High-security steganography method for voice over IP
A high-security, voice technology, applied in the field of secure communication, can solve the problems of not distinguishing the difference of available carrier bits, small embedded capacity, etc., and achieve the effect of improving imperceptibility and reducing distortion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
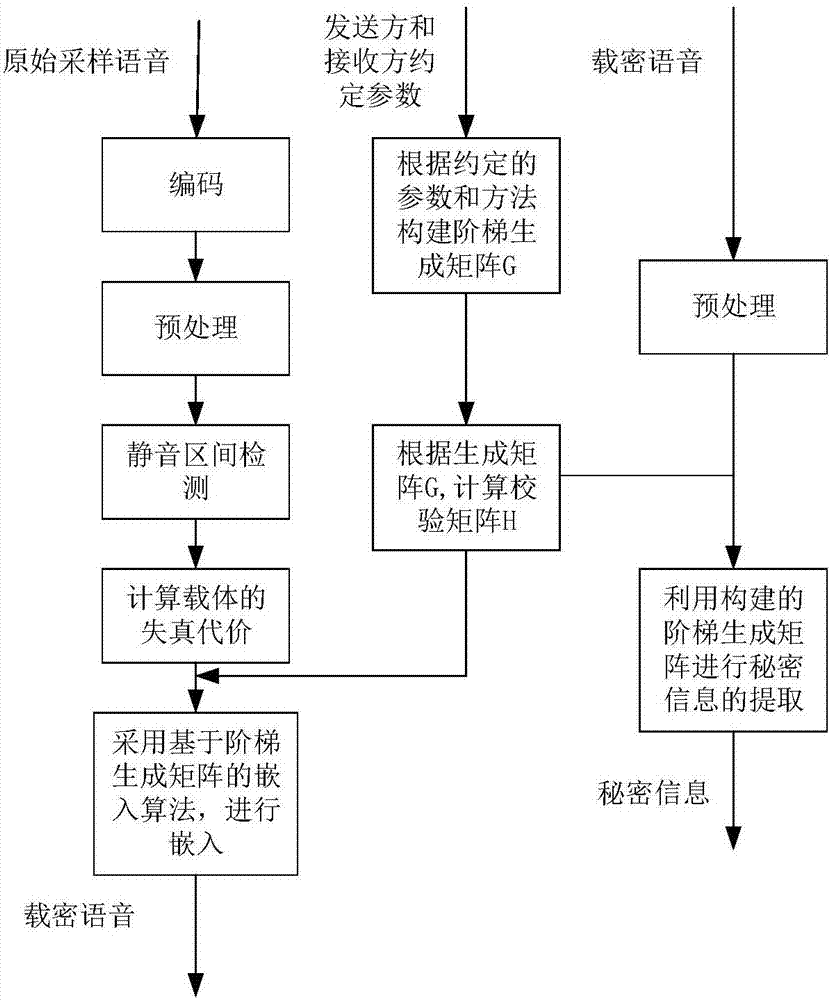
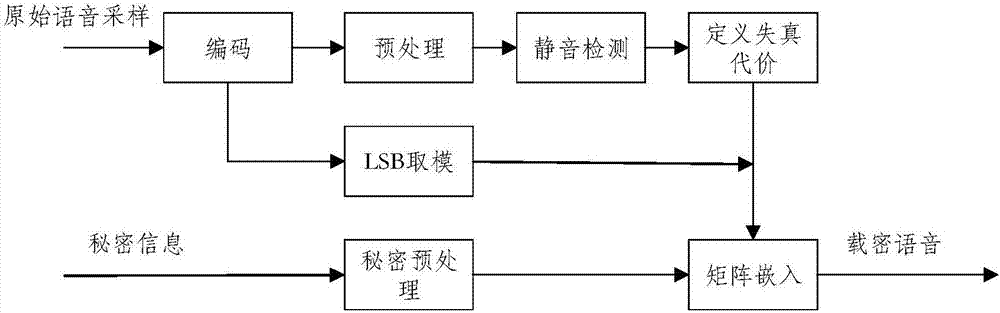
Image
Examples
Embodiment 1
[0074] In this embodiment, the voice sample set in ITU-Appendix P.501 is used for testing. The voice sample set covers male voice and female voice audio samples from various countries in the world, monophonic, 8KHz, 16-bit sampling.
[0075] Setting embedding rate is respectively 0.2, 0.3, 0.4, 0.5, 0.6, at each embedding rate, adopts the method of the present invention to carry out steganography, adopts the objective voice quality evaluation (PESQ) method that ITU-TP.862 standard provides to MOS- The LQO value has been tested and counted, and the results are attached Figure 4 As shown, it can be seen that the speech quality of the encrypted speech sample processed by the steganographic method of the present invention is closer to the speech quality of the coded speech sample without steganography.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com