IDS rule optimization system and optimization method
An optimization method and rule technology, applied in the field of network security, can solve the problems of IDS false alarms and alarms, and achieve the effect of reducing the false alarm rate, reducing the number of alarms, and optimizing IDS rules
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention is further illustrated below by means of examples, but the present invention is not limited to the scope of the examples.
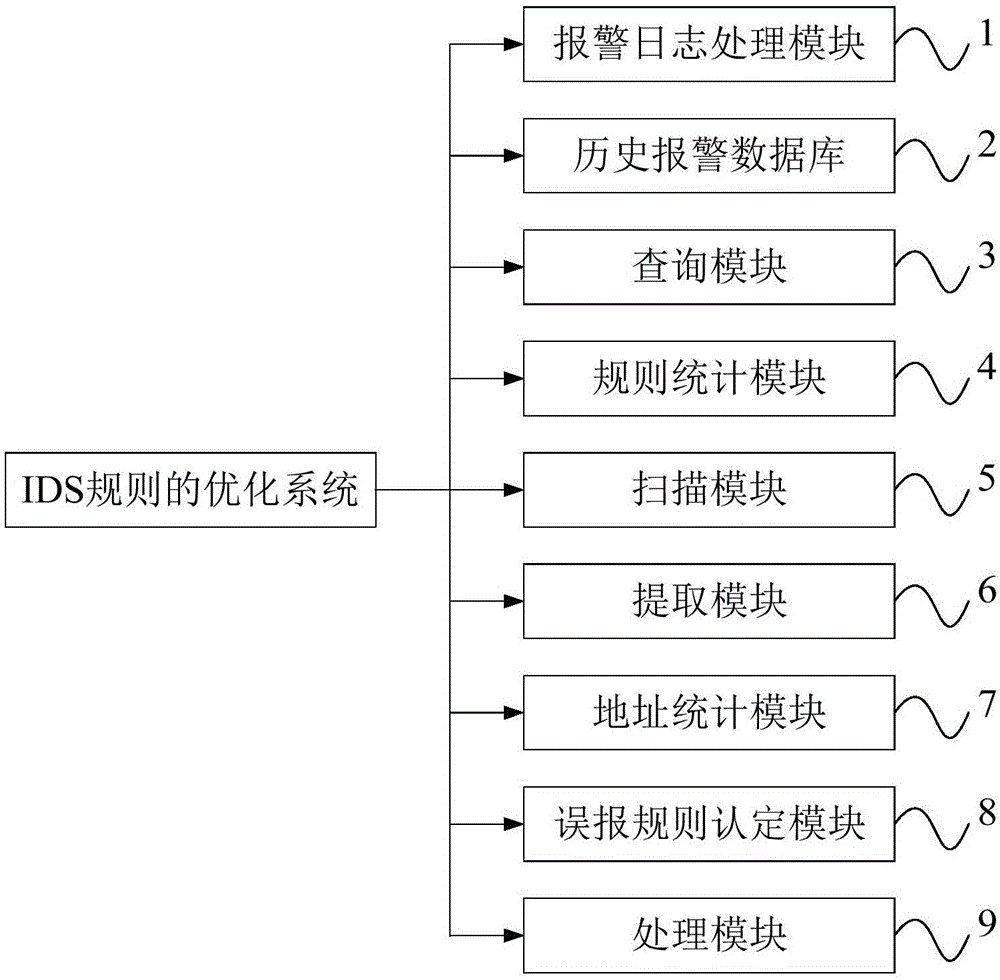
[0035] Such as figure 1 As shown, the optimization system of the IDS rule of the present invention includes an alarm log processing module 1, a historical alarm database 2, a query module 3, a rule statistics module 4, a scanning module 5, an extraction module 6, an address statistics module 7, and a false alarm rule identification module 8 and processing module 9.
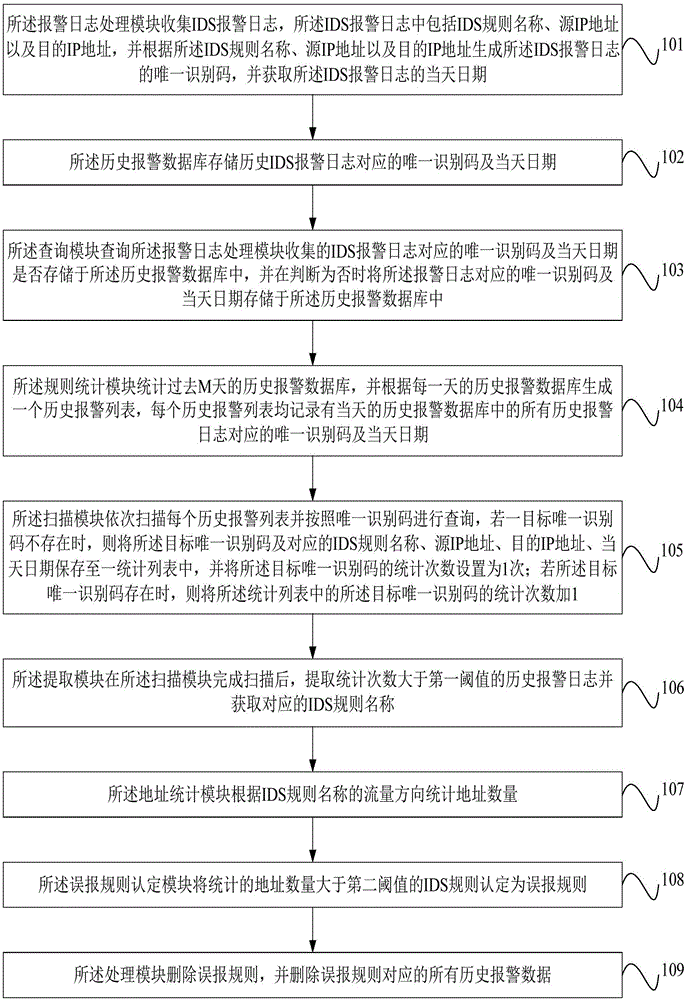
[0036] Wherein, the alarm log processing module 1 first collects the IDS alarm log, which includes the IDS rule name, source IP address and destination IP address, and generates an alarm log according to the IDS rule name, source IP address and destination IP address The unique identification code of the IDS alarm log, and obtain the date of the IDS alarm log;
[0037] Wherein, the unique identification code may specifically be an MD5 value;
[0038] The histor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com