and low information security, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
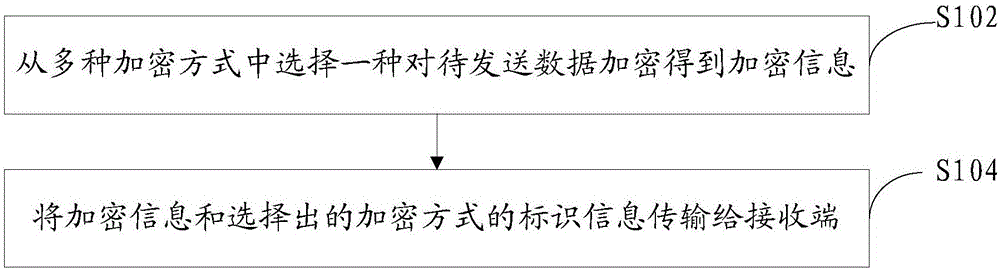
[0052] In order to solve the problem that in the current technology, the two sides of the information exchange always carry out encrypted communication based on the mechanism of the pre-agreed encryption method, which leads to low information security and is easy to be cracked by an illegal third party in the long-term communication process, an information processing method is proposed method, please combine figure 1 :
[0053] S102. Select one of multiple encryption methods to encrypt the data to be sent to obtain encrypted information.
[0054] The data to be sent may include the information required for information interaction between the sender and the receiver. For example, when the APP on the mobile terminal needs to interact with the server, the mobile terminal as the sender may need to send some request data to the server to request The server provides corresponding services, such as payment service, page refresh service, identity authentication service, etc. The raw d...
no. 2 example
[0068] This embodiment provides an information processing method, which is used for an information receiving end to decrypt the information encrypted by using the information processing method provided in the first embodiment. In order to make those skilled in the art understand the advantages and details of the information processing method in this embodiment, the following combination figure 2 Be explained:
[0069] S202. Receive the encrypted information and the identification information of the encryption method transmitted by the sending end.
[0070] Since the sending end may send encrypted information and identification information separately using different communication links and different communication methods, the receiving end may also need to receive encrypted information and identification information separately. Now suppose that the sender transmits the encrypted information and identification information to the receiver in the form of a data message, and the ...
no. 3 example
[0083] This embodiment provides an information processing method. On the basis of combining the first embodiment and the second embodiment, this embodiment will describe the aforementioned information processing method in detail from the interaction process between the sending end and the receiving end. Please refer below image 3 :
[0084] S302. The sending end digitally signs the original data according to a preset rule to obtain first signed data.
[0085] Digital signature, also known as public key digital signature and electronic signature, is a method similar to ordinary physical signature written on paper, but it uses the technology in the field of public key encryption to identify digital information.
[0086] The data to be sent includes the original data that the sender actually needs to send to the receiver. For example, in the data to be sent by the mobile terminal to the server through the APP, the included original data may be the request data generated accordi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com