Malicious code behavior analyzer
A technology of behavior analysis and static analysis, which is applied in the field of malicious code behavior analysis devices, can solve problems such as being unable to deal with high-level malicious code attacks, and achieve the effect of anomaly detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
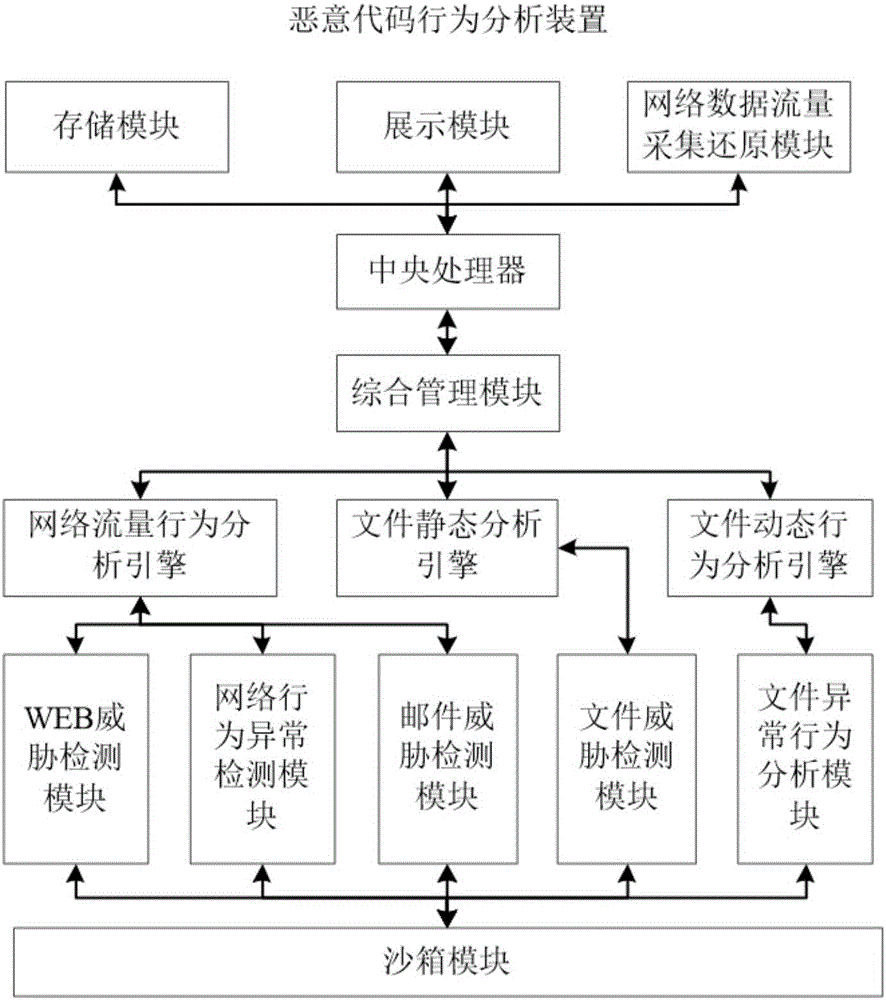
[0017] A malicious code behavior analysis device provided by an embodiment of the present invention realizes reorganization and restoration of network data streams, realizes abnormal detection of network behaviors, restores, extracts and analyzes suspicious files, and places suspicious files in a sandbox template It realizes the dynamic monitoring and analysis of file behavior, and combines the results of static analysis and dynamic analysis to give the information security risk degree of suspicious files, which solves the current technical problem of being unable to cope with increasingly severe high-level malicious code attacks.
[0018] In order to make the purpose, features and advantages of the present invention more obvious and understandable, the technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with the accompanying drawings in the embodiments of the present invention. Obviously, the following T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com