Internet of things (IoT) access method and system of terminal equipment
A technology of the Internet of Things system and terminal equipment, which is applied in the transmission system, near-field transmission system, digital transmission system, etc., and can solve the problems that the sensing information is easy to be leaked or tampered, and the security of the sensing information cannot be guaranteed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
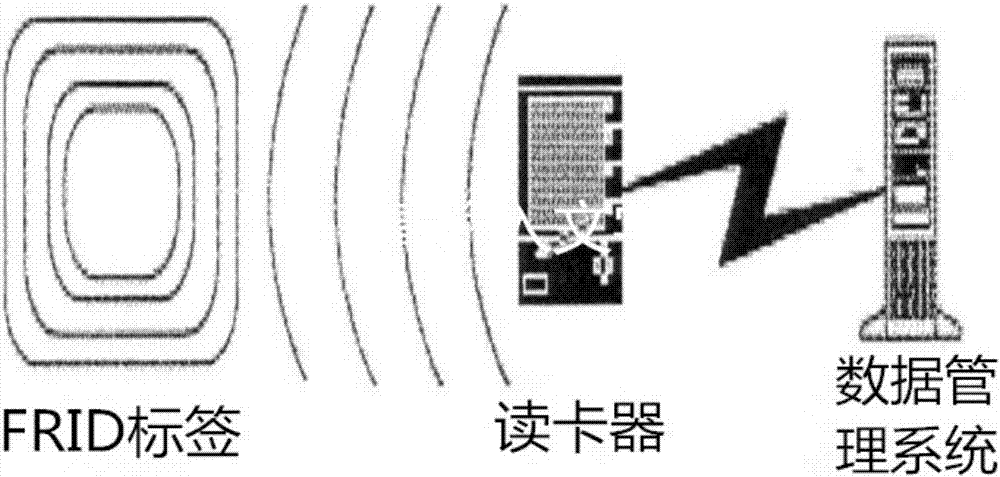
[0050] The Internet of Things is to connect any item to the Internet through radio frequency identification (RFID), infrared sensors, global positioning systems, laser scanners and other information sensing devices according to the agreed agreement, for information exchange and communication, so as to realize intelligentization. A network concept for identifying, locating, tracking, monitoring and managing. Among them, the basic principle of radio frequency identification technology is to use the transmission characteristics of radio frequency signal and space coupling (inductive or electromagnetic coupling) to realize the automatic identification of the identified object. The radio frequency identification system consists of two parts: electronic tags and readers (card readers). figure 1 As shown, in its practical application, the electronic tag is attached to the surface or inside of the object to be identified. When the object passes the range of the reader with the tag, th...
Embodiment 2
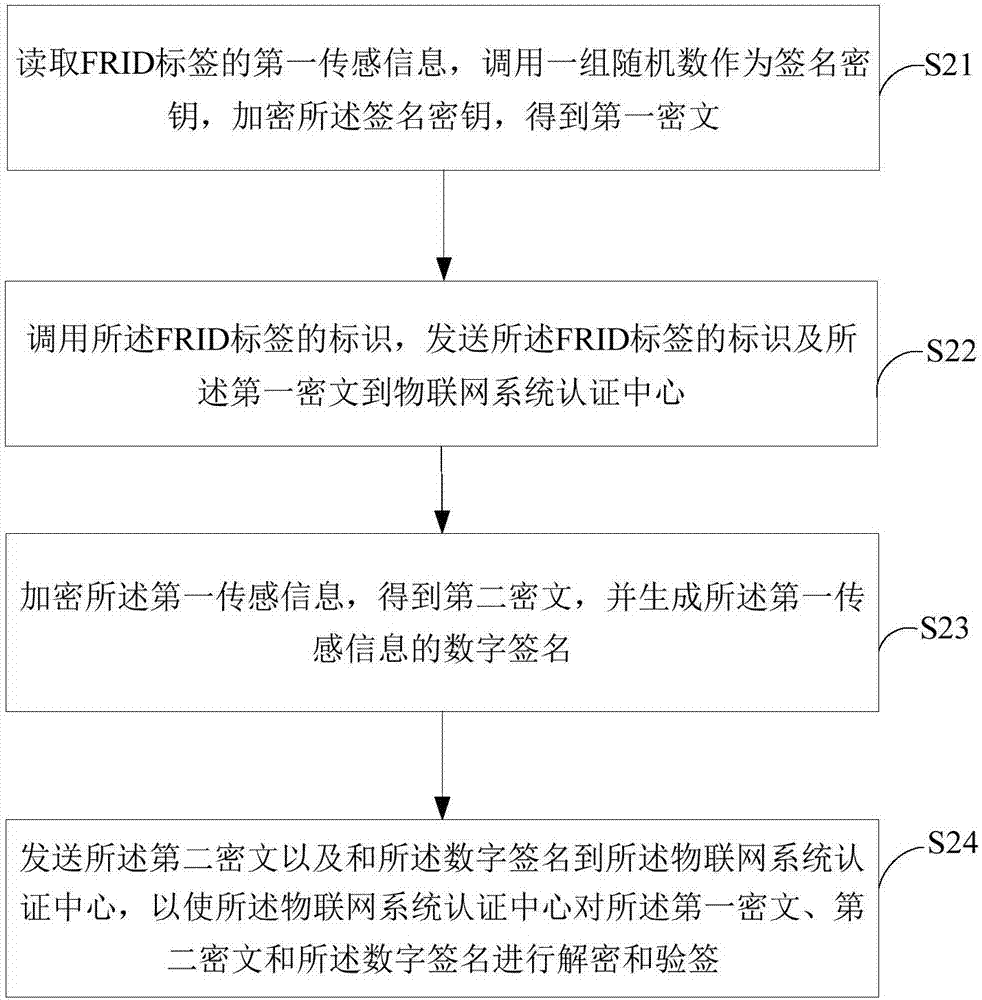
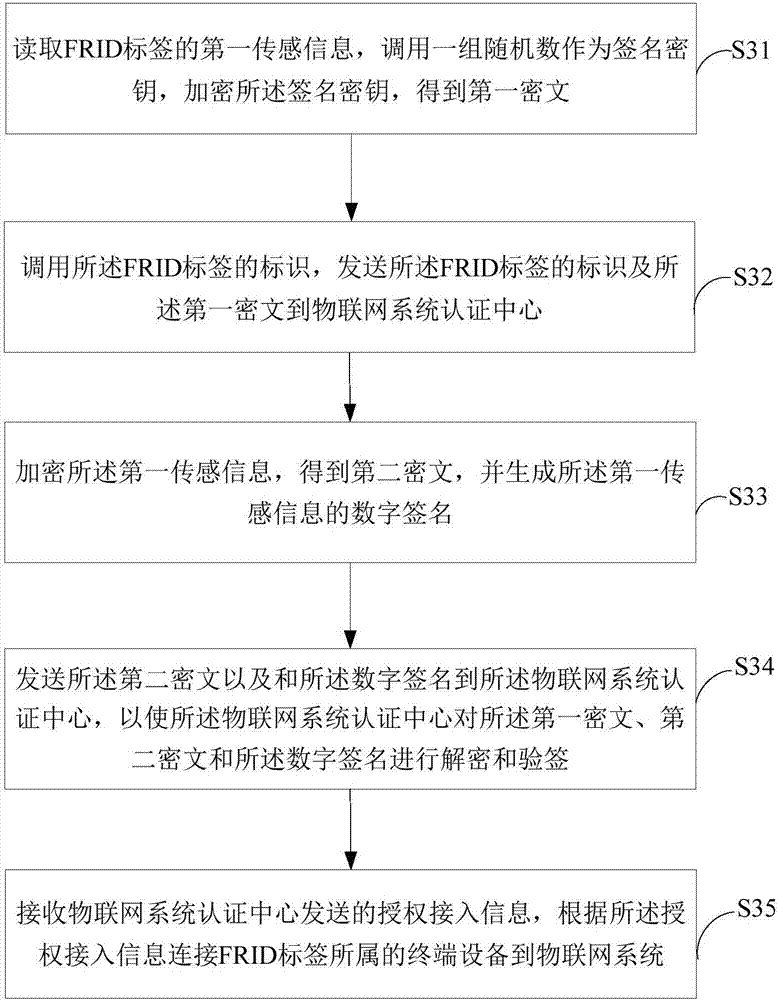
[0073] image 3 It shows a flowchart of a method for a terminal device to securely access the Internet of Things provided by the second embodiment of the present invention, as shown in image 3 The methods shown include:
