Dynamic signature method, client using the same and server
A client-side and server-side technology, applied in the field of identity authentication, can solve problems such as user account theft and authentication failures, and achieve the effect of increasing attack costs and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
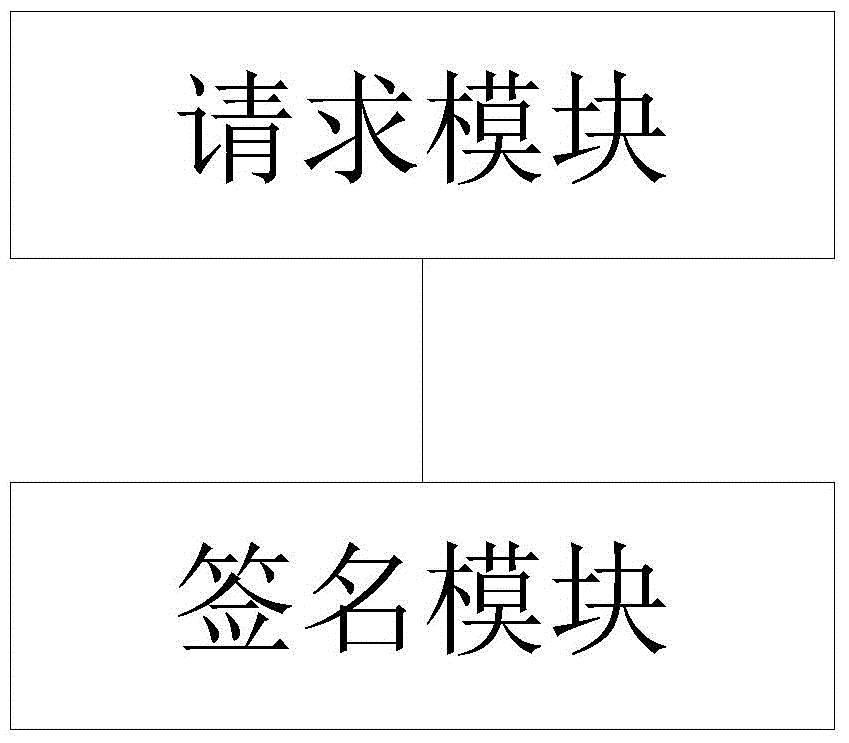
Image
Examples
Embodiment Construction
[0046] The technical solutions of the present application will be described in further detail below in conjunction with the accompanying drawings and embodiments, and the following embodiments do not limit the present application.
[0047] Generally speaking, in Internet-based applications, there is a client on the user side and a server on the service provider's side. Clients are generally applications installed on users' mobile terminals, computers or other smart devices, and some clients are directly webpages provided by service providers. User authentication is required for opening services between the client and the server, performing verification during business operations, and canceling services.
