Method for ensuring wireless data transmission by using fountain code-based symmetrical encryption
A wireless data, symmetric encryption technology, applied in digital transmission systems, security devices, transmission systems, etc., can solve the problems of large feedback load, poor information transmission security, eavesdropping, etc., achieve small feedback load, improve security, design reasonable effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention is described in further detail below in conjunction with accompanying drawing:
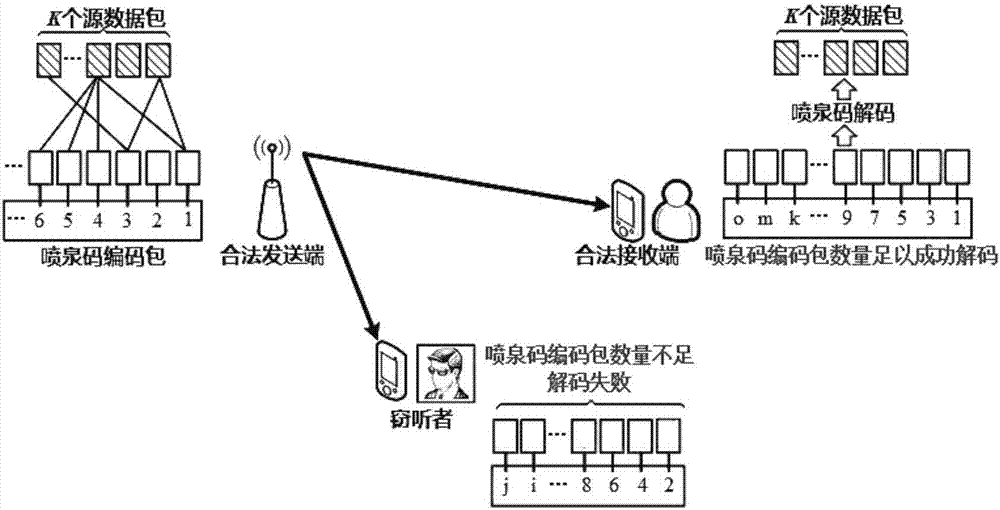
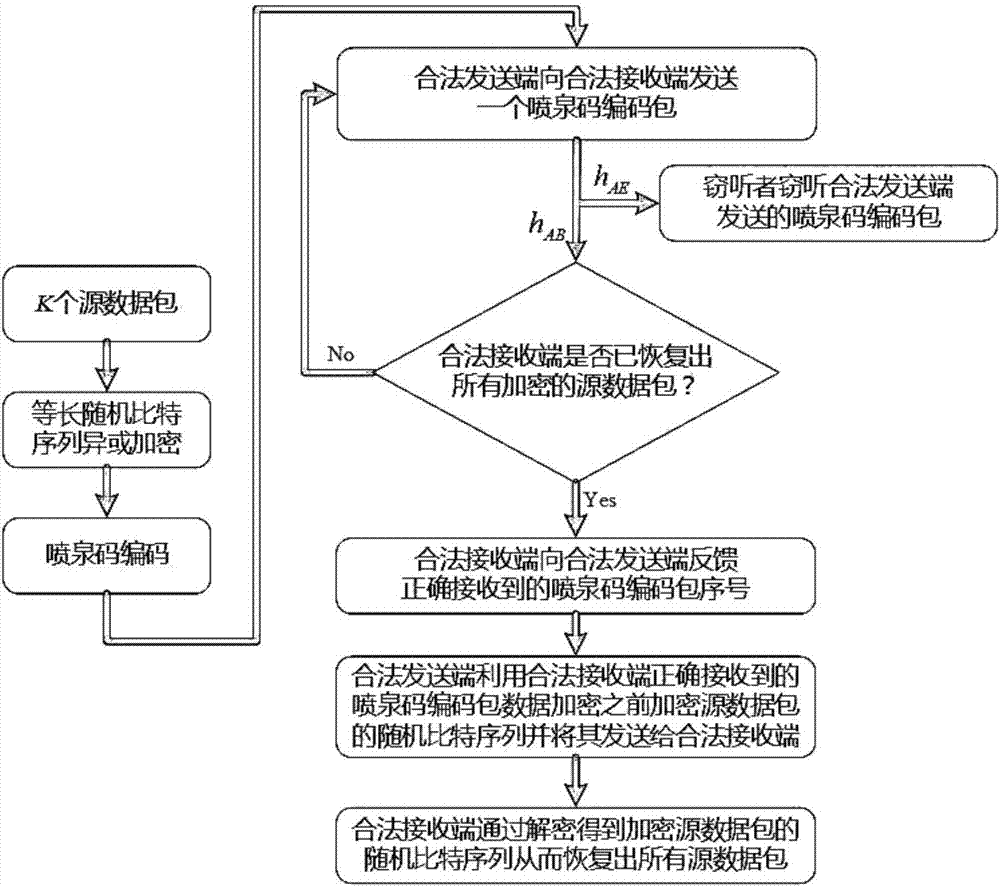
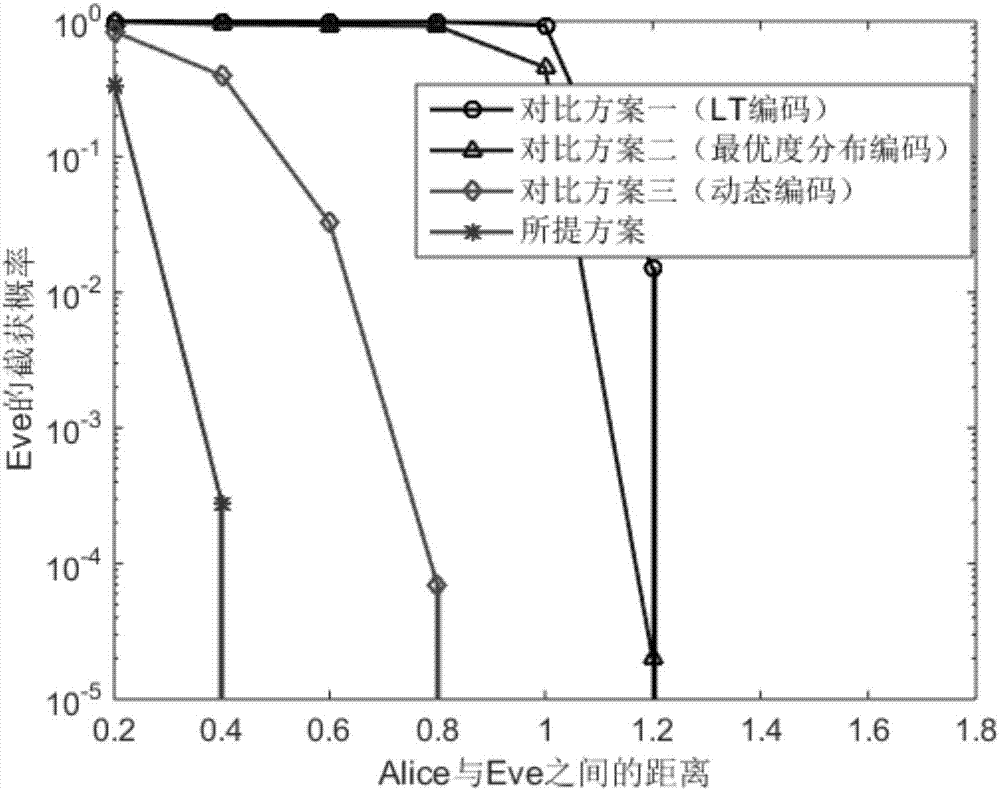
[0023] refer to figure 1 , as a rateless erasure code, fountain code mainly includes LT code and Raptor code. The legitimate sender uses fountain codes for encoding, and each fountain code encoding packet is obtained by XORing randomly selected different source data packets. The legal receiving end can only successfully decode and restore the data after receiving enough fountain code encoding packets, and the legal sending end stops the fountain code encoding and the sending of the encoding packets only after receiving the feedback that the legal receiving end has completed decoding and data recovery . This means that when the legal receiver can receive enough Fountain Code encoding packets before the eavesdropper and complete Fountain Code decoding and data recovery, then the security of the transmitted data can be guaranteed.
[0024] The key idea of the present...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com