Risk evaluation method and system
A technology of risk assessment and risk assessment model, applied in instruments, complex mathematical operations, finance, etc., can solve problems such as insufficient mining and utilization of data, weak variables cannot be selected into models, etc., to achieve comprehensive risk assessment factors and improve risk assessment. Effects, model results Objective and accurate effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
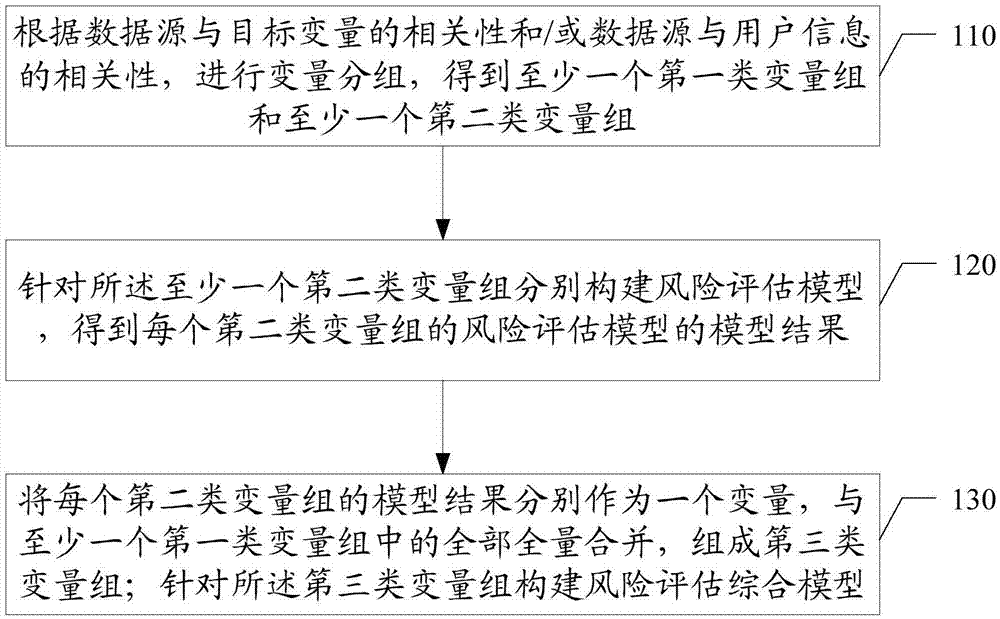
[0048] Please refer to figure 1 , the first embodiment of the present invention provides a risk assessment method, which may include:
[0049] 110. Perform variable grouping according to the correlation between the data source and the target variable and / or the correlation between the data source and user information, to obtain at least one variable group of the first type and at least one variable group of the second type.
[0050] With the rapid development of the Internet, more and more information and data are available, and the data sources used in risk assessment methods are also becoming more and more extensive. Some of them have a stronger correlation with credit risk, while others have a weaker correlation. In this paper, the variables are first grouped according to the data source, and the variables of the same source are regarded as a variable group. For example, the three types of variables from payment, instant messaging, and social networking can be regarded as t...
Embodiment 2
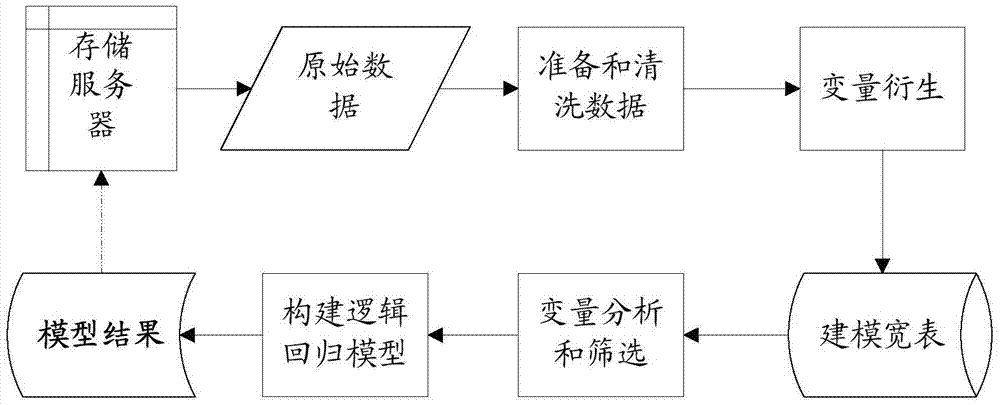
[0107] (Embodiment 2) In order to better implement the above-mentioned solution of the embodiment of the present invention, related devices for coordinating the implementation of the above-mentioned solution are also provided below.
[0108] Please refer to Figure 4 , the embodiment of the present invention provides a risk assessment system 400, which may include:
[0109] A preprocessing module 410, configured to group variables according to the correlation between the data source and the target variable and / or the correlation between the data source and user information, to obtain at least one variable group of the first type and at least one variable group of the second type;
[0110] The first construction module 420 is configured to respectively construct a risk assessment model for the at least one second-type variable group, and respectively obtain the model results of the risk assessment model of each second-type variable group;
[0111] The variable combination modu...
Embodiment 3
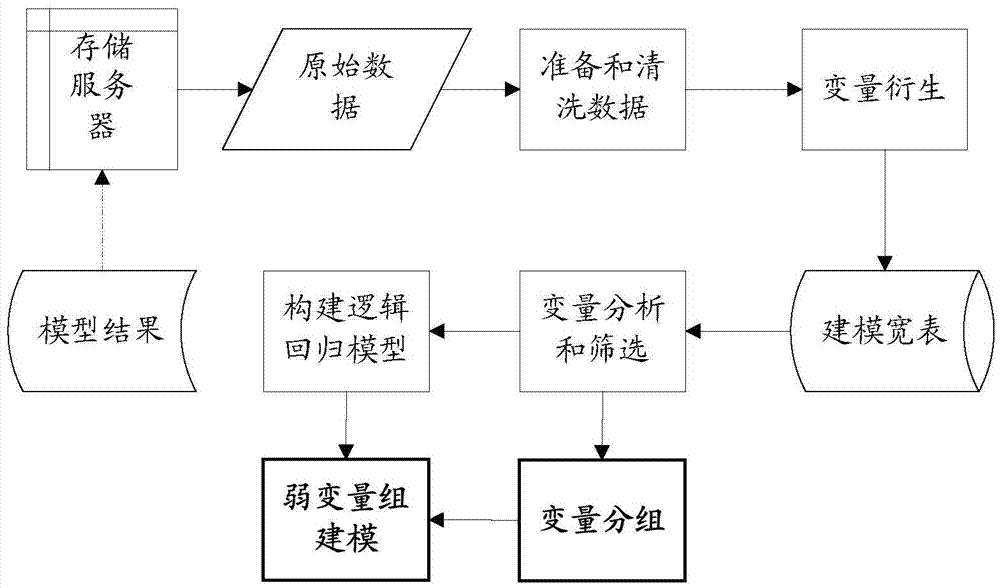
[0128] (Embodiment 3) The embodiment of the present invention also provides a computer storage medium, the computer storage medium can store a program, and when the program is executed by a computer device including a processor, the computer device executes the above-mentioned method embodiment Some or all steps of the risk assessment method described in .
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com