Method used for connecting skynet system and recoding card transaction illegal behavior
A record card and skynet technology, applied in the payment system, payment system structure, agreement authorization, etc., can solve the problems of asset loss, unscrupulous verification procedures, and affecting the relationship between the police and the public, so as to prevent fraud and protect interests and property Safety and guarantee the effect of normal operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
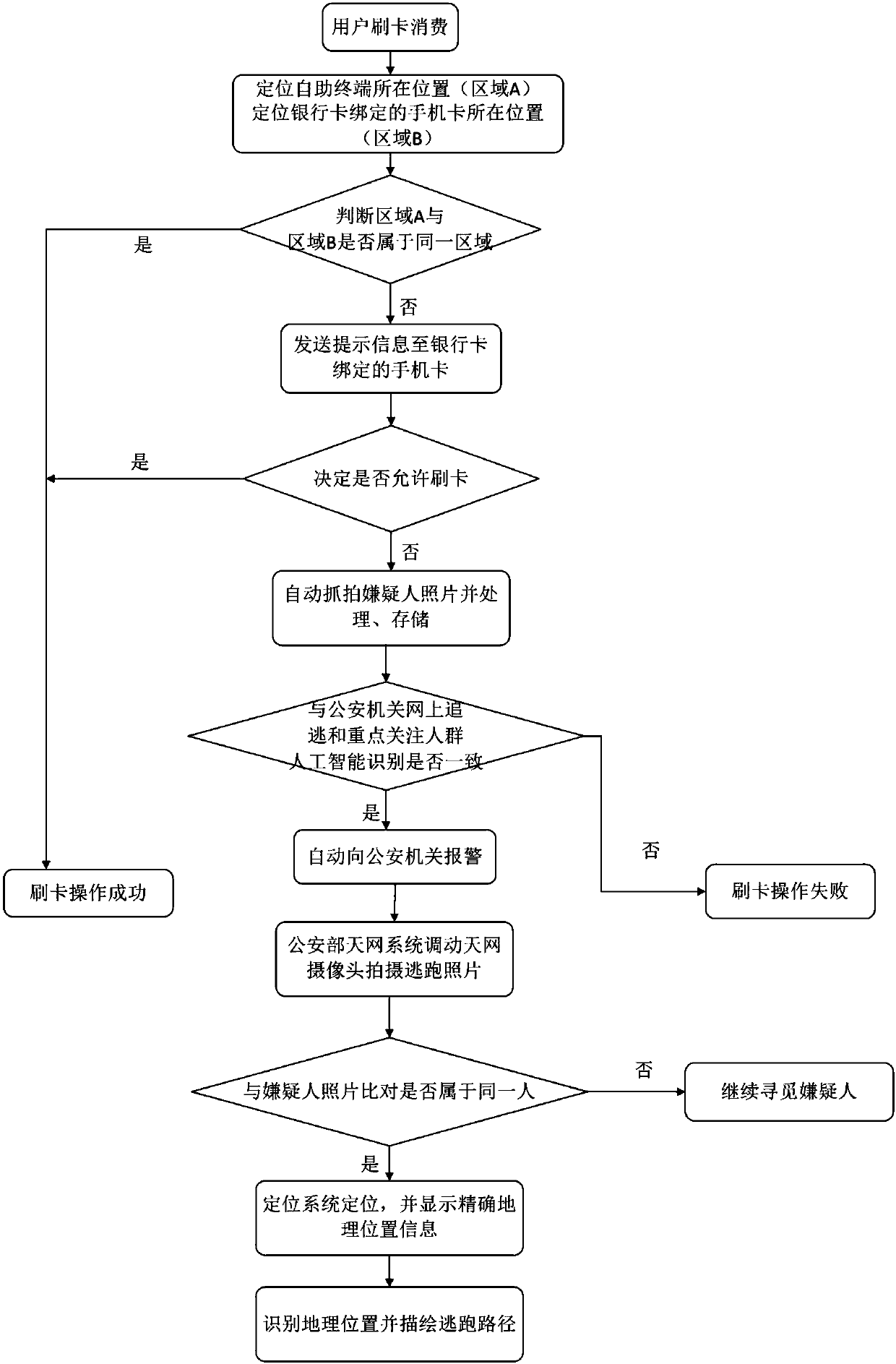
[0060] Step 1: The user performs consumption by swiping the card at the payment terminal;
[0061] Step 2: The bank card transaction system obtains the transaction information, identifies the bank card account number, and reads the reserved mobile phone number bound to the bank card account number and other related information through the bank card system database;
[0062] Step 3: The location service platform of the communication operator locates the reserved mobile phone number read in step 2, and obtains area B; and sends a request to the positioning system to obtain the geographic location information of the card swiping terminal (area A);
[0063] Step 4: The bank card management platform judges whether area A and area B belong to the same area, if area A and area B belong to the same area, the payment terminal prompts that the card swiping operation is successful, and completes the card swiping operation; if area A and area B do not belong to the same area area, call th...
