Distributed access authentication management method in LEO satellite network
A technology for access authentication and satellite network, which is applied to network topology, usage of multiple keys/algorithms, and key distribution, which can solve problems such as high computing and communication overhead, and achieve performance bottleneck avoidance, high scalability, and computing avoidance The effect of overhead and computing power waste
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
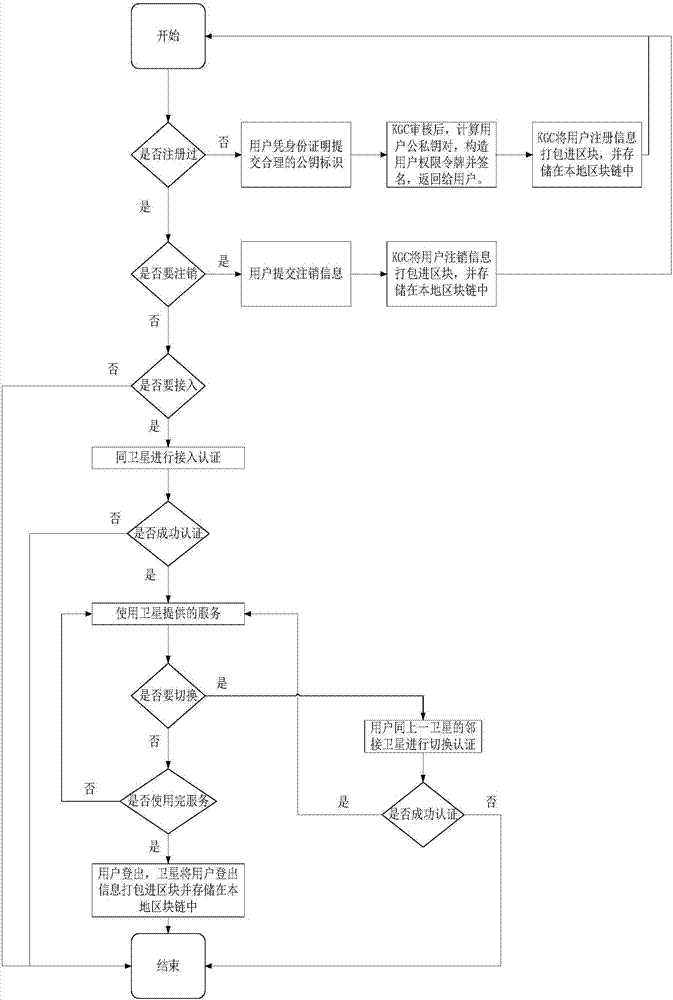
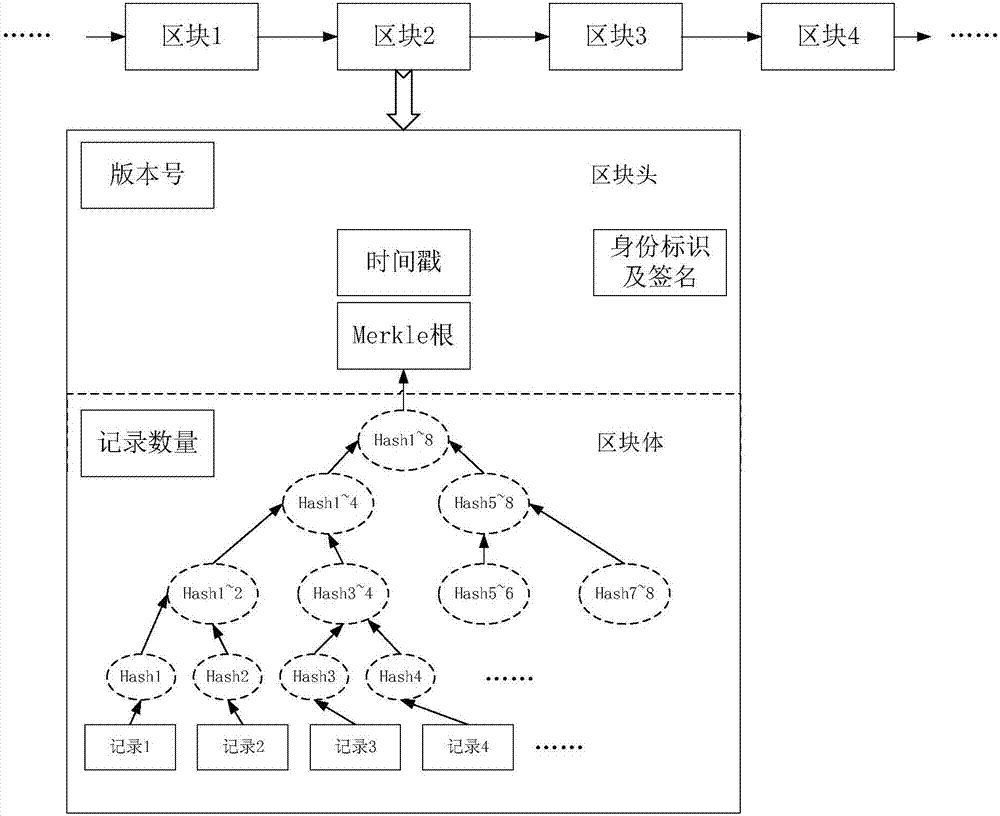
[0026] The distributed access authentication management method in the LEO satellite network of the present invention mainly has the following steps: for the convenience of description, all the methods for encryption and decryption using public and private keys involved in this method are designated to use the IBC encryption and decryption method, and the protocol involves All received message packets will contain a timestamp. When any node in the system receives a message packet, it will perform a timestamp check. The time stamp will not be described in the following description of the principle and process.
[0027] For the convenience of specific elaboration, first indicate the meaning of the following symbols:
[0028]
[0029]
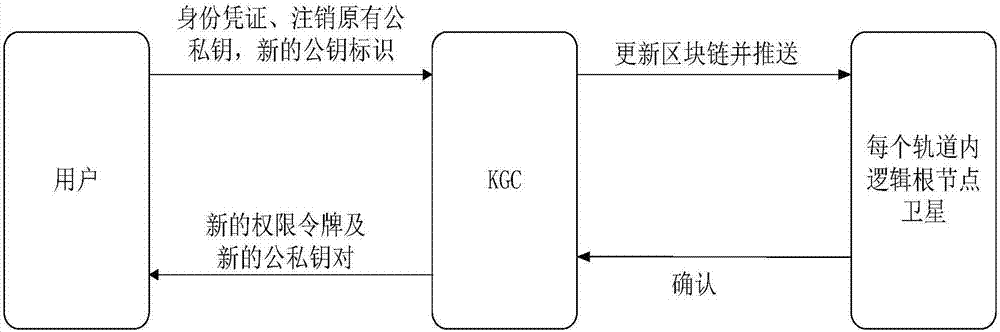
[0030] Among them, KGC is used to calculate the user's public and private key pairs and issue authorization tokens (Authorization Token ) trusted center. If the user has registered and obtained his own public-private key pair and authorizati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com