Shadow stack implementation method for integrity protection of multi-thread backward control flow
A technology of integrity protection and implementation method, applied in the field of shadow stack implementation of multi-threaded backward control flow integrity protection, can solve problems such as inapplicability of multi-threading, modification of source code and imperfect hiding mechanism, etc., to achieve convenient deployment, The effect of convenient and quick access and improved protection capability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
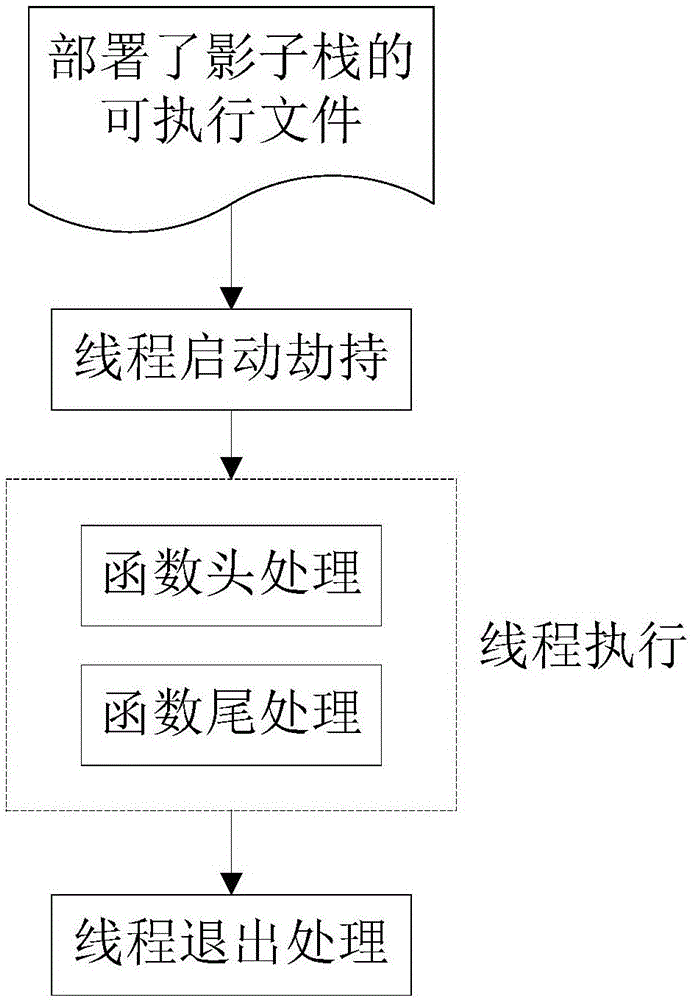
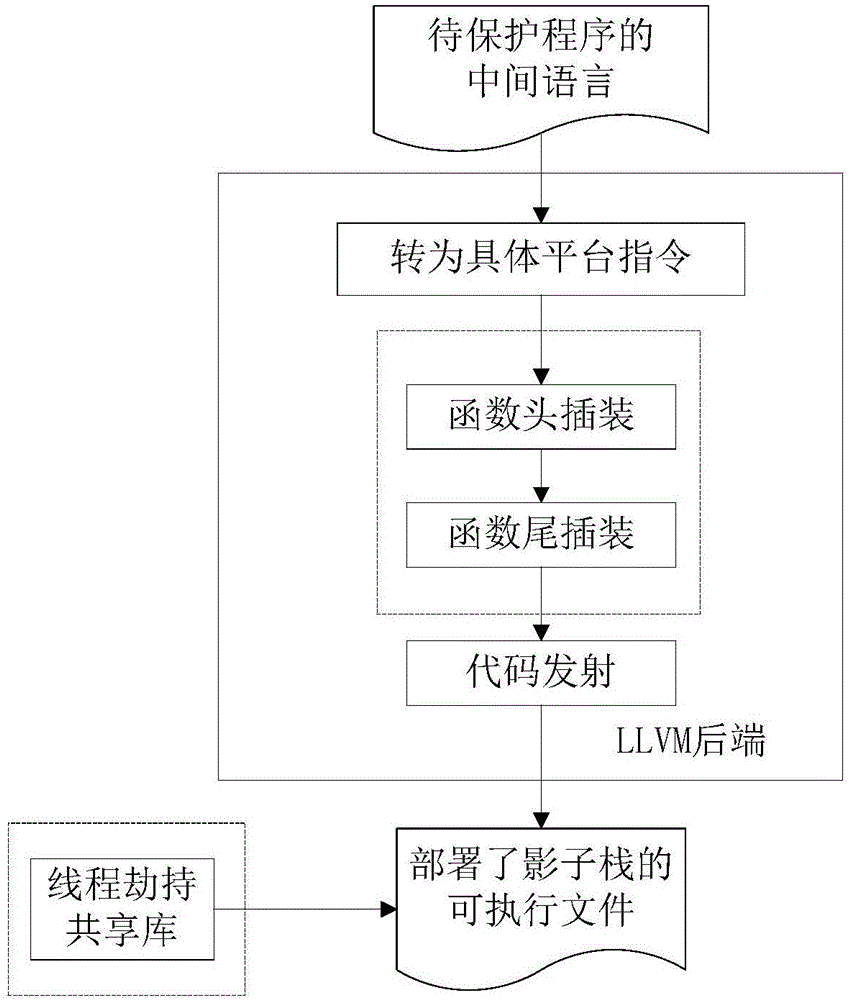
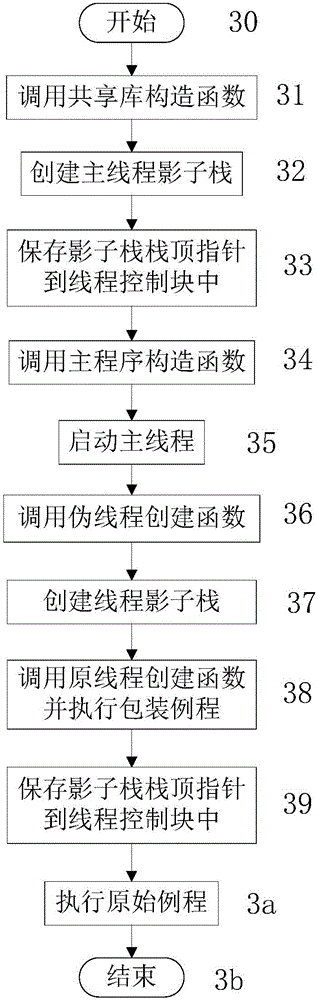
[0047] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
[0048] Unless the context clearly states otherwise, the number of elements and components in the present invention can exist in a single form or in multiple forms, and the present invention is not limited thereto. Although the steps in the present invention are arranged with labels, they are not used to limit the order of the steps. Unless the order of the steps is clearly stated or the execution of a certain step requires other steps as a basis, the relative order of the steps can be adjusted. It can be understood that the term "and / or" used herein refers to and covers any and all possible combina...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com