Worm homologous analysis method and device
A technology of homology analysis and worms, which is applied in the field of network information security to achieve the effect of reducing scale, improving efficiency and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
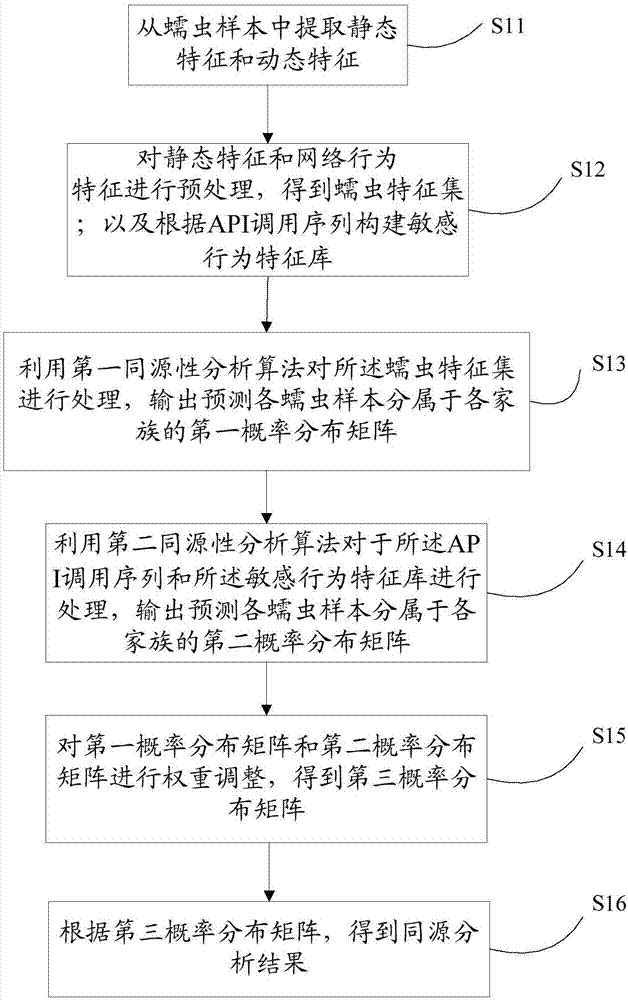
[0050] figure 1 It is a flowchart of a worm homology analysis method provided by the embodiment of the present invention. like figure 1 As shown, the method includes:
[0051] Step S11, extracting static features and dynamic features from the worm sample.
[0052] Wherein, the static feature refers to the semantic structure feature of the worm, and this part of the feature is extracted from the disassembly file of the worm sample, and is composed of assembly instructions and executable file section names;
[0053] The dynamic features include: network behavior features and application programming interface API call sequences. Among them, the network behavior feature is to extract the protocol name, target port number and message le...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com