False alarm elimination method based on log playback
A log and false positive rate technology, applied in the field of network security, can solve a large number of manual inspections and other problems, and achieve the effect of eliminating false blocking and false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Below in conjunction with accompanying drawing and specific embodiment the present invention is described in further detail:
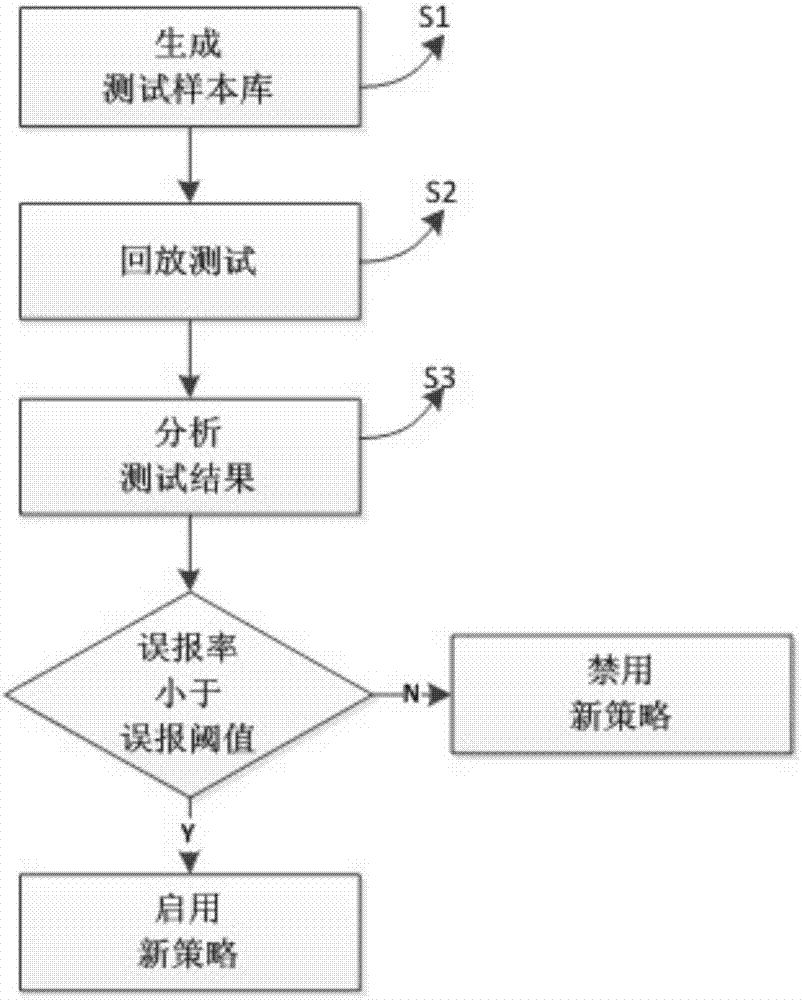
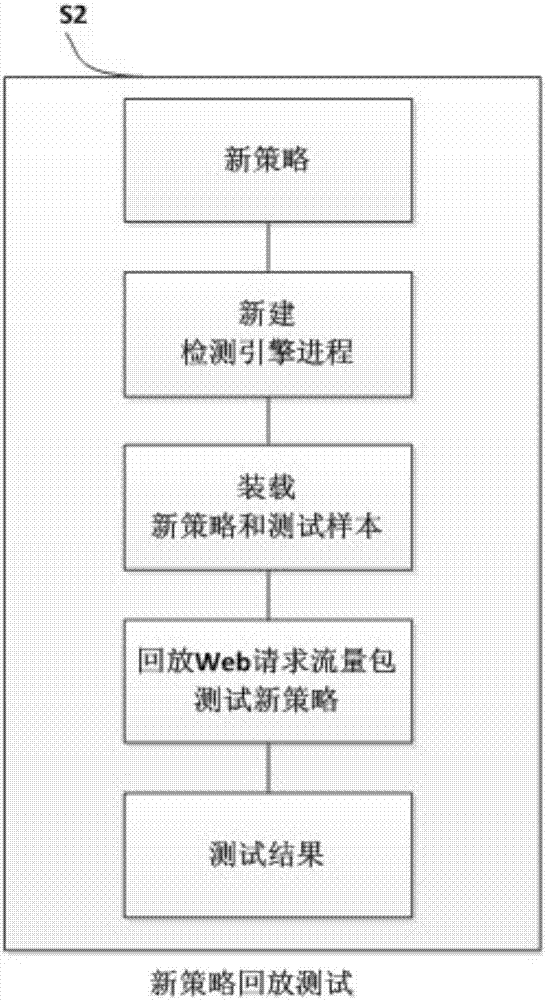
[0035] Such as figure 1 The shown method for eliminating false alarms based on log playback is used to maintain the rule base of the Web application protection system WAF, and specifically includes the following steps:
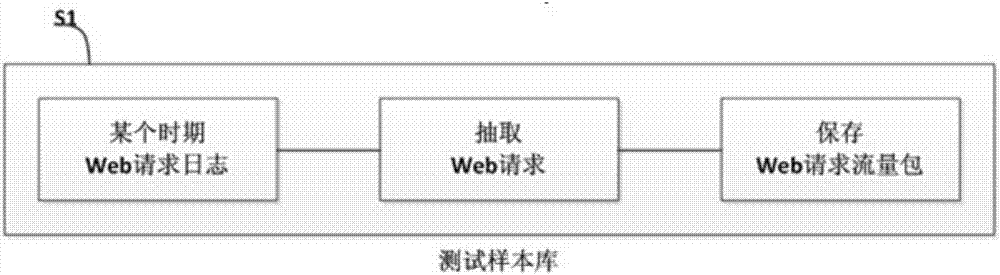
[0036] S1) Dynamically generate a test sample library, specifically through the following sub-steps:
[0037] Step A: first obtain the access log of the web application within a certain time period (the specific time period can be configured), that is, the access log saved in the WEB server.
[0038] Step B: From the access log obtained in step A, extract the web request. A web request is an access request initiated by a client to a web application.
[0039] Step C: According to the Web request obtained in Step B, obtain the corresponding Web request parameter, that is, the request content, from the access log to form a test ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com