Network application login method and system
A network application and application server technology, applied in the transmission system, digital transmission system, user identity/authority verification, etc., can solve the problems of complexity and waste of resources, and achieve the effect of simplifying the login process and improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
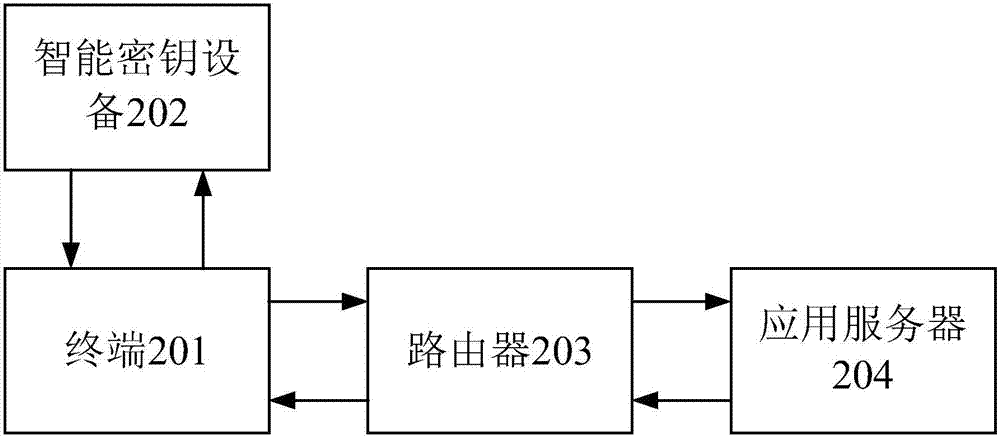
[0021] This embodiment provides a method for logging in a network application. In the process of the method, the smart key device is an identification device with an electronic signature function, which may be an electronic device such as a USB KEY or an audio KEY that can perform information interaction with the terminal; the terminal It can be a PC, mobile phone, tablet computer and other devices with network connection functions; the application server can be a network application server such as a mailbox server and an OA system server; the application server and the router are in the same intranet system, and the terminal can log in to the application through the router Intranet application of the server.
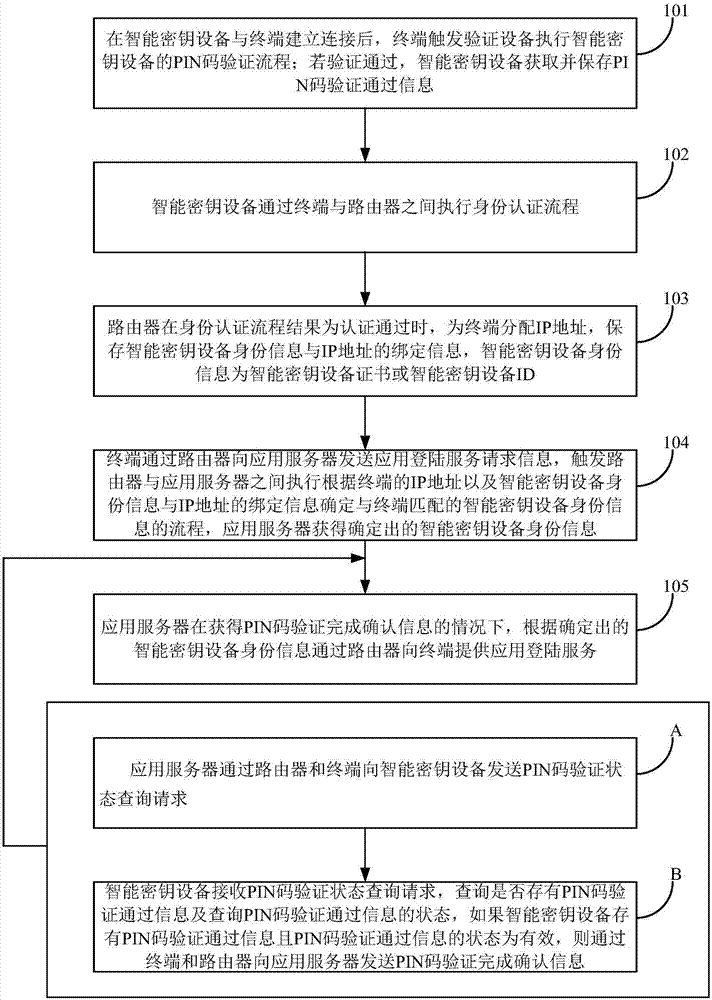
[0022] figure 1 A flow chart of a network application login method provided in this embodiment, such as figure 1 The shown method embodiment includes the following steps 101-105:
[0023] Step 101, after the smart key device establishes a connection with the terminal,...
Embodiment approach 2
[0048] Optional implementation mode 2. The difference between this optional implementation mode and optional implementation mode 1 is that the verification device in step 101 is an identity authentication server. The following only describes the differences from optional implementation mode 1:
[0049] In this step, the terminal triggers the verification device to execute the PIN code verification process of the smart key device, which specifically includes:
[0050] Step 121a, the terminal prompts the PIN code input prompt information, receives the PIN code and generates PIN code verification information, and sends the PIN code verification information to the identity authentication server;
[0051] In step 121b, the identity authentication server receives and verifies the PIN code verification information, and generates PIN code verification passing information if the verification is passed, and sends it to the smart key device through the router and the terminal.
[0052] O...
Embodiment approach 3
[0056] Optional implementation mode 3. The difference between this optional implementation mode and optional implementation mode 1 is that in step 101, the device that prompts for PIN code input and the verification device are both smart key devices. The differences are explained:
[0057] Step 131a, the terminal sends the PIN code input prompt information to the smart key device;
[0058] In step 131b, the smart key device receives and prompts the PIN code input prompt information, receives the PIN code and verifies it, and generates PIN code verification pass information if the verification is passed.
[0059] Optionally, after the smart key device generates the information that the PIN code has been verified, the information is set to a valid state.
[0060] In the solution provided by this optional implementation mode, the devices receiving the PIN code and verifying the PIN code are all smart key devices, and the PIN code does not need to be transmitted between devices, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com