Advanced security method and device
An advanced security and module installation technology, applied in the field of network security, can solve the problems of increased hardware cost, easy leakage of user data, easy leakage of user data, etc., and achieves the effect of ensuring security and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
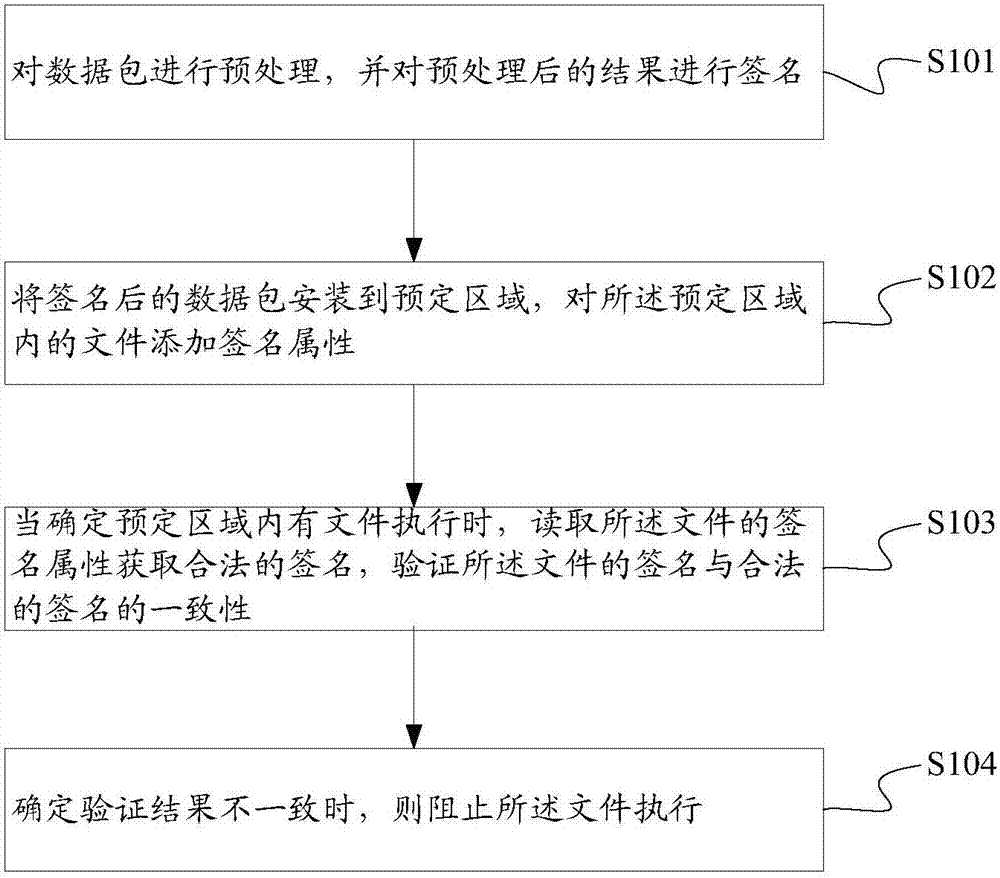
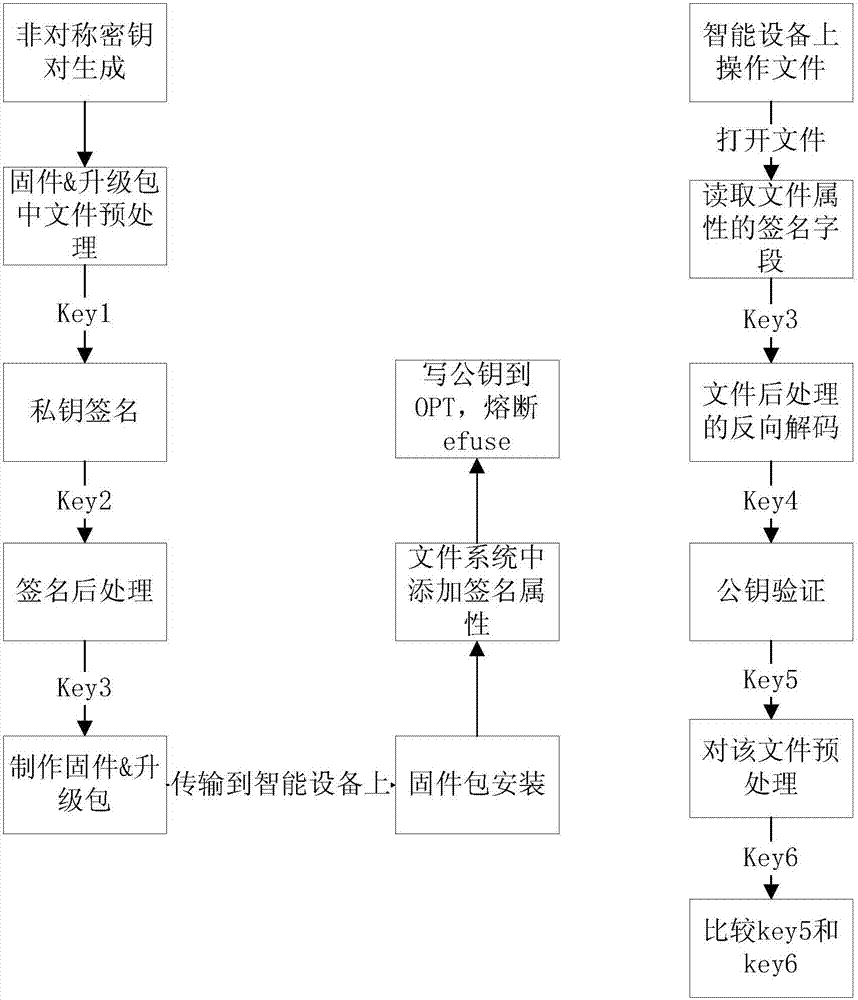
[0062] Embodiment two: figure 2 A schematic flow chart of Embodiment 2 of a high-level security method provided by the present invention, as shown in figure 2 As shown, the public key in the asymmetric key pair is stored in the OTP area of the CPU, and the advanced security method of private key signature and public key verification is adopted. The specific steps are as follows:
[0063] S201. Use an asymmetric encryption algorithm to generate a public key and a private key, the private key is used for signing, and the public key is used for verification.
