Android malicious software detection method based on API characteristics
A technology of malware and detection methods, applied in the fields of instruments, digital data processing, platform integrity maintenance, etc., which can solve problems such as consumption of traffic for no reason, crashes, file and data damage in mobile phones, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
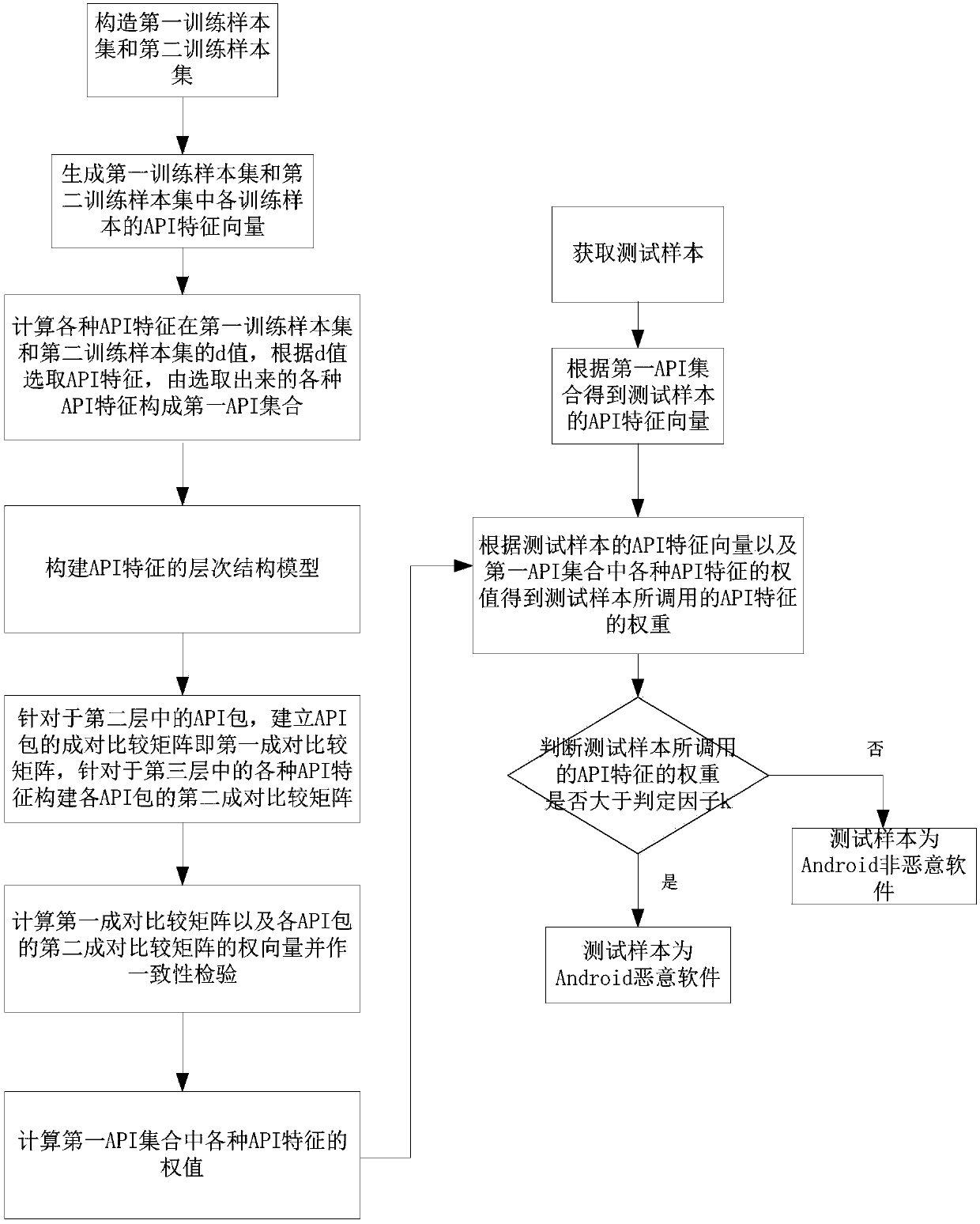
[0078] The invention discloses a method for detecting Android malware based on API features, such as figure 1 As shown, the steps are as follows:
[0079] Step S1, obtain a certain number of Android malware training samples to construct the first training sample set, obtain a certain number of Android non-malware training samples to construct the second training sample set; in this embodiment, the Android malicious software in the first training sample set The quantity of software training sample is greater than the quantity of the Android non-malicious software training sample in the second training sample set, obtains 944 Android malicious software training samples to construct the first training sample set in the present embodiment, in the present embodiment, obtains 171 Android non-malware training samples.
