Domain name hijacking detection and linkage processing method and domain name hijacking detection and linkage processing system
A domain name hijacking and disposal method technology, applied in the network field, can solve the problems of high false positive rate, lack of linkage disposal methods, complex address database maintenance, etc., to reduce false positives, optimize domain name hijacking determination technology, and improve emergency response efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
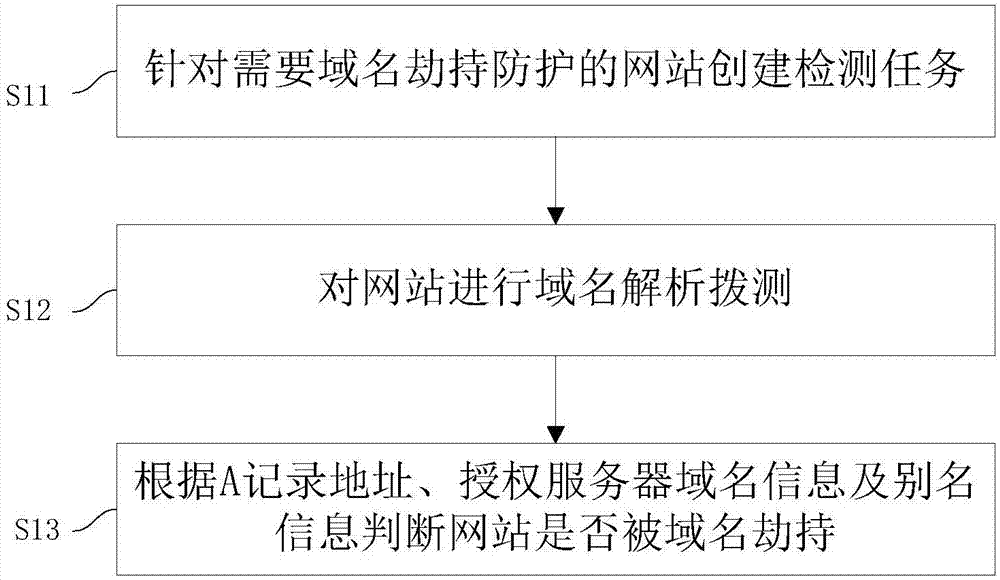
[0055] This embodiment provides a domain name hijacking detection and linkage processing method, such as figure 1 shown, including steps:
[0056] S11: Create detection tasks for websites that require domain name hijacking protection;
[0057] S12: Perform domain name resolution and dial-up test on the website;
[0058] S13: Determine whether the website is hijacked by the domain name according to the A record address, the authorization server domain name information and the alias information.
[0059] Domain name hijacking refers to intercepting domain name resolution requests within the scope of the hijacked network, analyzing the requested domain name, and releasing requests outside the scope of review, otherwise returning a false IP address or doing nothing to make the request unresponsive, the effect is to Specific networks do not respond or visit fake URLs.
[0060] The prior art has disadvantages such as complicated address database maintenance and high false positiv...
Embodiment 2
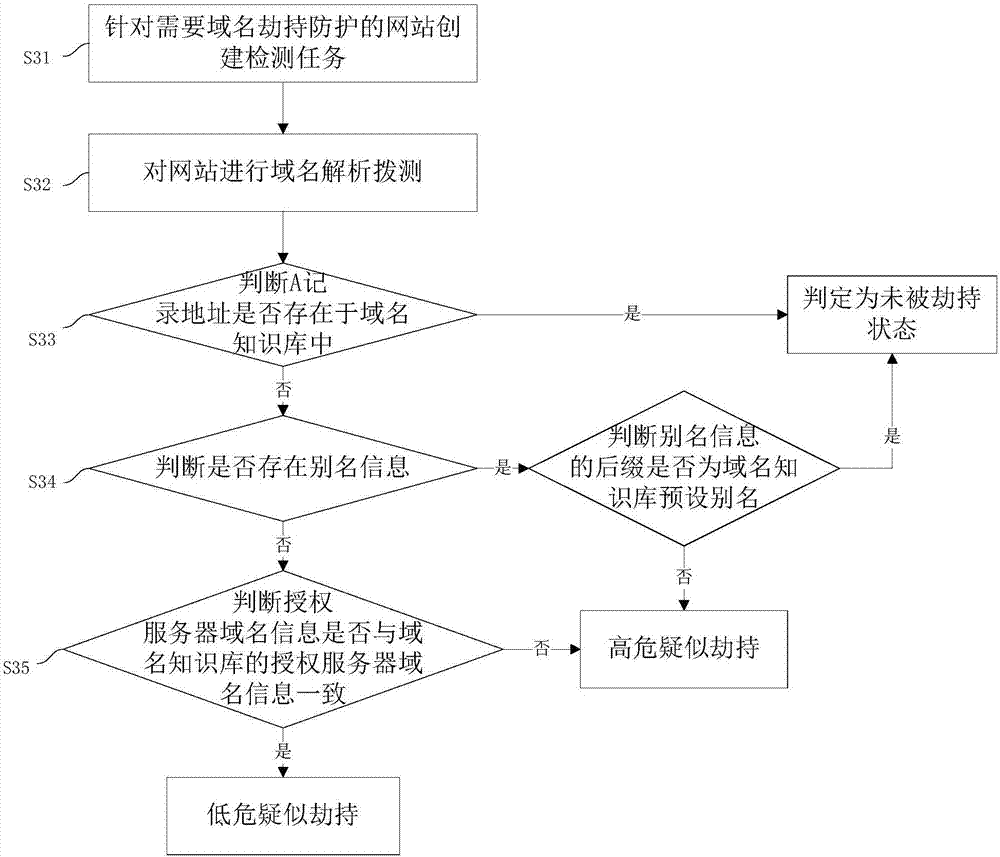
[0089] This embodiment provides a domain name hijacking detection and linkage processing method, such as image 3 shown, including steps:
[0090] S31: Create a detection task for a website that requires domain name hijacking protection;
[0091] S32: Perform domain name resolution and dial-up test on the website;
[0092] S33: Determine whether the A record address exists in the domain name knowledge base, if so, determine that it is not hijacked;
[0093] S34: If the A record address does not exist in the domain name knowledge base, determine whether there is alias information, if yes, determine whether the suffix of the alias information is a preset alias in the domain name knowledge base, if so, determine that it is not hijacked, otherwise, determine that it is high risk suspected hijacking;
[0094] S35: If there is no alias information, determine whether the domain name information of the authorized server is consistent with the domain name information of the authoriz...
Embodiment 3
[0118] This embodiment provides a domain name hijacking detection and linkage processing method, such as Figure 5 shown, including steps:
[0119] S51: Create a detection task for a website that requires domain name hijacking protection;
[0120] S52: Perform domain name resolution dial-up test on the website;
[0121] S53: Determine whether the A record address exists in the domain name knowledge base, if so, determine that it is not hijacked;
[0122] S54: If the A record address does not exist in the domain name knowledge base, determine whether there is alias information, if yes, determine whether the suffix of the alias information is a default alias in the domain name knowledge base, if so, determine that it is not hijacked, otherwise, determine that it is high risk suspected hijacking;
[0123] S55: If there is no alias information, determine whether the domain name information of the authorized server is consistent with the domain name information of the authorized s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com