Internet finance safety link realization method based on block chaining encryption technology
A security link and implementation method technology, applied in the field of Internet financial security link implementation based on block chain encryption technology, can solve the problem of ensuring high-level business security, unable to prevent misappropriation of distributed denial of service attacks, unable to prevent intrusive operations, etc. problem, to achieve the effect of ensuring link security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] All features disclosed in this specification, or steps in all methods or processes disclosed, may be combined in any manner, except for mutually exclusive features and / or steps.
[0032] Any feature disclosed in this specification (including any appended claims, abstract and drawings), unless expressly stated otherwise, may be replaced by alternative features which are equivalent or serve a similar purpose. That is, unless expressly stated otherwise, each feature is one example only of a series of equivalent or similar features.
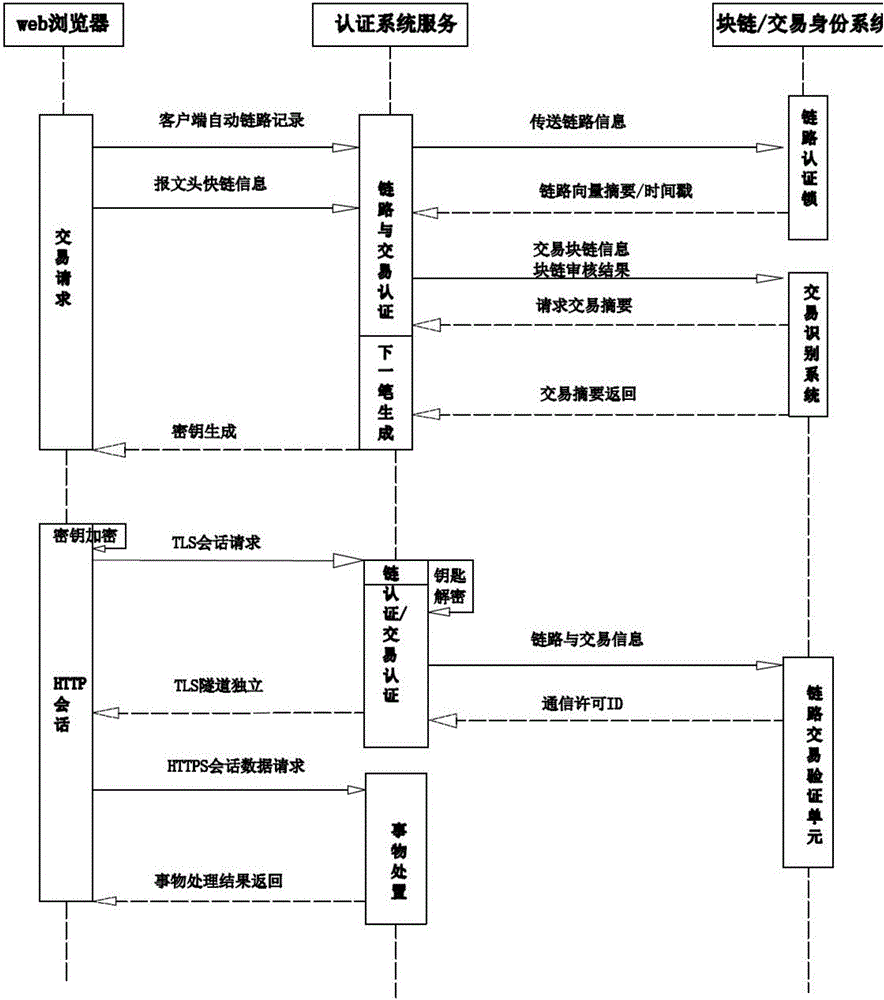
[0033] Such as figure 1 and figure 2 As shown, firstly, the encrypted key block of the message header generated by the independent authentication and authorization method is combined with the message body, and the message is sent to the next link;
[0034] Secondly, the HTTPS protocol processing of self-authentication credentials uses the message identity system and dynamic link vector with sequence check before the TLS link is established ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com