A Hardware Protection Device against Buffer Overflow Attack
A buffer overflow and hardware protection technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as program crash, increase software complexity, increase system burden, etc., and achieve the effect of high execution efficiency, increased security, and good portability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] See figure 1 , figure 2 As shown, its specific implementation is as follows:
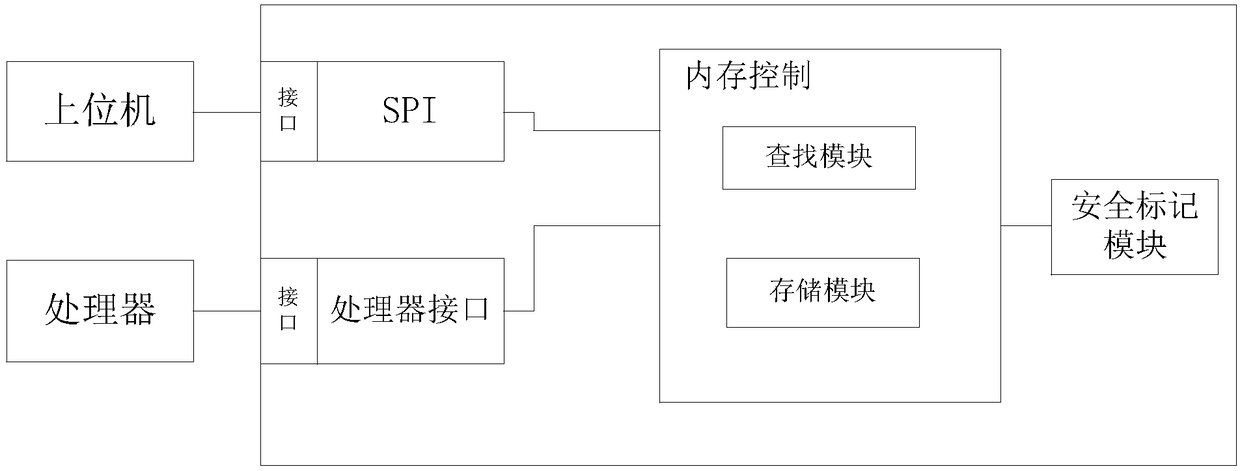
[0029] The present invention designs a hardware protection device against buffer overflow attacks, which mainly consists of the following parts. SPI (Serial Peripheral Interface) module, processor interface module. The internal processing module mainly includes a counter module, a safety mark module, and a memory control module. The relationship between them is that the memory control module is the most important module, and other modules are connected around it. Wherein the SPI module provides a download interface for it; the memory control module is connected with the processor through the processor interface; the check value used by the hash to calculate the code is stored in the storage module of the memory control module.
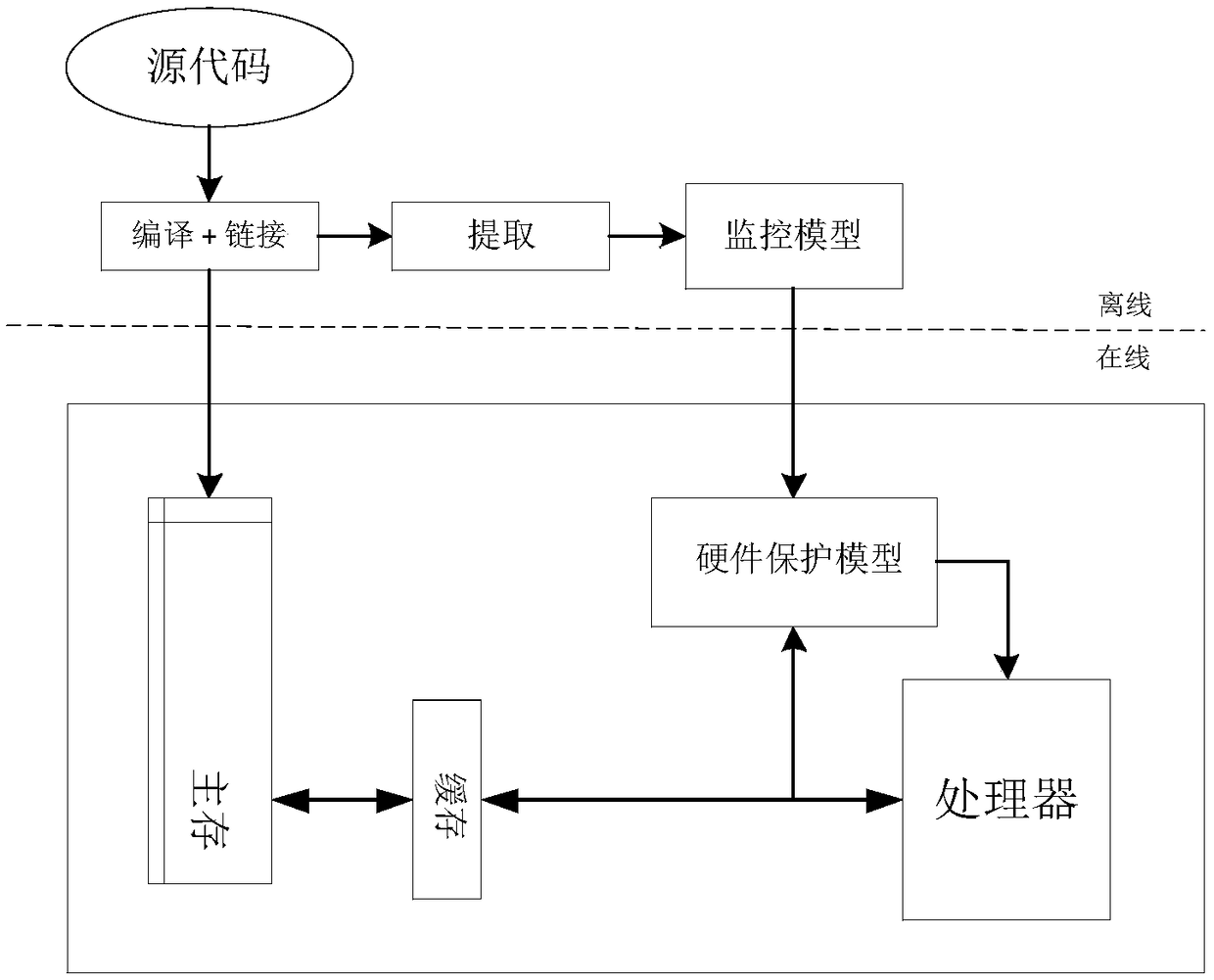
[0030] figure 1 The architecture of the hardware protection device is described. Before it works, the executable code part of the extraction tool needs to be ex...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com