Weak password screening method
A screening method and weak password technology, applied in the field of information security, can solve problems such as long verification time, omission, and unsuitability for huge password verification, so as to achieve the effect of expanding capacity and reducing missed detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
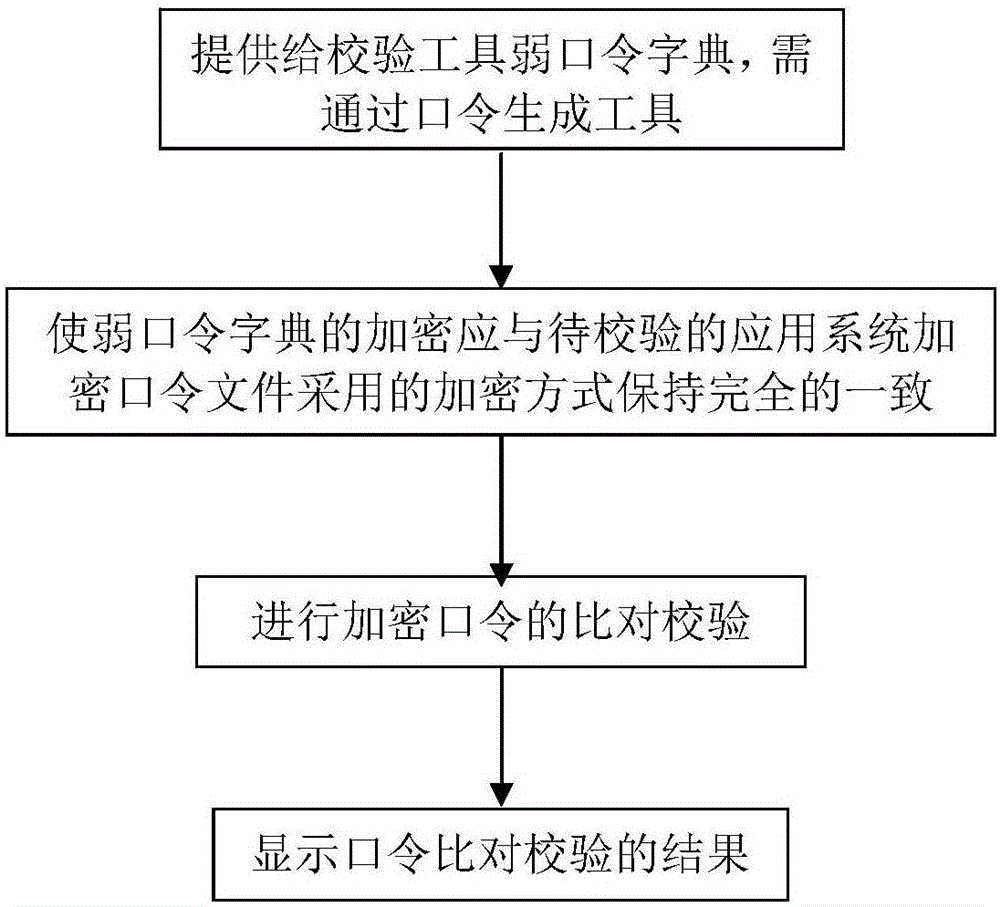
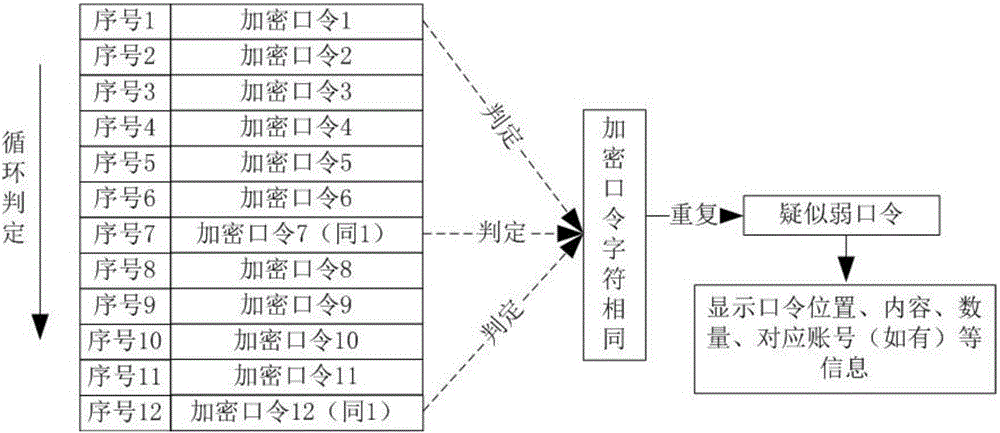
[0035] In the present invention, the definition of a weak password cannot simply be defined as a weak password consisting of simple numbers, letters, and symbols. It should be pointed out that passwords that are easy to be guessed by others or cracked by cracking tools should also be included in the so-called weak passwords in the present invention. This includes unknown and repeated passwords in the same field, industry or system. The same password found in the password verification process, regardless of whether the password is encrypted or not, can be defined as a weak password in the present invention. , so as to provide an effective supplement for the weak password dictionary generation tool.
[0036] In the present invention, the weak password verification tool is mainly used to verify encrypted or non-encrypted passwords of various application systems. The tool not only adopts the traditional method of using a weak password dictionary to verify plaintext and encrypted ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com