Session management method and server
A session management and server technology, which is applied in the field of communication, can solve problems such as unfavorable normal processing of other businesses, increase of server processing load, large storage space, etc., and achieve the effect of improving management quality, reducing processing load, and improving processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
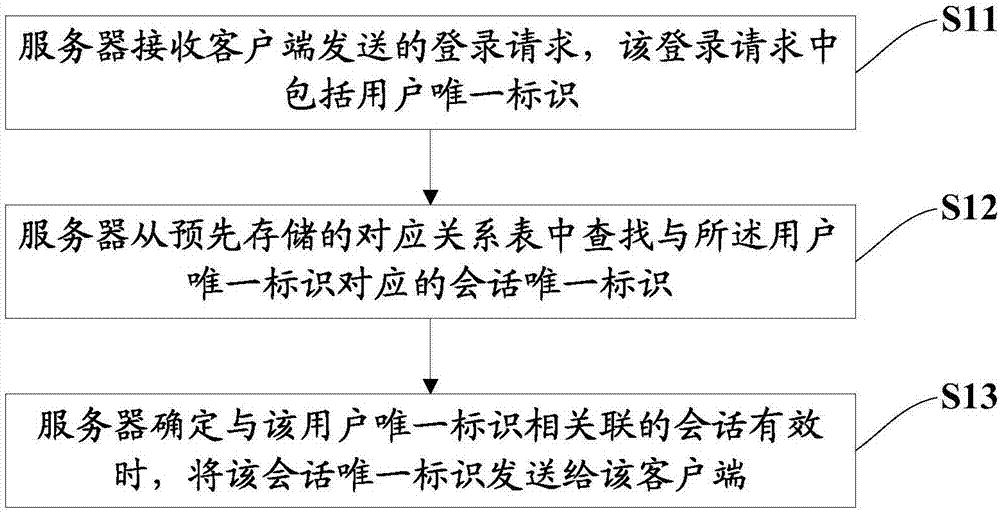
[0040] refer to figure 1 , figure 1 It is a schematic flowchart of the session management method provided in the first embodiment of the present invention, including the following steps:
[0041] S11: The server receives the login request sent by the client, and the login request includes a user ID.
[0042]In this embodiment, the server may specifically be an application server of a shopping mall, an application server of a bank, an application server of an airline, and the like. The server can accept the login request sent by the client. It should be noted that the login request includes the user ID, such as the account ID registered by the user on the website, and the login request also includes the user password of the user ID. Whether this login is legal can be verified according to the user ID and the corresponding user password, that is, whether the account number and password of the login are correct, so as to ensure that the login is initiated by the relevant user. ...
no. 2 example
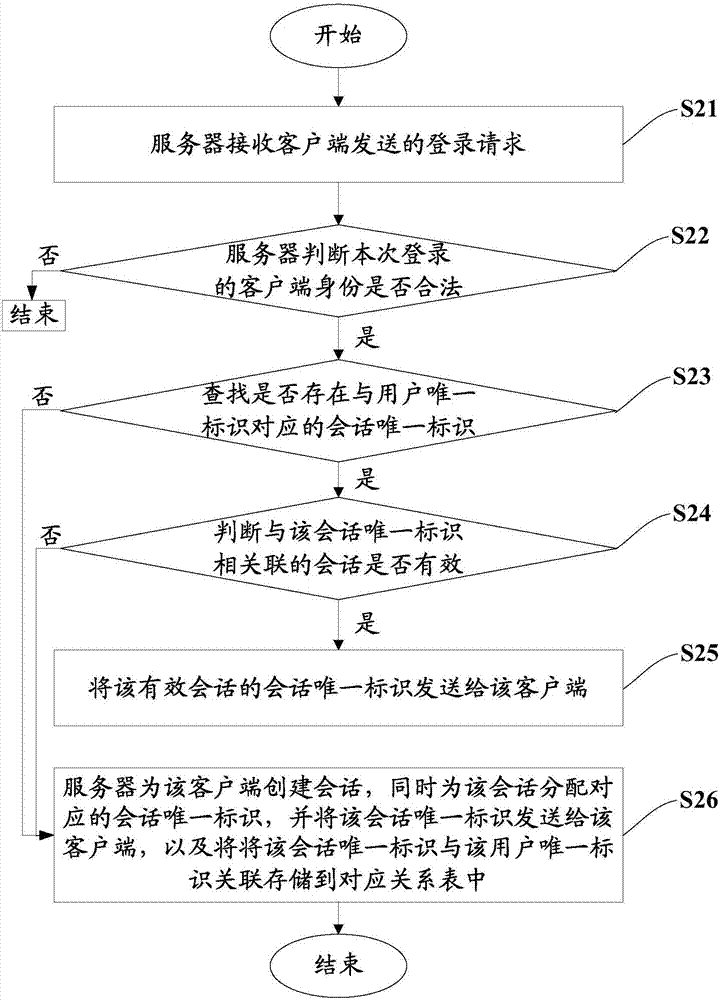
[0077] This embodiment provides a session management method on the basis of the first embodiment, please refer to figure 2 , figure 2 It is a schematic flowchart of a session management method provided in the second embodiment of the present invention, including:
[0078] S21: The server receives the login request sent by the client.
