A secure and verifiable method for continuous data collection in sensor networks
A sensor network and data collection technology, applied in security devices, secure communication devices, machine-to-machine/machine-type communication services, etc., can solve problems such as sensor node discarding or repeated transmission attacks difficult to monitor, and achieve energy saving in communication , high data privacy, and the effect of reducing data traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
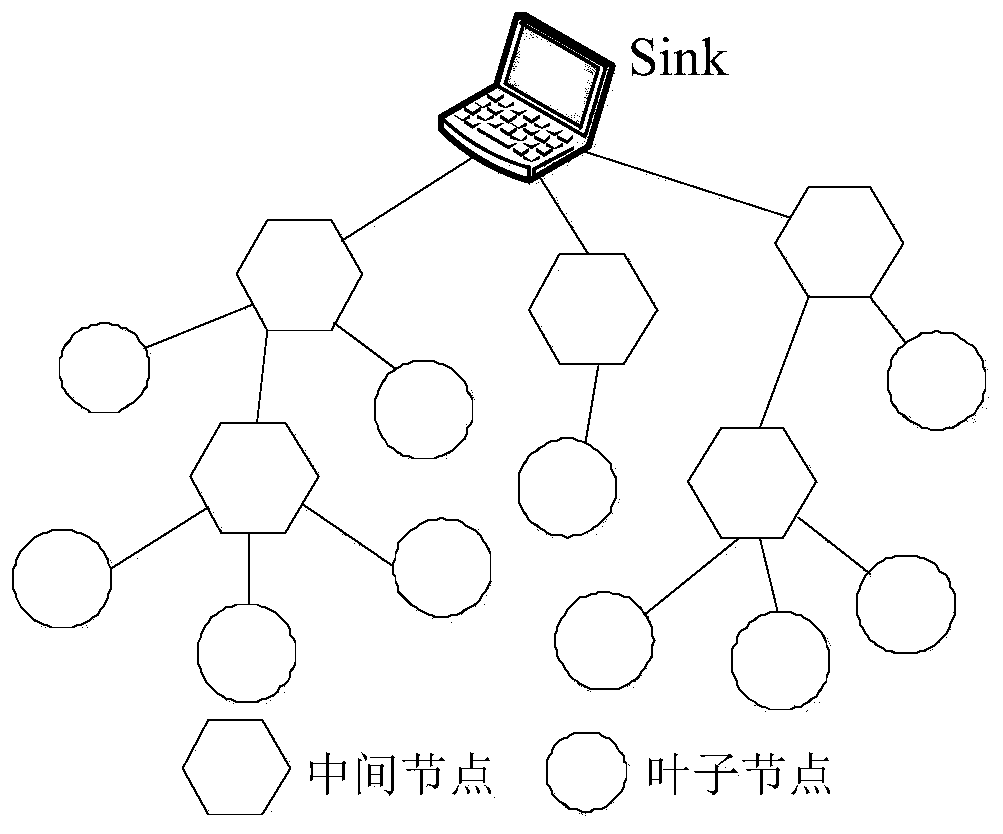