[0064] S202. Unpack the firmware package or upgrade package that needs to be signed, and preprocess all the file contents in it, including but not limited to SHA256, CRC and other algorithms, to obtain the first password key1.
[0065] S203. Use the private key in the asymmetric key pair to sign key1 to obtain key2.
[0066] S204. For the convenience of storing the encrypted data, the encrypted data is post-processed ...
Embodiment 3
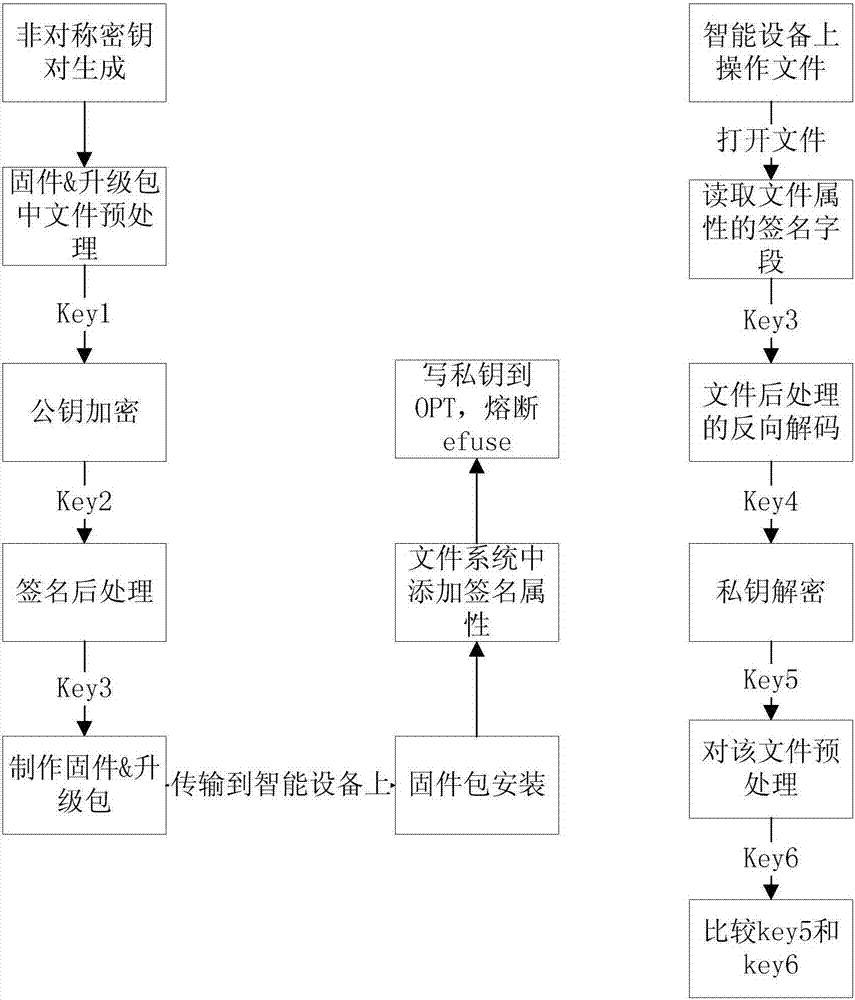
[0074] Embodiment three: image 3 A schematic flow chart of Embodiment 3 of a high-level security method provided by the present invention, as shown in image 3 As shown, the public key in the asymmetric key pair is stored in the OTP area of the CPU, and the public key is used to encrypt and decrypt the private key. The specific steps are as follows:
[0075] S301. Use an asymmetric encryption algorithm to generate a public key and a private key, where the public key is used for encryption and the private key is used for decryption.
[0076] S302. Unpack the firmware package or upgrade package that needs to be signed, and perform preprocessing on all file contents in it, including but not limited to algorithms such as SHA256 and CRC, to obtain key1.
[0077] S303. Encrypt key1 using the public key in the asymmetric key pair to obtain key2.
[0078] S304. For the convenience of storing the encrypted data, the encrypted data is post-processed into a readable character string...
Embodiment 4
[0086] Embodiment four: Figure 4 A schematic flow diagram of Embodiment 4 of an advanced security method provided by the present invention, as shown in Figure 4 As shown, the public key in the asymmetric key pair is stored in the flash memory or the system disk, and the advanced security method of private key signature and public key verification is adopted. The specific steps are as follows:
[0087] S401. Use an asymmetric encryption algorithm to generate a public key and a private key, the private key is used for signing, and the public key is used for verification.
[0088] S402. Unpack the firmware package or upgrade package that needs to be signed, and preprocess all the file contents in it, including but not limited to SHA256, CRC and other algorithms, to obtain key1.
[0089] S403. Use the private key in the asymmetric key pair to sign key1 to obtain key2.
[0090]S404. For the convenience of storing the encrypted data, the encrypted data is post-processed into a r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com