semiconductor device
A technology of semiconductors and programs, applied in computer security devices, instruments, computing, etc., can solve the problems of weak resistance of microcomputers and power supply noise.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0047]
[0048] Although a plurality of embodiments will be described below, the semiconductor devices to be described in the respective embodiments are respectively sold according to a new commercial sales model envisaged by the present inventors. Here, a description will first be made about a commercial sales model of a semiconductor device conceived by the present inventors.
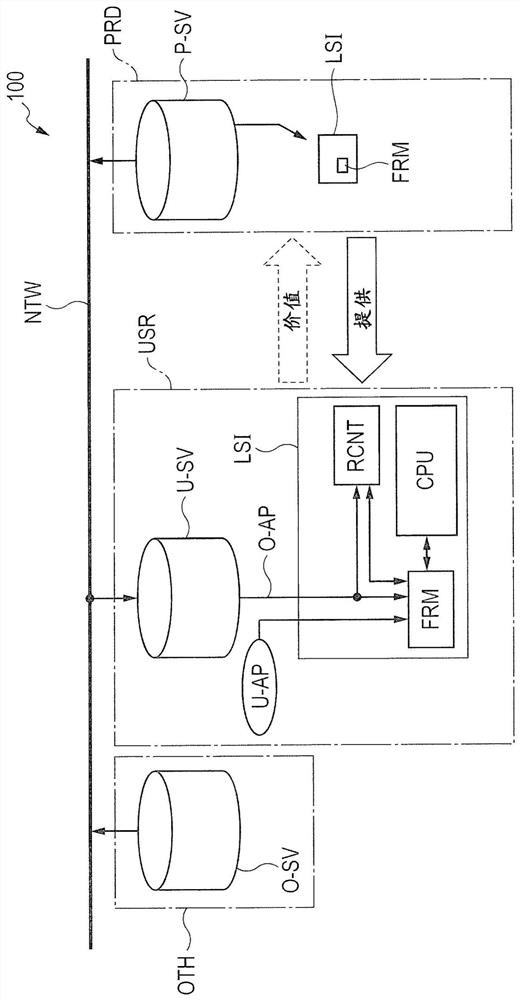
[0049] figure 1 is a system diagram showing the configuration of the semiconductor device commercial sales model according to the embodiment. In the same drawing, reference numeral 100 denotes a semiconductor device commercial sales model. Although not specifically shown, the semiconductor device business sales model 100 includes a provider PRD, a user USR, and a third-party OTH that provides programs.
[0050] The provider PRD sells the microcomputer LSI to the user USR. In the microcomputer LSI, a plurality of circuit blocks are formed in a single semiconductor chip by a known semiconductor ma...
no. 2 example
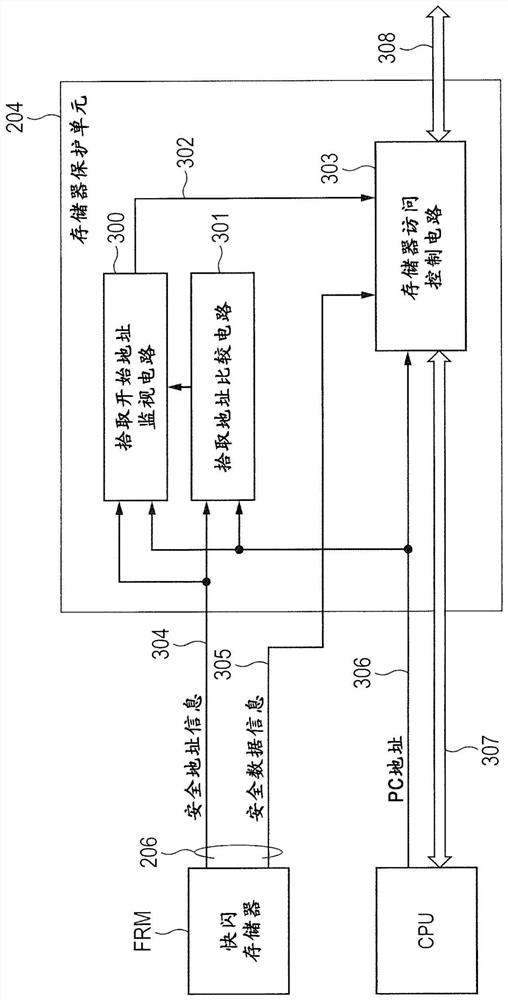
[0225] Figure 12 is a layout diagram showing the layout of data stored in the flash memory FRM according to the second embodiment.
