Start-stop method and system and security detection method and system based on construction of Linux system services
A system service and security detection technology, applied in the field of host system security enhancement, can solve problems such as complex and tedious installation packages, and achieve the effects of improving construction speed, simple and fast construction, and shortening detection cycle.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
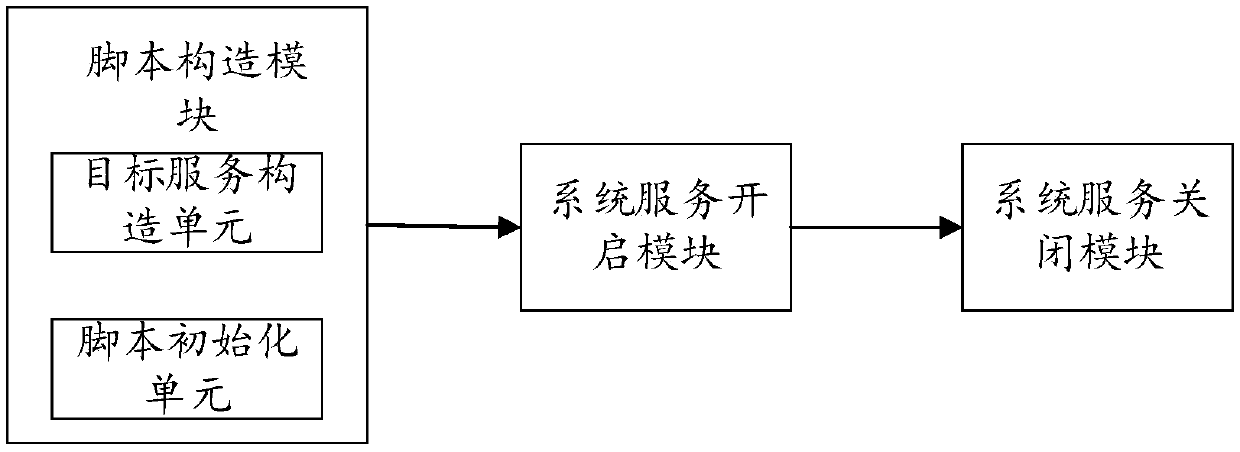
Image
Examples
Embodiment 1
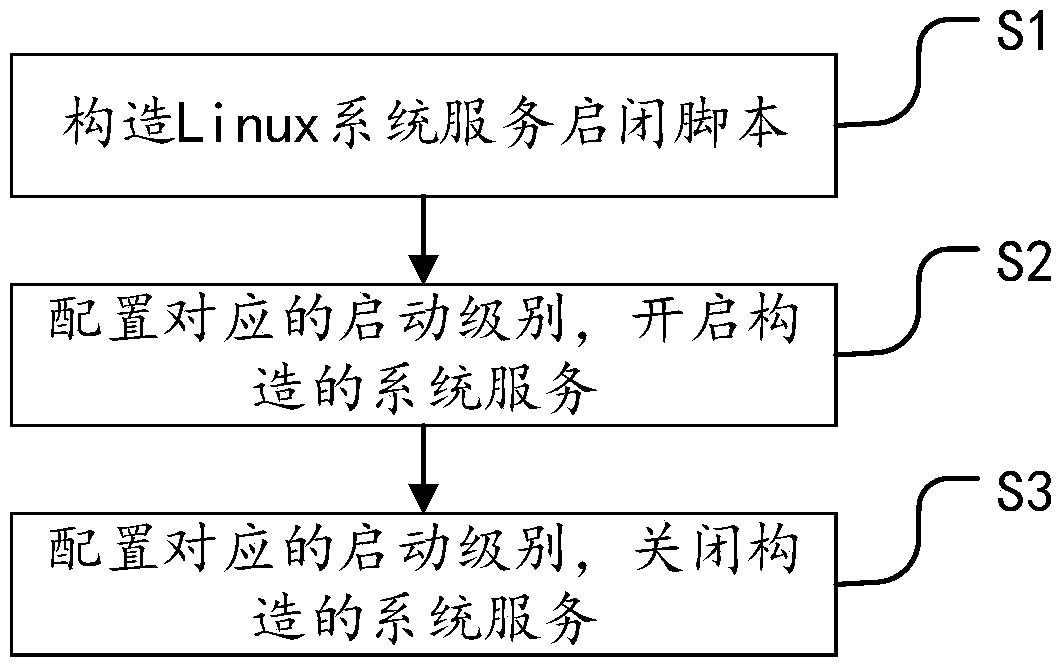
[0034] Such as figure 1 As shown, the embodiment of the present invention discloses a method for opening and closing based on constructing Linux system services, comprising the following steps:
[0035] Construct Linux system service startup and shutdown scripts.
[0036] The init.d directory contains many startup and stop scripts for various services of the system. When Linux starts, it will search for the service scripts in these directories, and determine different startup levels according to the run level of the scripts.
[0037] In the init.d directory, use the existing service to clone the target service. For example, when constructing the target service dovecot service, you can use the existing Linux service network to construct, that is, copy the network service, and execute the following command to complete the copy task:
[0038] "cp / etc / init.d / network / etc / init.d / dovecot"
[0039] By copying the command, the dovecot service is added to the init.d directory. Howev...
Embodiment 2
[0083] The embodiment of the present invention discloses a security detection method based on constructing Linux system services, comprising the following steps:
[0084] Construct Linux system service startup and shutdown scripts.
[0085] In the init.d directory, use the existing service to clone the target service. For example, when constructing the target service dovecot service, you can use the existing Linux service network to construct, that is, copy the network service, and execute the following command to complete the copy task:
[0086] "cp / etc / init.d / network / etc / init.d / dovecot"
[0087] By copying the command, the dovecot service is added to the init.d directory. However, the completed dovecot service is different from the real dovecot service. Its content is the same as that of the network service, but the name has changed. When the system recognizes the service type, because the system judges only according to the name, although the substantive content of the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com