Embodiment 2
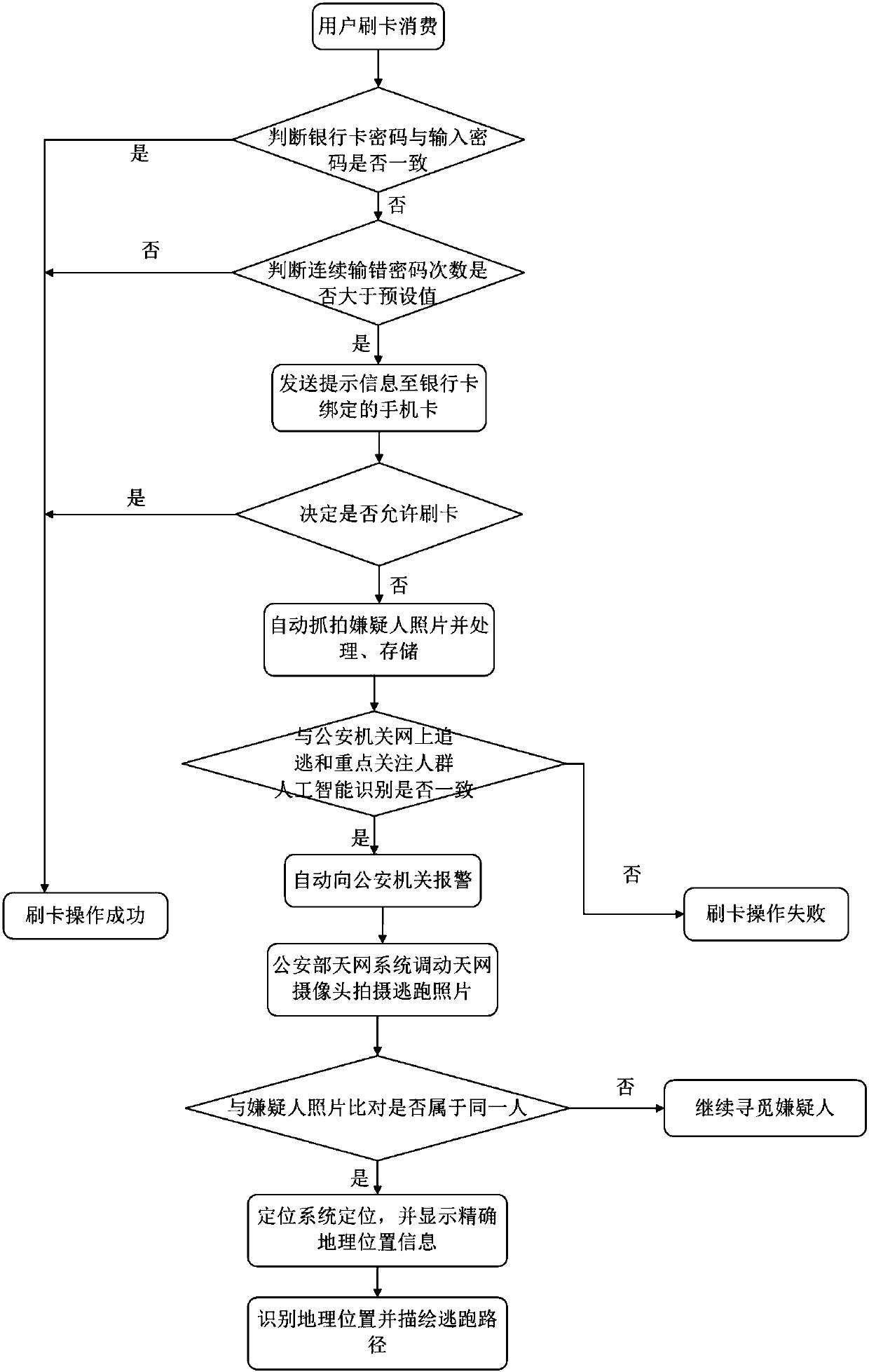
[0066] As described in Embodiment 1, a method for docking with the Skynet system to record card transaction violations, in step 5, if the user does not allow the card to be swiped, the payment terminal automatically captures the suspect’s photo through the camera, and by setting it in the The core controller inside the payment terminal reads the suspect’s graphic information and uploads and stores it to the artificial intelligence identification system, and conducts artificial intelligence identification with the public security agency’s online pursuit and key focus groups; if the identification results are consistent, the payment terminal prompts for card swiping operation If it fails, it will automatically report to the public security organ;
[0067] Step 6: Transmit the suspect’s graphic information to the public security video surveillance system, which is connected to the Skynet system of the Ministry of Public Security to mobilize the Skynet camera to take photos of the ...
Embodiment 3
[0070] As described in Example 2, a method for docking with the Skynet system to record card transaction violations, if the public security organ’s online pursuit and key focus groups are identified by artificial intelligence with the suspect’s photos, and the identification results are inconsistent, the payment terminal prompts Swipe operation failed.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com