User authority authentication method and apparatus
A technology of user authority and verification method, applied in the Internet field, can solve the problems of easy omission of authority judgment and a large amount of user authority verification code, so as to avoid omission of authority judgment, reduce the amount of code, and improve the accuracy and execution efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
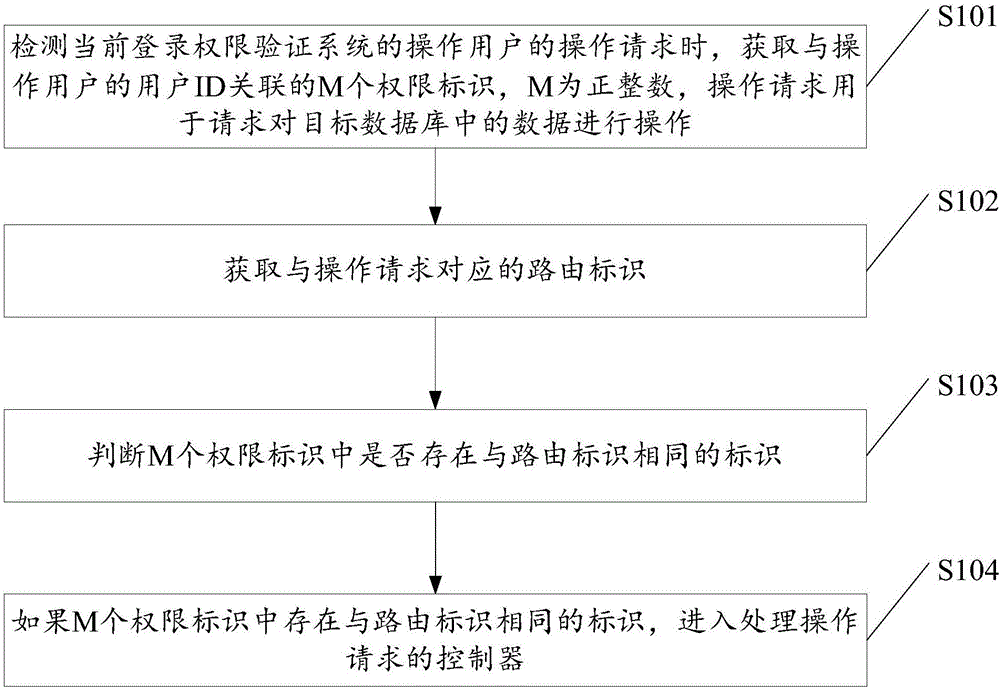
[0114] For the operation request is a view request, assuming that Wang Wu has logged in, and Wang Wu’s view request is detected, and he enters the URL to view the product, such as http: / / www.example.com / product / view / 1, and performs the following permission judgments in turn step:
[0115] 1. Obtained Wangwu user ID is 3;
[0116] 2. Get the role ID 3 associated with the user ID 3 from the preset user role association table;
[0117] 3. Obtain the permission ID 1 associated with the role ID 3 from the preset role permission association table;
[0118] 4. Obtain the permission ID of 1 from the preset permission table as App\Http\Controllers\ProductController@view;
[0119] 5. Obtain the routing ID corresponding to the viewing request: App\Http\Controllers\ProductController@view, which is the same as the authorization ID obtained in the previous step, and enter the controller that processes the viewing request. There is no custom permission judgment unit in the controller used...
Embodiment 2
[0121] For the operation request is a view request, assuming that Wang Wu has logged in and entered the website for editing the product, such as http: / / www.example.com / product / edit / 1, the following permission judgment steps are performed in sequence:
[0122] 1. Obtained Wangwu user ID is 3;
[0123] 2. Get the role ID 3 associated with the user ID 3 from the preset user role association table;
[0124] 3. Obtain the permission ID 1 associated with the role ID 3 from the preset role permission association table;
[0125] 4. Obtain the permission ID of 1 from the preset permission table as App\Http\Controllers\ProductController@view;
[0126] 5. Obtain the routing ID corresponding to the editing request: App\Http\Controllers\ProductController@edit, compare it with the permission ID obtained in the previous step, if it is different, the permission authentication will fail, and the editing request will not be processed.
