Network data processing method, device and system
A technology for network data and processing methods, applied in the field of network security, can solve the problems of missing network data of hosts and servers, low data processing accuracy, etc., and achieve the effect of improving platform compatibility, saving transmission bandwidth, and data integrity and comprehensiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
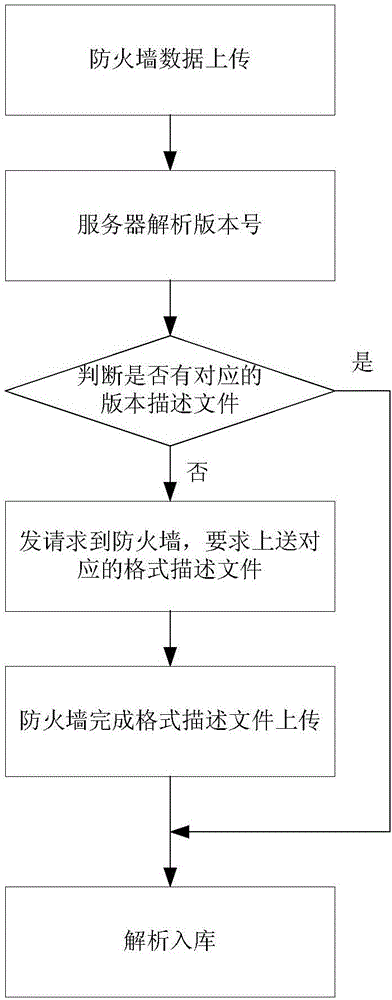
[0040] According to an embodiment of the present invention, an embodiment of a method for processing network data is provided. It should be noted that the steps shown in the flowcharts of the drawings can be executed in a computer system such as a set of computer-executable instructions, and , although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
[0041] figure 2 is a flowchart of a network data processing method according to an embodiment of the present invention, such as figure 2 As shown, the method includes the following steps:
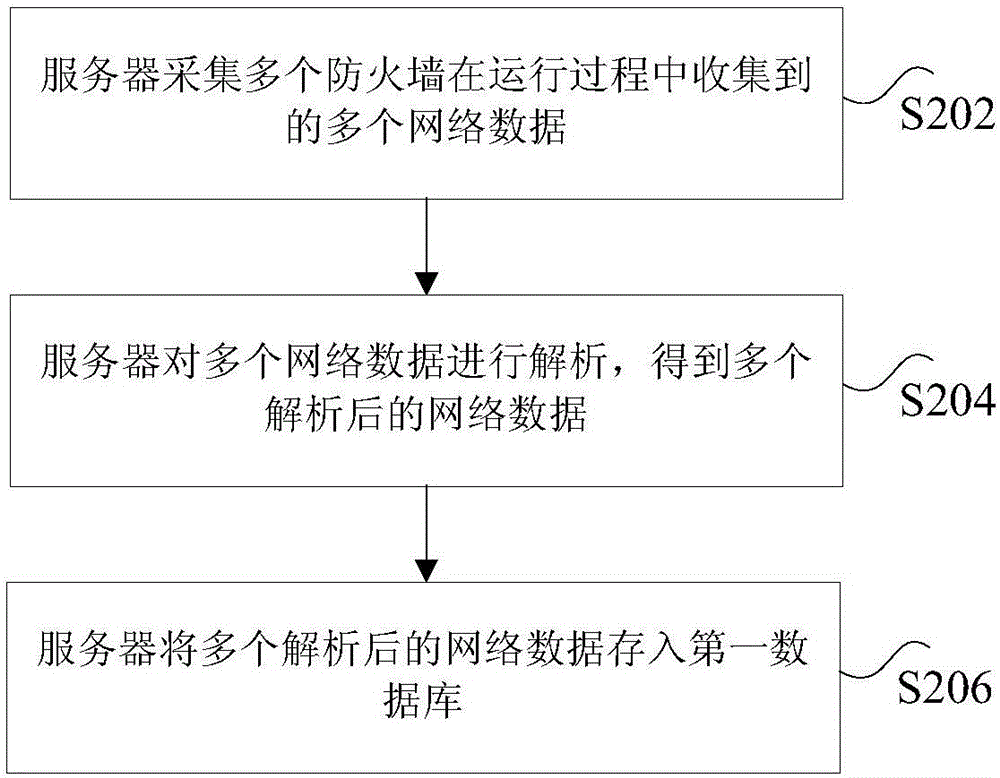
[0042]Step S202, the server collects multiple network data collected by multiple firewalls during operation, wherein multiple firewalls are deployed at multiple LAN exits, and each network data includes at least: the operating status of each firewall, traffic data, domain name information, suspicious files, and threat informat...
