A method for Android system vulnerability detection based on vulnerability poc
A vulnerability detection, Android system technology, applied in computer security devices, instruments, computing, etc., can solve the problems of low detection efficiency, incomplete detection content, and poor user experience, so as to achieve comprehensive detection content and vulnerability maintenance workload. Less, improve the effect of user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] All the features disclosed in this specification, except mutually exclusive features and / or steps, can be combined in any way.
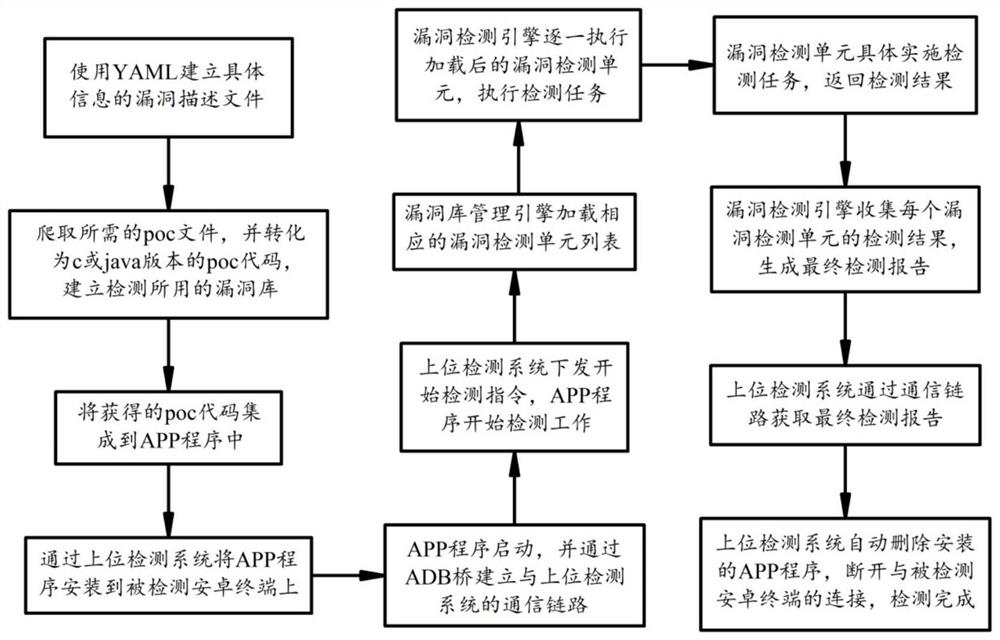
[0037] Combine below figure 1 The present invention will be described in detail.
[0038] A method for realizing Android system vulnerability detection based on the vulnerability POC belongs to the category of active detection, and the executor of the detection is an APP program, including the following steps:
[0039] Step 1 (S1): crawl the required vulnerability information from CVE and other public vulnerability websites, and use YAML to create a vulnerability description file with specific information;
[0040] Step 2: Crawl the required poc file from the public vulnerability website, and convert it into c or java version of the poc code, and use YAML and poc code to build the vulnerability library used for detection;
[0041] Step 3: Develop an APP program for detection. The APP program has functions such as vulnerability library manage...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com