[0074] Step S31, read the first sensing information of the RFID tag, call a set of random numbers as the signature key, encrypt the signature key, and obtain the first ciphertext;
[0075] Step S32, calling the identification of the RFID tag, sending the identification and the first ciphertext to the authentication center of the Internet of Things system;
[0076] Step S33, encrypting the first sensing information to obtain a second ciphertext, and generating a digital signature of the first sensing information;
[0077] Step S34, sending the identification of the RFID tag, the second ciphertext and the digital signature to the IoT system certification center, so that the IoT system certification center can verify the second ciphertext and the Decrypt and...
Embodiment 3
[0082] Figure 4 It shows a flow chart of a method for a terminal device to securely access the Internet of Things provided by the third embodiment of the present invention, and the details are as follows:
[0083] Step S41, the IoT system certification center receives and stores the identification of the RFID tag and the first ciphertext sent by the RFID card reader; and receives the second ciphertext and digital signature sent by the RFID card reader;
[0084] In this step, the authentication center of the Internet of Things system receives the identification and the first ciphertext of the RFID tag sent by the RFID card reader, and stores the identification and the first ciphertext of the RFID tag in the memory. When the identification of the RFID tag and the first ciphertext are stored, the identification of the RFID tag is analyzed and stored according to different categories of the identification of the RFID tag. For example, tags attached to terminal devices in the sam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com