Embodiment 2
[0194] According to an embodiment of the present invention, an embodiment of an apparatus for processing network data is provided.
[0195] Figure 22 is a schematic diagram of a network data processing device according to an embodiment of the present invention, such as Figure 22 As shown, the device includes:
[0196] The collection module 221 is configured to collect multiple network data collected by multiple firewalls during operation, wherein multiple firewalls are deployed at multiple LAN exits, and each network data includes at least: the running status and flow data of each firewall , domain name information, suspicious files and threat information.
[0197] Specifically, the above-mentioned server may be a cloud server. Based on cloud computing technology, the available computing power, storage capacity and network capacity can achieve near-infinite scalability. Cloud computing technology and big data technology are closely integrated. Based on the storage and com...
Embodiment 3
[0209] According to an embodiment of the present invention, an embodiment of a network data processing system is provided.
[0210] Figure 23 is a schematic diagram of a network data processing system according to an embodiment of the present invention, such as Figure 23 As shown, the system includes:
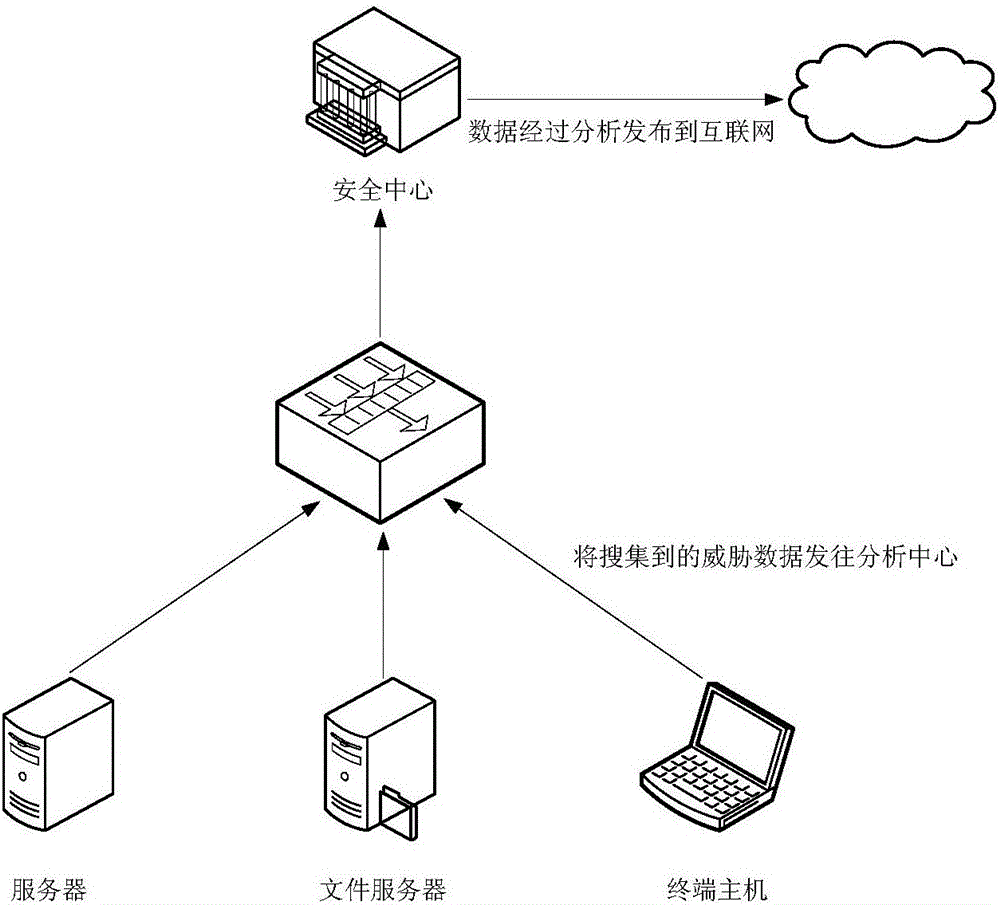
[0211] Multiple firewalls 231 are deployed at multiple LAN exits to collect multiple network data during operation, wherein each network data includes at least: the running status of each firewall, traffic data, domain name information, suspicious files and threats information.
[0212] Specifically, the above-mentioned local area network can be the network exit of a company or institution, and the firewall deployed at the local area network exit can provide security protection for the data assets of the intranet, and the hosts and servers of the intranet and the interconnected network data all pass through the firewall, so , the firewall can collect more comprehensive and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com