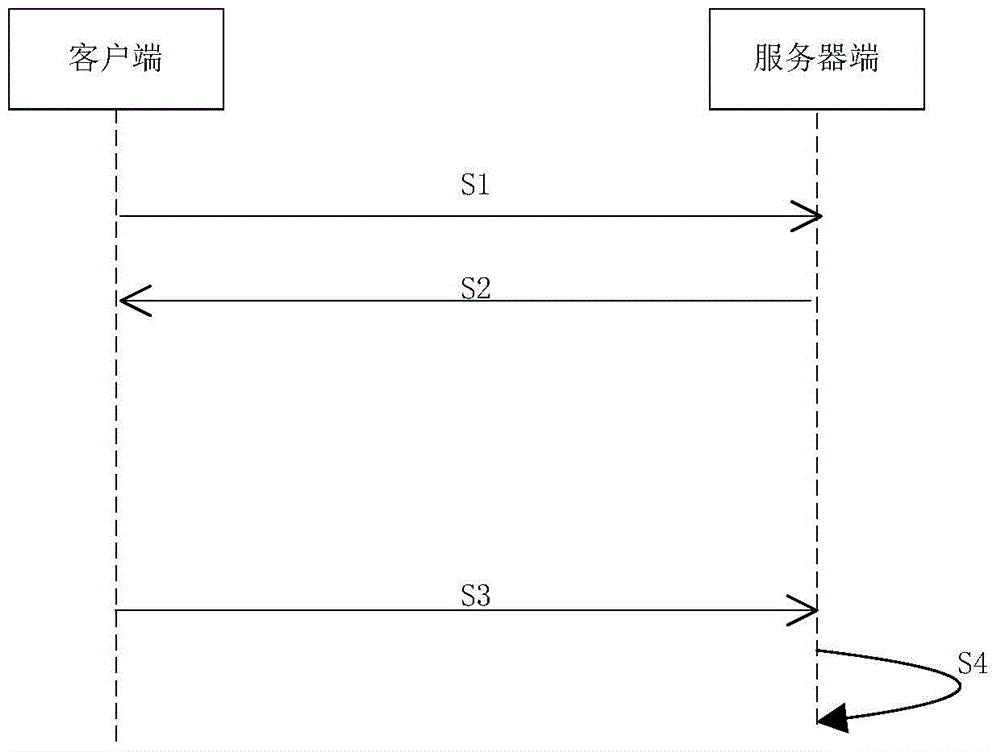
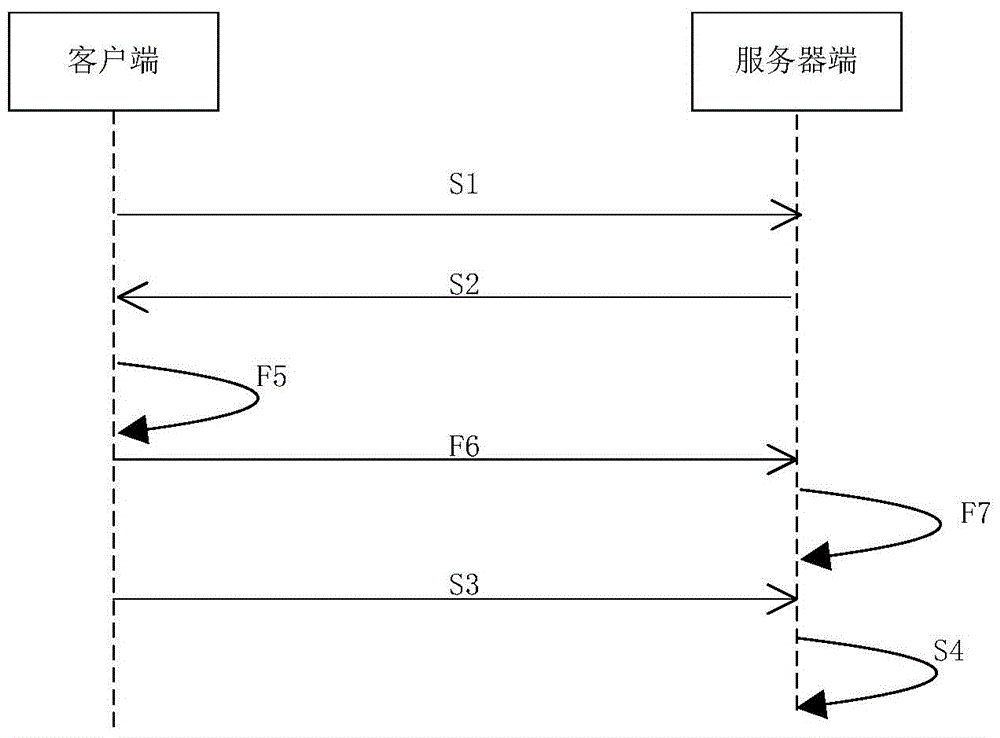
[0048] The dynamic signature method of this embodiment is as follows: figure 1 shown, including the following steps:
[0049]S1. The client sends an authentication request to the server.
[0050] S2. After receiving the authentication request, the server sends an authentic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com