Network intrusion detection method and device
A network intrusion detection and network data technology, applied in the field of information security, can solve the problem that the database cannot be updated in time and the detection accuracy, and achieve the effect of improving the accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] Embodiment 1 of the present invention discloses a network intrusion detection method, which is applied to a network intrusion detection device. The flow chart of the method is as follows figure 1 shown, including the following steps:
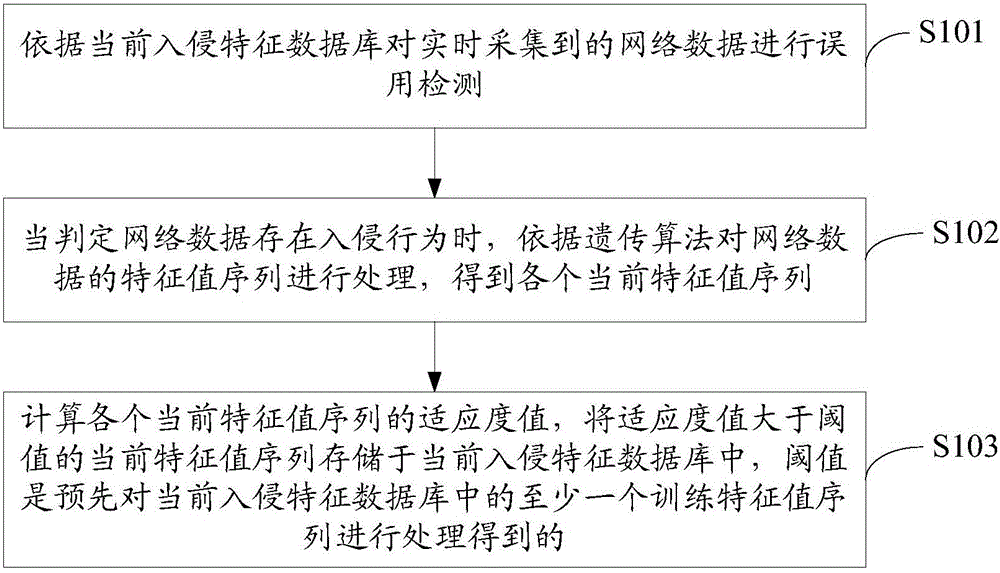
[0057] S101, performing misuse detection on the network data collected in real time according to the current intrusion feature database;
[0058] In the process of executing step S101, misuse detection is performed on the network data collected in real time, and whether there is an intrusion behavior in the network data is judged by matching the feature value sequence of the network data with the current intrusion feature database; wherein, the collected network data can be Include at least one preset parameter value. The preset parameter is the most obvious feature that changes in the network system when the attack occurs. The preset parameter includes but is not limited to IP source address, IP destination address, source port, destinat...
Embodiment 2
[0066] In combination with the network intrusion detection method disclosed in the first embodiment of the present invention and the accompanying figure 1 , Embodiment 2 of the present invention also provides a network intrusion detection method, the method flow chart is as follows figure 2 shown, including the following steps:
[0067] S101, performing misuse detection on the network data collected in real time according to the current intrusion feature database;
[0068] S102, when it is determined that there is an intrusion behavior in the network data, process the eigenvalue sequence of the network data according to the genetic algorithm to obtain each current eigenvalue sequence;
[0069] S103. Calculate the fitness value of each current feature value sequence, and store the current feature value sequence whose fitness value is greater than the threshold in the current intrusion feature database. The threshold is to pre-process at least one training feature value sequen...
Embodiment 3
[0075] In combination with the network intrusion detection method disclosed in Embodiment 1 and Embodiment 2 of the present invention, such as figure 1 and figure 2 In the shown step S102, the eigenvalue sequence of the network data is processed according to the genetic algorithm, and the specific execution process of each current eigenvalue sequence is obtained, as shown in image 3 shown, including the following steps:
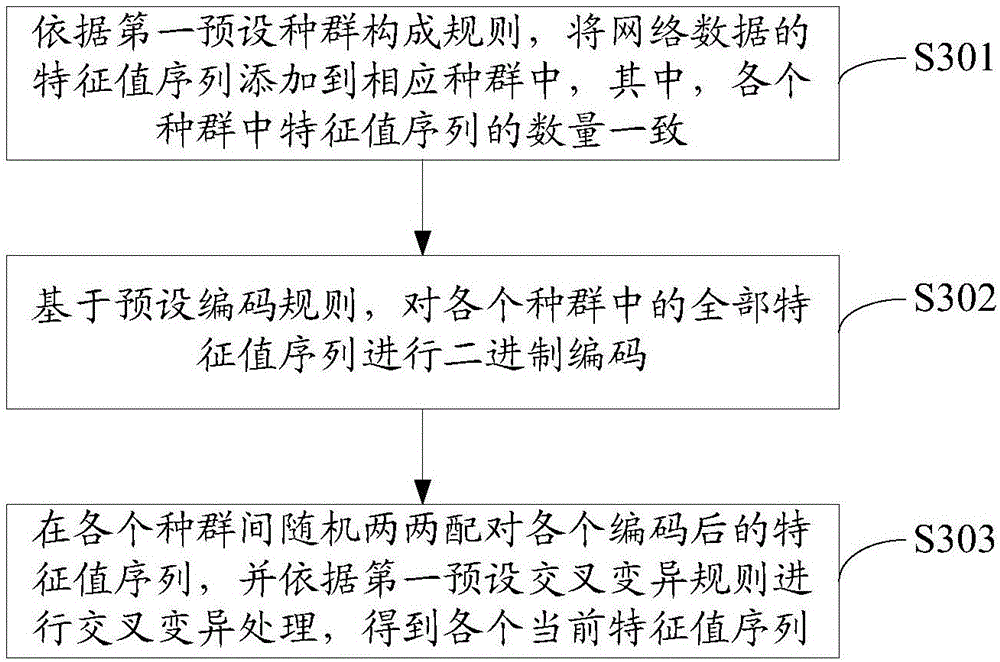
[0076] S301. Add the eigenvalue sequence of the network data to the corresponding population according to the first preset population composition rule, wherein the number of eigenvalue sequences in each population is the same;
[0077] In the process of executing step S301, according to the first preset population composition rule, for example, construct 2 populations, each population has 3 eigenvalue sequences, and sequentially add the eigenvalue sequences of the continuously collected network data to the corresponding in the population.
[0078] S302. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com