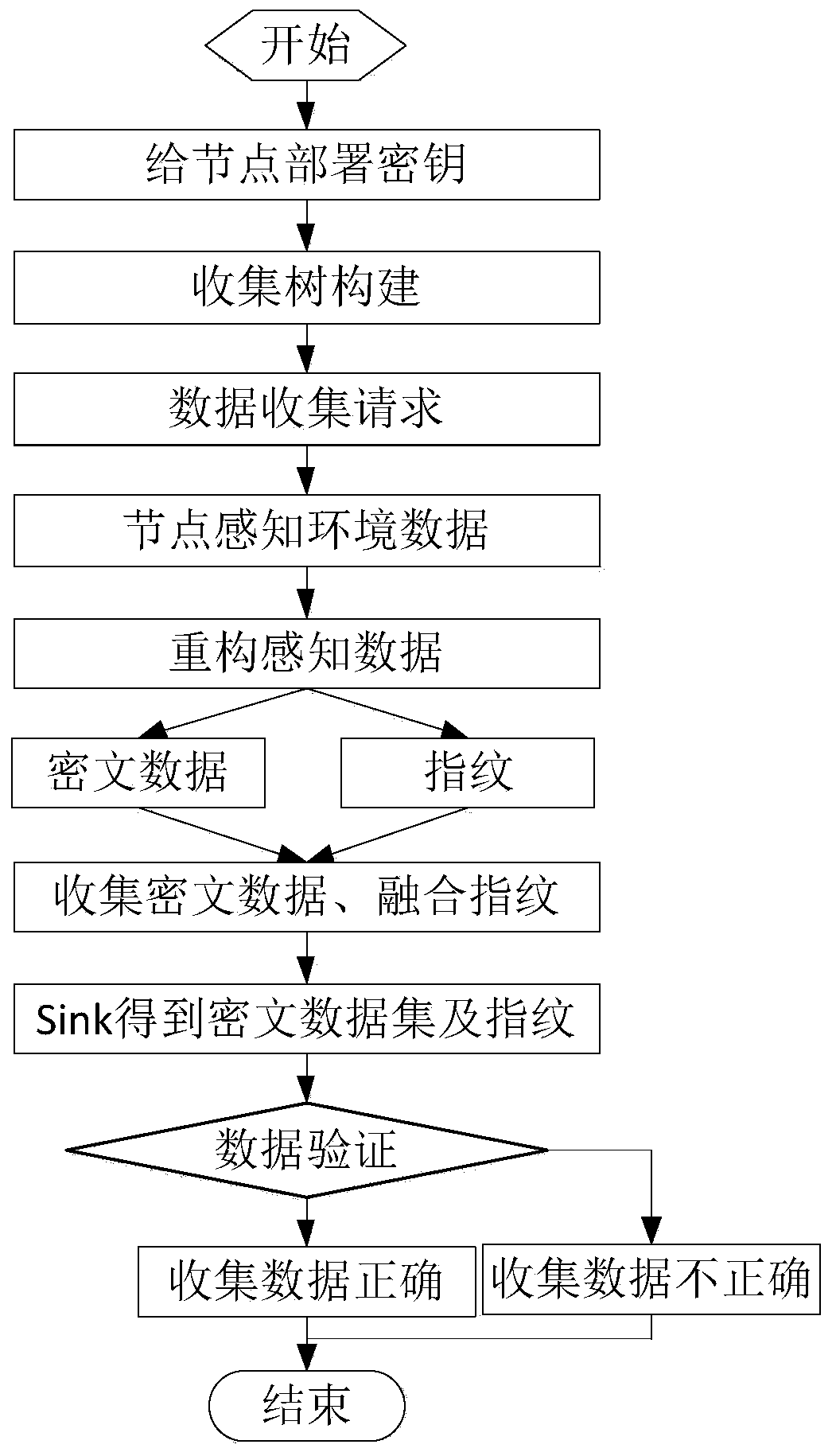
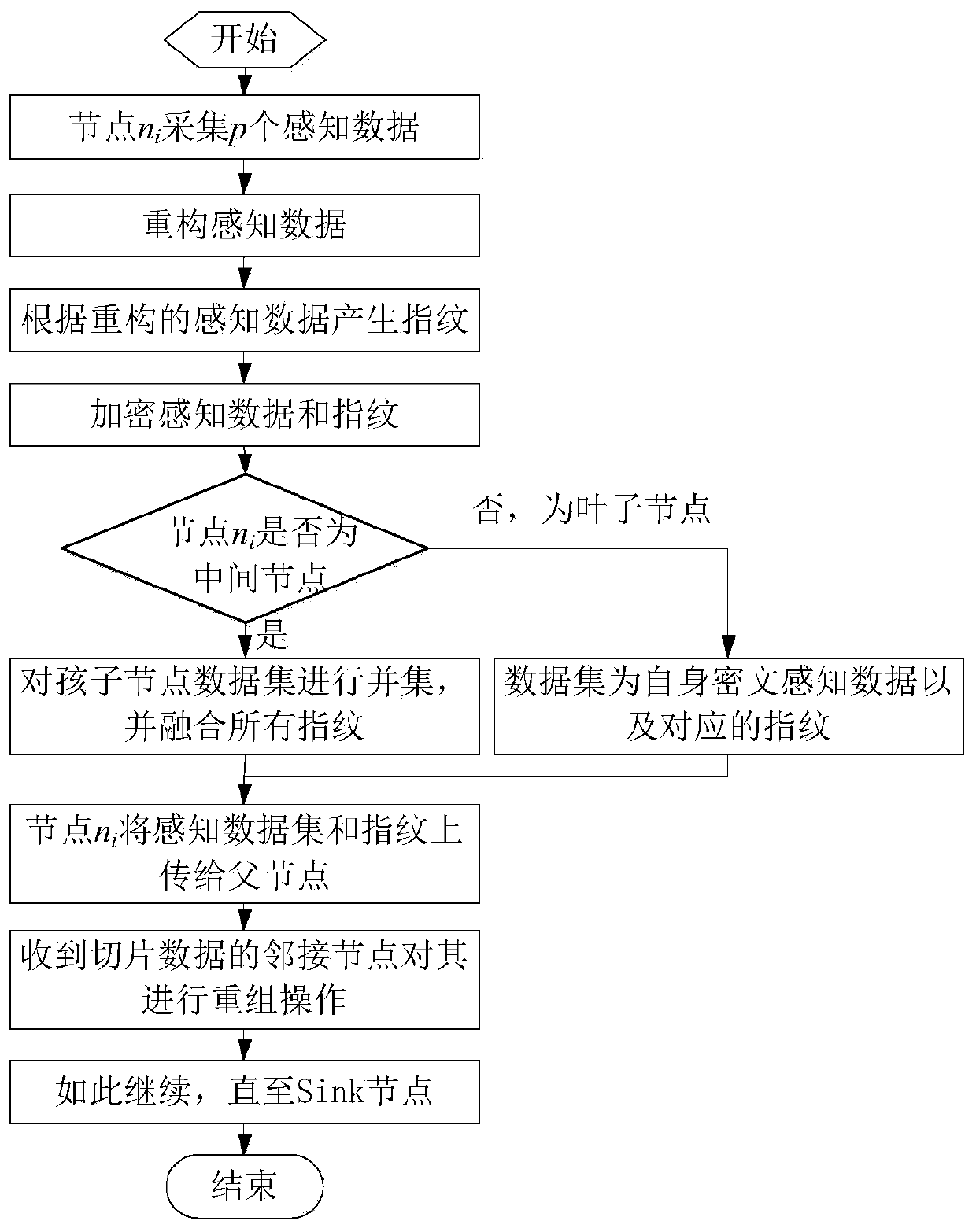
[0043] The present invention utilizes the time correlation of perceived data, uses basic data and difference data chains to represent multiple data in one cycle, and encrypts the data and transmits them to the Sink node, effectively reducing data while ensuring data privacy traffic. At the same time, the Sink node uses the sensor node to send "fingerprint" to verify the sensing data. Since the number of "fingerprint" is much shorter than the number of sensing data, this method realizes the integrity of the sensing data while increasing a small amount of traffic. verify.
[0044] That is to ensure the security of data through encryption technology, and use time correlation to reconstruct the sensing data in a cycle, effectively reducing the data communication traffic; sensor nodes generate "fingerprints" of sensing data, so that Sink can collect Since the number of "fingerprint" digits is much shorter than the number of perception data and can be fused, the cost of "fingerprin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com