Method and device for detection of malignant document
A malicious file and detection method technology, applied in the computer field, can solve the problems of low detection accuracy of WEBSHELL detection engine, missed detection of WEBSHELL detection engine, and inability to cover WEBSHELL, etc., so as to improve detection accuracy and detection efficiency and reduce detection complexity The effect of reducing the cost of operation and maintenance in the later stage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
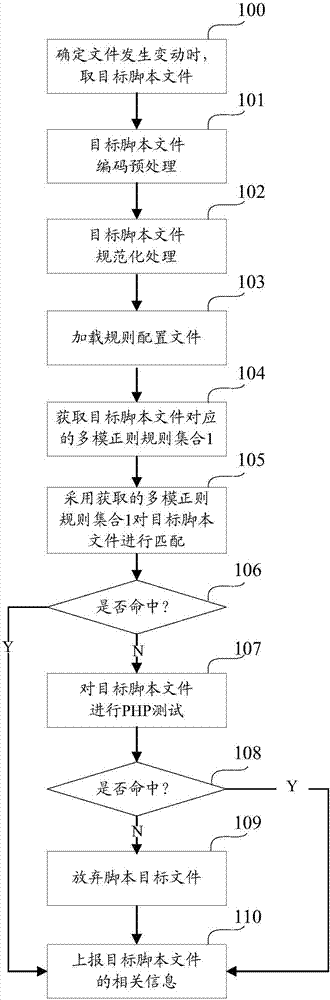
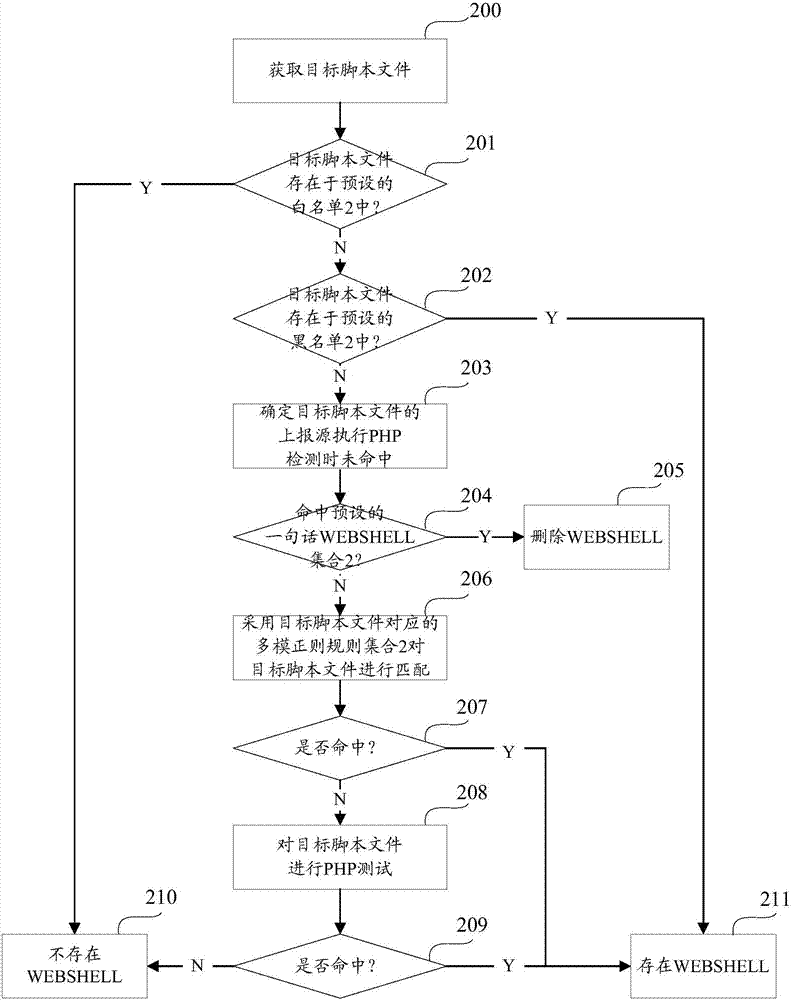
[0059] In order to improve the detection accuracy of WEBSHELL, in the embodiment of this application, based on the understanding of the nature of WEBSHELL deformation, a detection method based on the PHP virtual machine sandbox is redesigned, that is, the taint mark is set for the specified input parameters in advance, and then through Insert the Hook detection code into the target function in the target script file to detect whether the target function uses an input parameter with a taint mark, and judge whether the target script file contains WEBSHELL according to the detection result.
[0060] Preferred embodiments of the present application will be described in detail below in conjunction with the accompanying drawings.
[0061] At present, although the popular WEBSHELL evolves in various ways, after summarizing, it is found that they all have some common characteristics:
[0062] 1) Receive a superglobal variable as an input parameter.
[0063] 2) In the command executio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com