Network steal prevention method of wireless router, and wireless router
A technology of wireless router and anti-scrambling network, which is applied in the field of communication, can solve problems such as inconvenience, and achieve the effect of avoiding the harassment of repeatedly receiving authentication applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The wireless router anti-scraping network method and the wireless router provided by the present invention will be described in detail below in conjunction with the accompanying drawings.
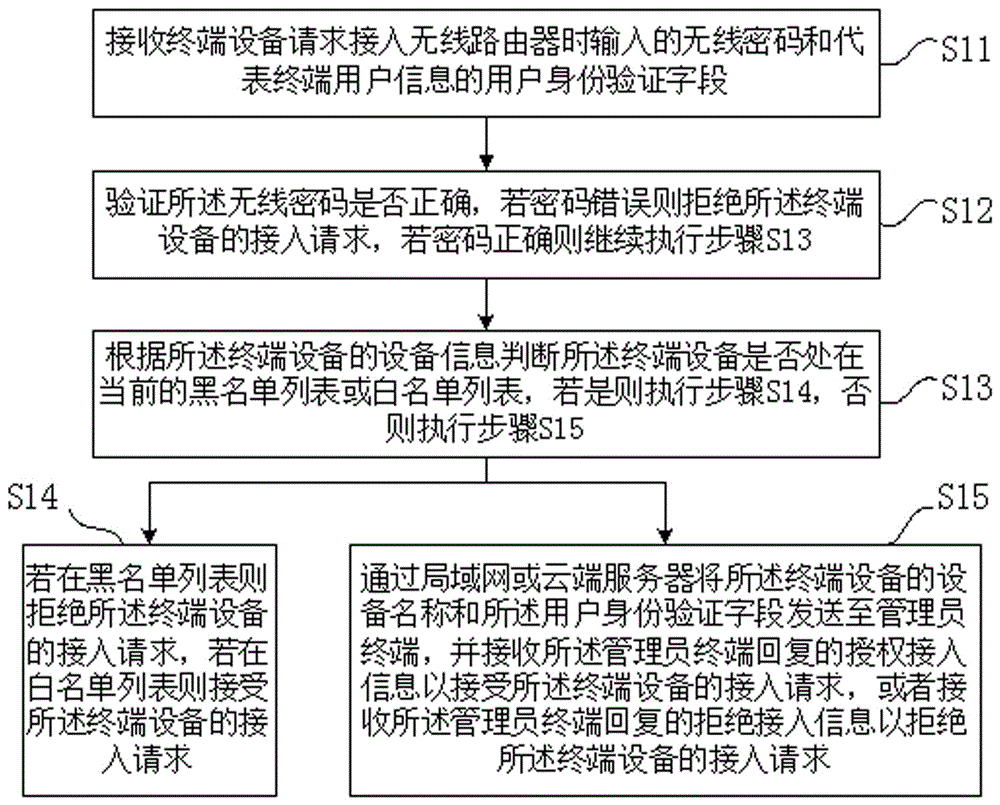
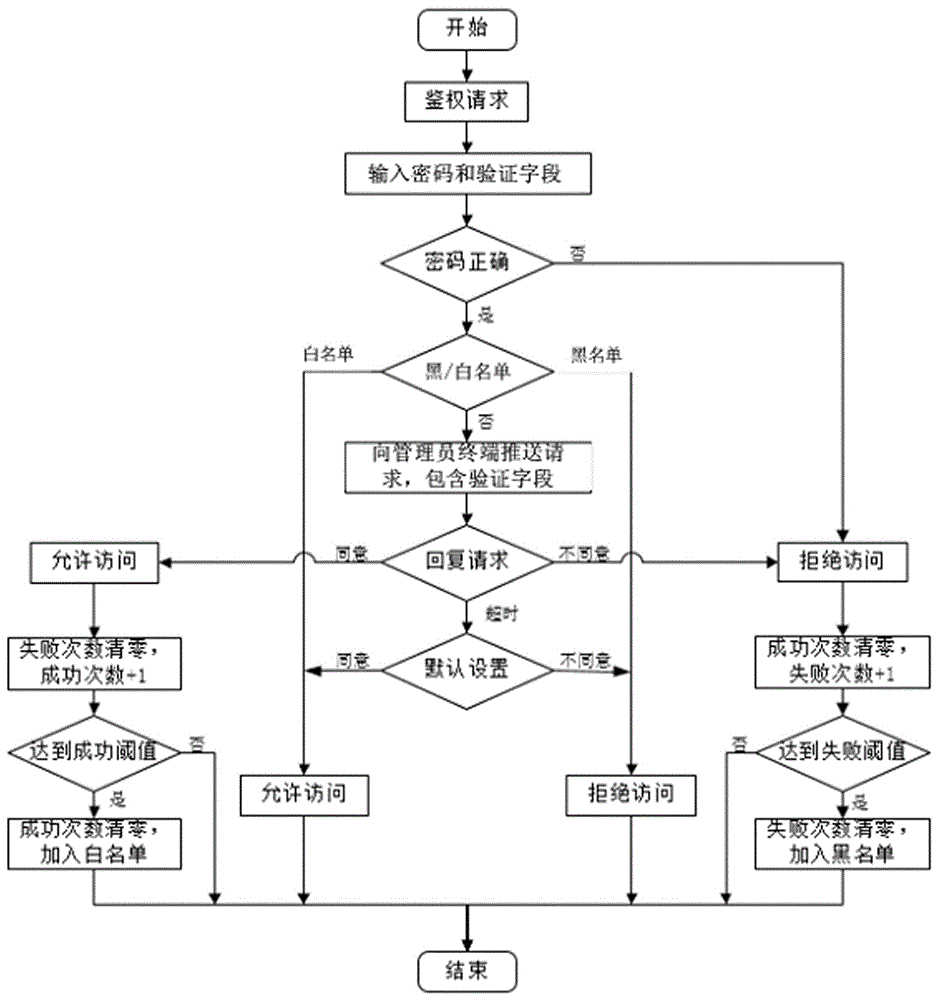
[0018] refer to figure 1 , a schematic flowchart of the wireless router anti-scrambling method according to the present invention. The method includes the following steps: S11: receiving the wireless password entered when the terminal device requests to access the wireless router and the user identity verification field representing terminal user information; S12: verifying whether the wireless password is correct, and rejecting the wireless password if the password is wrong. If the password is correct, continue to execute step S13; S13: judge whether the terminal device is in the current blacklist or whitelist according to the device information of the terminal device, and if so, execute step S14 , otherwise execute step S15; S14: If it is in the blacklist, reject the access reques...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com