[0226] The flash memory FRM according to the second embodiment is divided into a plurality of regions. In the area where the flash memory FRM is configured, Figure 12 The non-secure program area, the secure program area, and the protected information area are shown in . exist Figure 12 , the non-secure program area is denoted by reference numeral 1200 , the secure program area is denoted by reference numeral 1201 , and the protected information area is denoted by reference numeral 1202 .
[0227] In the second embodiment, the safety program whose safety should be ensured is stored in the safety program area 1201 , and the non-safety program is stored in the non-safety program area 1200 . The information of the protected safety program area 1201 is stored in the protected information area 1202 .
[0228] In the new semiconductor commercial...
no. 3 example
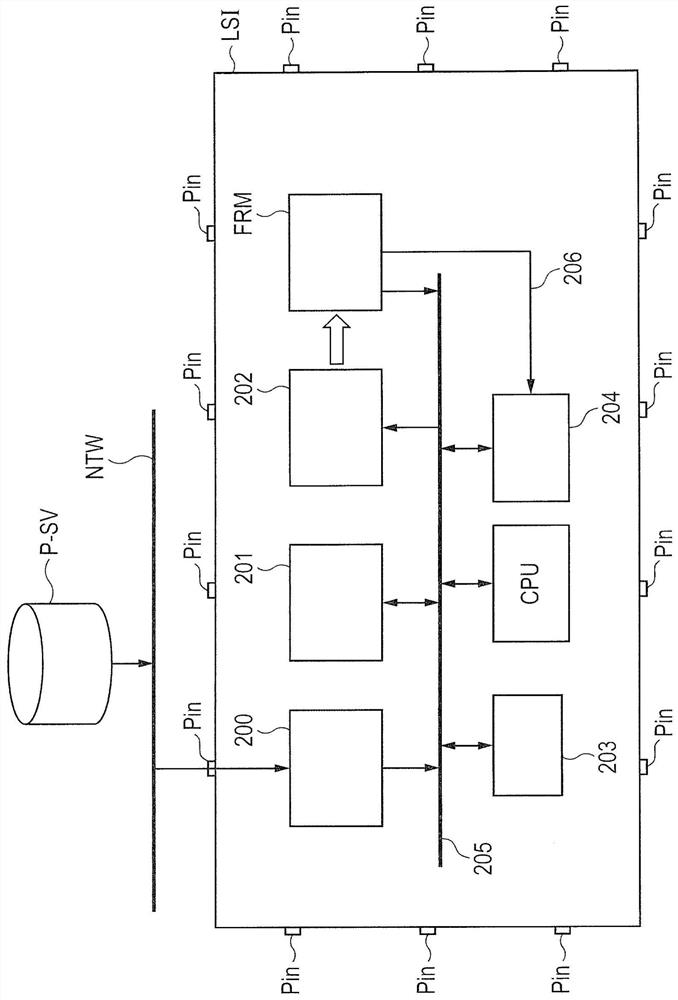
[0257] Figure 15 is a block diagram showing the configuration of the microcomputer according to the third embodiment. because Figure 15 The configuration of the microcomputer LSI shown is similar to figure 2 The microcomputers are shown, and the differences between them will be mainly described. In addition, in addition to the microcomputer LSI, such as figure 2 as in, in Figure 15 Even the server P-SV and the network NTW are shown.
[0258] In the new semiconductor commercial sales model, such as figure 1 As shown, the provider PRD pre-writes the security program such as RTOS into the flash memory FRM. A microcomputer LSI provided with a flash memory FRM in which an RTOS is written, a microprocessor CPU, and the like is sold from the provider PRD. The user USR writes the user program U-AP or the like generated by the user USR into the flash memory FRM in the purchased microcomputer LSI.
[0259] In this case, such as when the user USR performs version upgrade or...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com