[0079] Here, at least the user ID is included in the login request.
[0080] S22: The server judges whether the identity of the client logging in this time is legal, if yes, go to step S23, if not, end.
[0081]The login request also includes the user password of the user ID. The server can verify whether the login is legal according to the user ID and the corresponding user password, that is, verify whether the account number and password of the login are correct, so as to ensure that the login is done by associated user-initiated. The verification method is not limited here, and may be any existing verification method.
[0082] S23: The...
no. 3 example
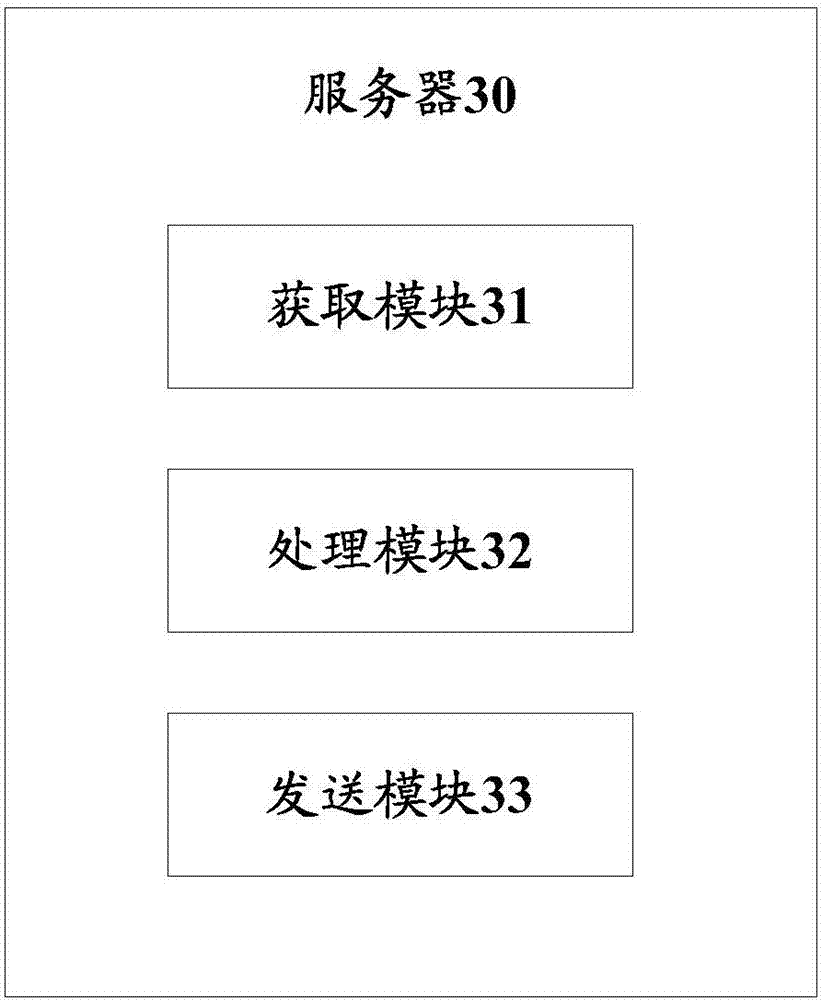
[0092] This embodiment provides a server, please refer to image 3 , image 3 It is a schematic structural diagram of a server provided by the third embodiment of the present invention, the server 30 includes an acquisition module 31, a processing module 32, and a sending module 33:
[0093] Wherein, the acquiring module 31 is configured to acquire the user ID included in the login request sent by the client.
[0094] The processing module 32 is configured to search for a session ID corresponding to the user ID from a pre-stored correspondence table. The processing module 32 is used to search the session ID corresponding to the user ID from the correspondence table according to the user ID obtained by the obtaining module 31 . The correspondence table can be stored in the memory of the server itself, or can be stored through other storage devices, including but not limited to storage in the session server, database, etc., regardless of whether the correspondence table is sto...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com