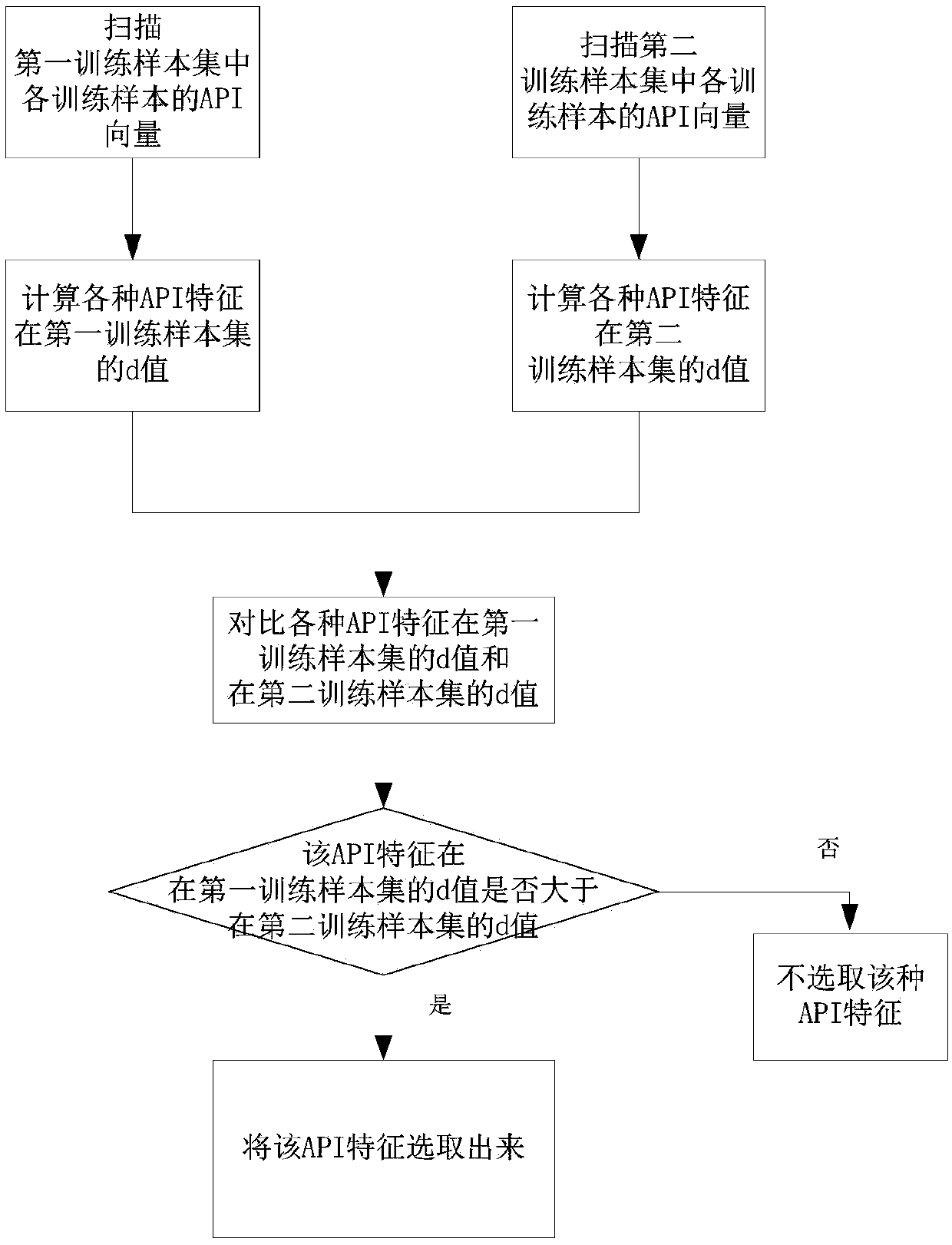
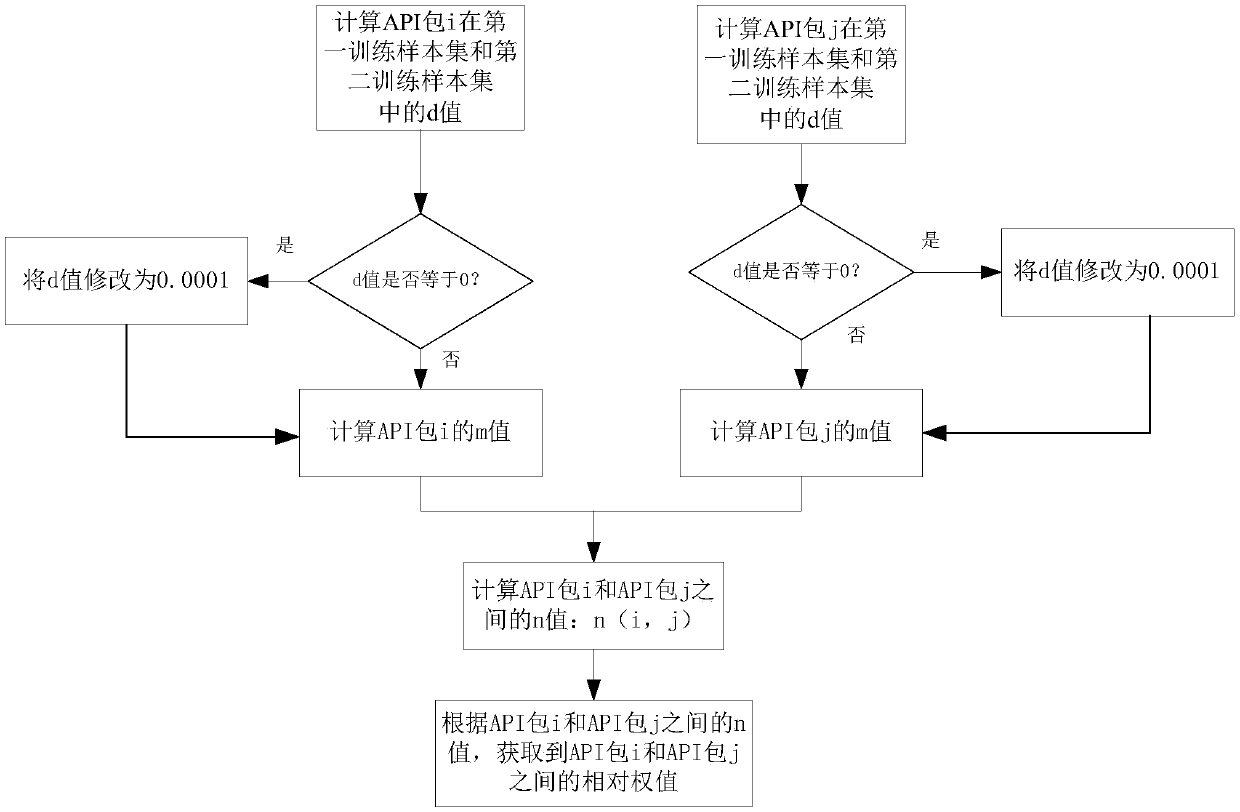
[0080] Step S2, for each training sample in the first training sample set and the second training sample set, analyze the API features called in each APK file, there...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com