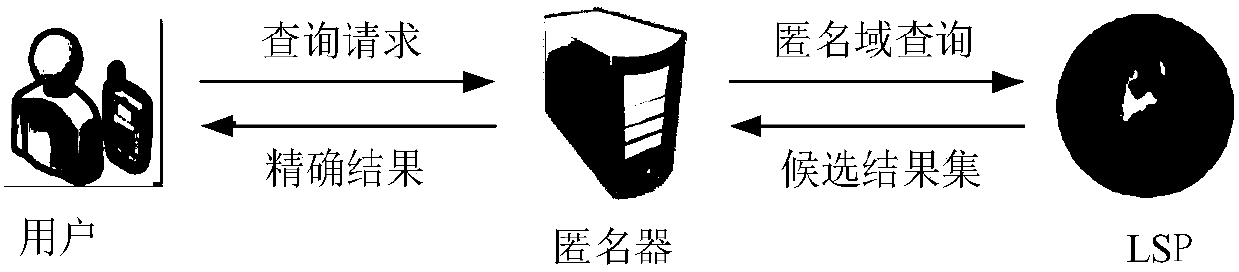
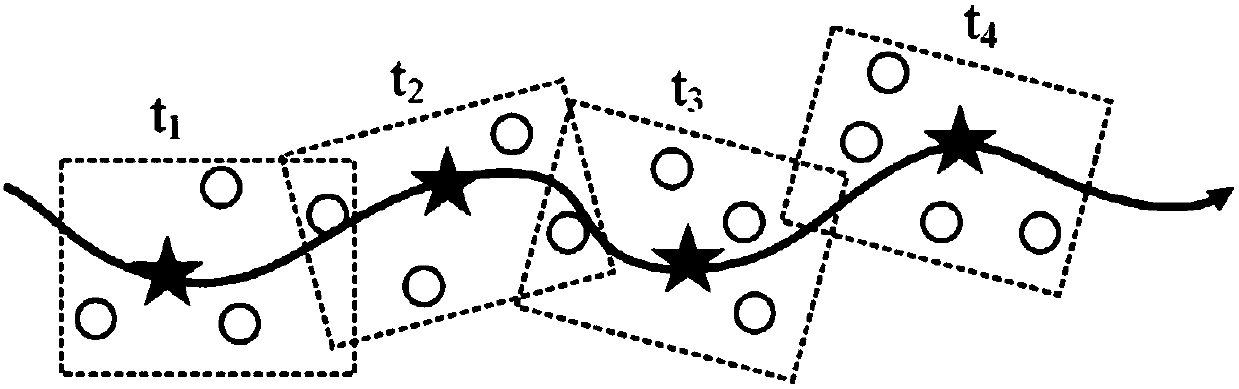
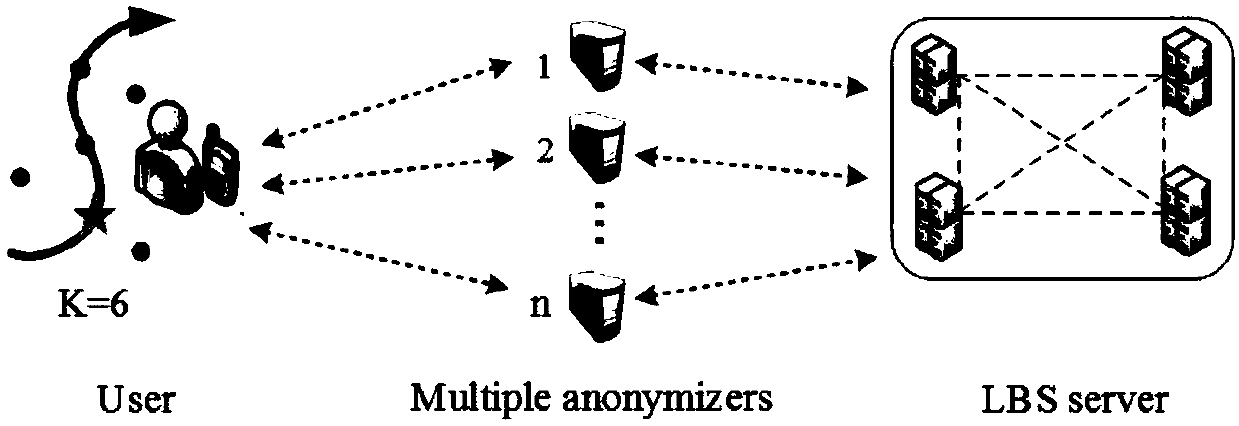
Trace privacy protection method based on double K mechanism
A technology of privacy protection and tracking, which is applied in location information-based services, security devices, electrical components, etc. It can solve the problems of leaking sensitive information of users and difficulty in ensuring the privacy of user tracking.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0060] Such as image 3 As shown, a trajectory privacy protection method based on the double K mechanism includes the following steps:
[0061] Step 1: Based on the user's current location and the query real location, construct g query prediction locations based on the hybrid prediction model of the trajectory mode, and select K-g-1 query fake locations based on the query prediction location to query the real location and query prediction location Form K query positions with query fake positions;
[0062] Among them, K represents the number of query requests corresponding to the query location sent by the user to the location service provider during a point of interest search process, and
[0063] Obtain g query prediction positions by using the predicted positions, and obtain K-g-1 query false positions by using a false position selection mechani...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com