Embodiment 3
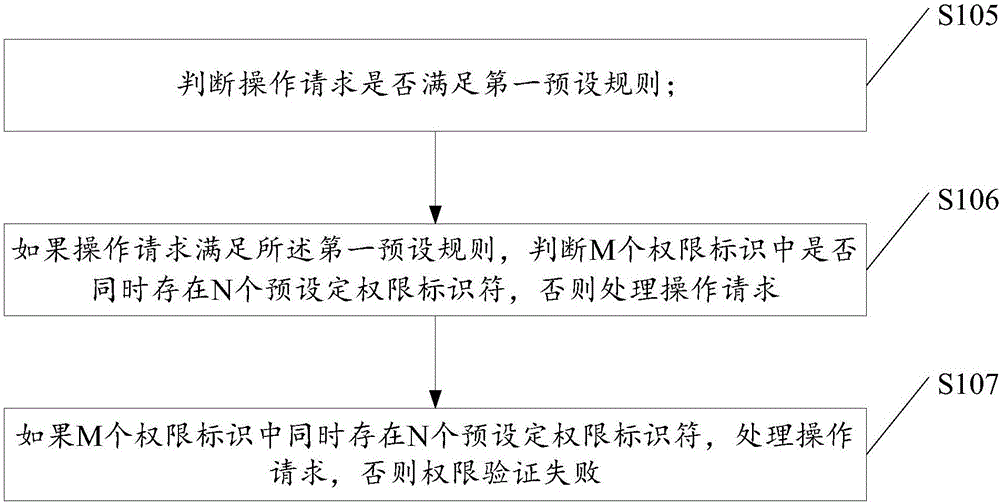
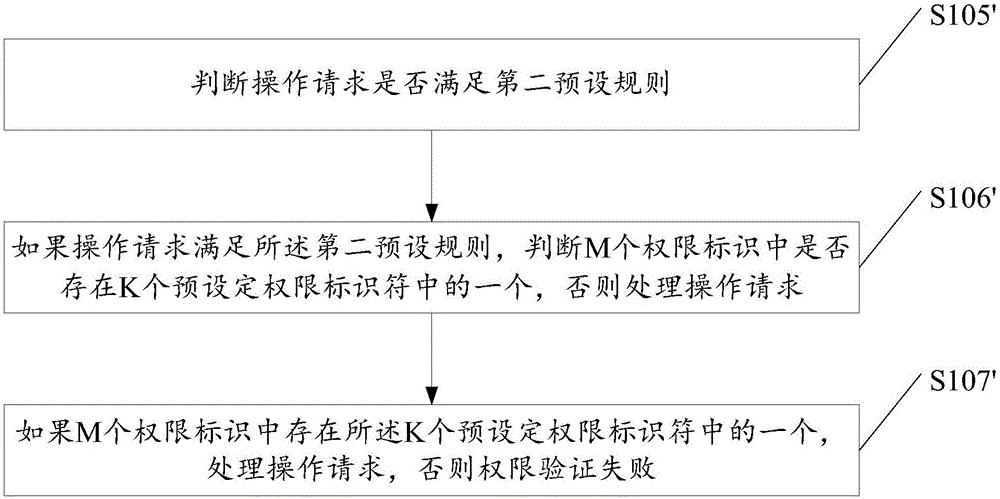
[0128] If the operation request is a delete request, add a custom permission judgment unit in the controller of the operation request for deleting a product. If the price is greater than 10,000, then judge whether there is a custom_high_price_product_delete permission identifier among the obtained M permission identifiers.
[0129] Specifically, the steps to determine the permissions of Zhang San and Li Si are as follows:
[0130] Assuming that Zhang San has logged in and entered the website to delete the product, such as http: / / www.example.com / product / delete / 1, the steps to determine the authority are as follows:
[0131] 1. The user ID of Zhang San is 1.
[0132] 2. Obtain the role ID associated with user ID 1 from the default user role association table.
[0133] 3. Obtain the permission IDs associated with role ID 1 from the preset role permission association table as 1, 2, 3, and 4.
[0134] 4. Obtained from the preset permission surface, the permission IDs of 1, 2, 3 a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com