Network security resource distributing method based on level bidding mechanism
A network security and resource allocation technology, applied in the field of network security resource allocation based on hierarchical bidding mechanism, can solve the problems of no research mechanism design, etc., to achieve the effect of ensuring maximum allocation, reducing network energy consumption, and improving utilization efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
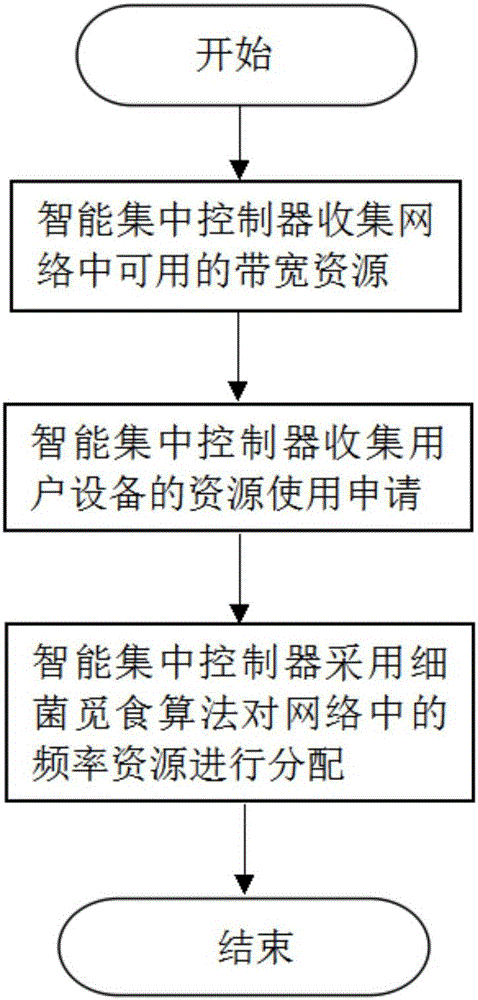
[0089] The present invention adopts a network security resource allocation method based on a hierarchical bidding mechanism, and the steps are as follows:
[0090] Step 1, the intelligent centralized controller collects available bandwidth resources in the network;
[0091] The available bandwidth resources in the collection network are the total traffic bandwidth of the radio frequency resources in the heterogeneous network, and the total traffic bandwidth of the radio frequency resources we use in this embodiment is 20M.
[0092] Step 2, the intelligent centralized controller collects the security resource usage application of the user equipment;
[0093] Submit an application to users who use wireless frequency bandwidth to collect relevant information about their Internet access.
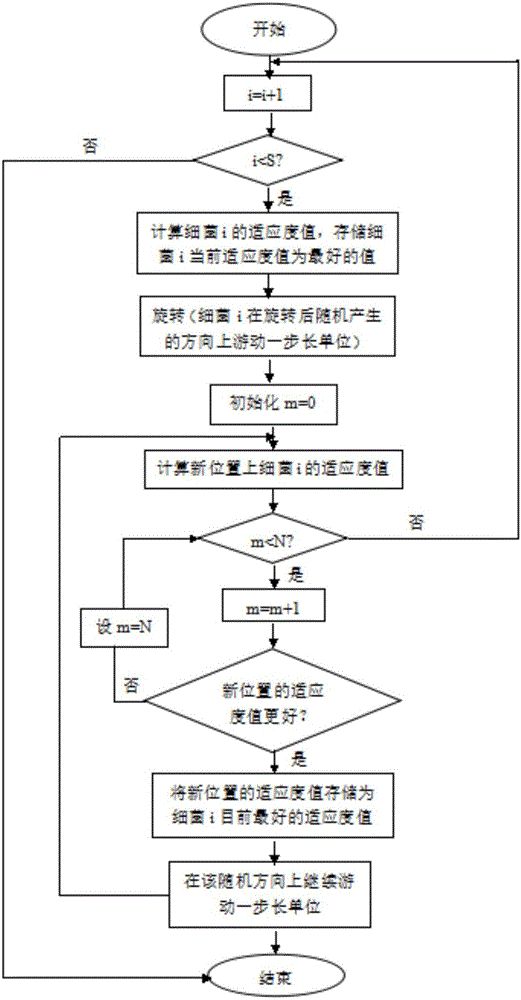
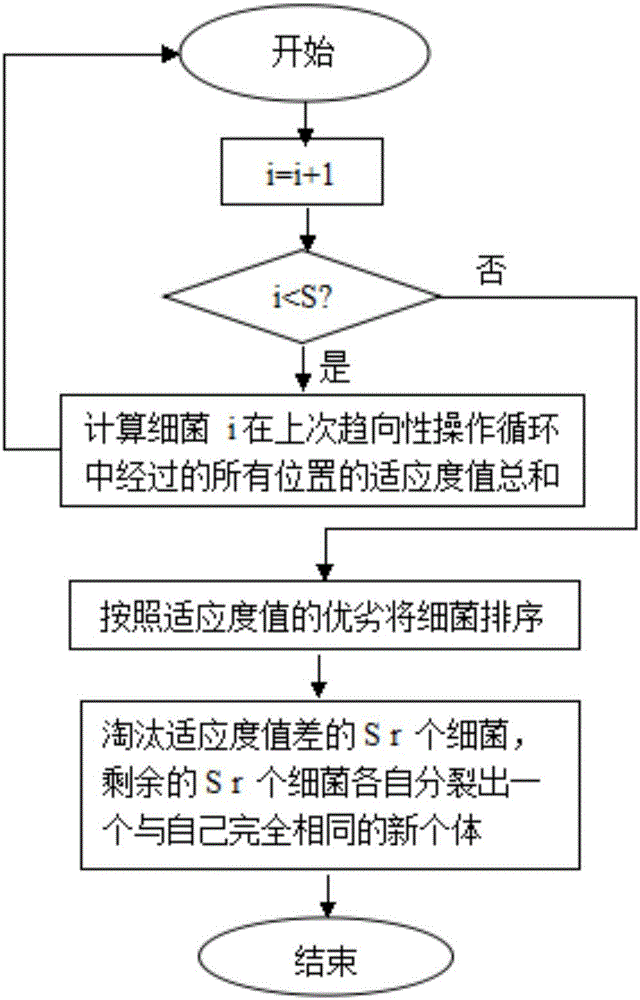
[0094] Step 3, the intelligent centralized controller uses the bacterial foraging optimization algorithm to allocate network security resources;
[0095] The size of the bacterial population i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com