A vehicle network security authentication method, system, vehicle, device and medium
A security authentication and vehicle network technology, applied in the field of automotive electronics, can solve the problems of vehicle driving safety, vehicle owner safety risk, malware intrusion, vehicle owner information leakage, etc., to avoid delaying the repair of security vulnerabilities, avoiding the intrusion of malicious commands, and improving The Effects of Network Security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] This embodiment provides a method for vehicle network security authentication, please refer to figure 1 , figure 1 It is a flowchart of a method for vehicle network security authentication in an embodiment of the present application, the vehicle includes a vehicle communication box, a gateway and a vehicle-specific microcomputer controller, and the method includes:
[0057] Step S101, the vehicle communication box receives the command sent by the remote service provider, and performs certificate verification on the command according to the certificate issued by PKI in advance; if the vehicle communication box certificate verification is successful, then sends the command to said gateway;
[0058] Step S102, the gateway performs certificate verification on the command according to the certificate issued in advance by the PKI; if the gateway certificate verification is successful, then send the command to the automobile-specific microcomputer controller;
[0059] Step S...
Embodiment 2
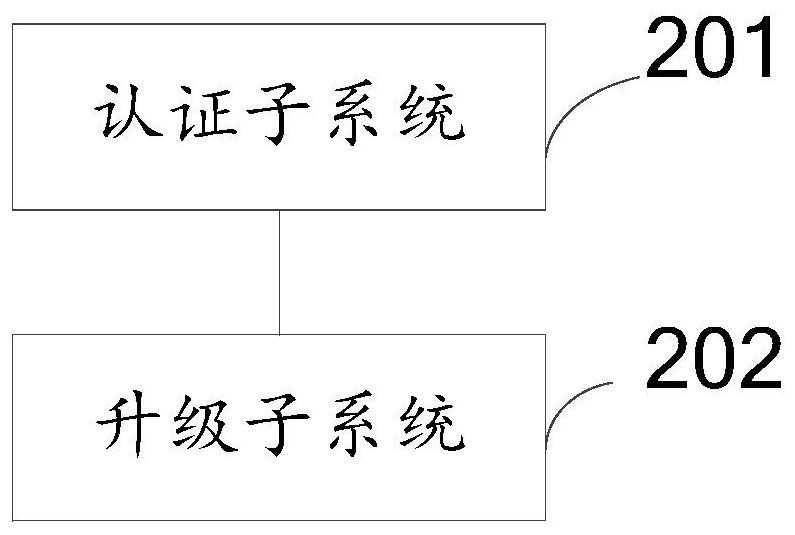
[0146] Such as figure 2 As shown, a network security system is provided, the system is applied to a vehicle, including:
[0147] Authentication subsystem 201, said authentication subsystem establishes the trust system among remote service provider, vehicle-mounted communication box, gateway and automobile special-purpose microcomputer controller through public key infrastructure; and establishes identity authentication system through PKI, through described identity The certification system assigns a corresponding unique root certificate to the vehicle manufacturer of the vehicle in question;
[0148]The upgrade subsystem 202, the upgrade subsystem adopts the over-the-air technology to establish upgrade channels for the vehicle communication box, the gateway and the vehicle-specific microcomputer controller.
[0149] In the embodiment of the present application, the network security system also includes a security chip SE, a digital certificate assigned to the vehicle by PKI ...
Embodiment 3
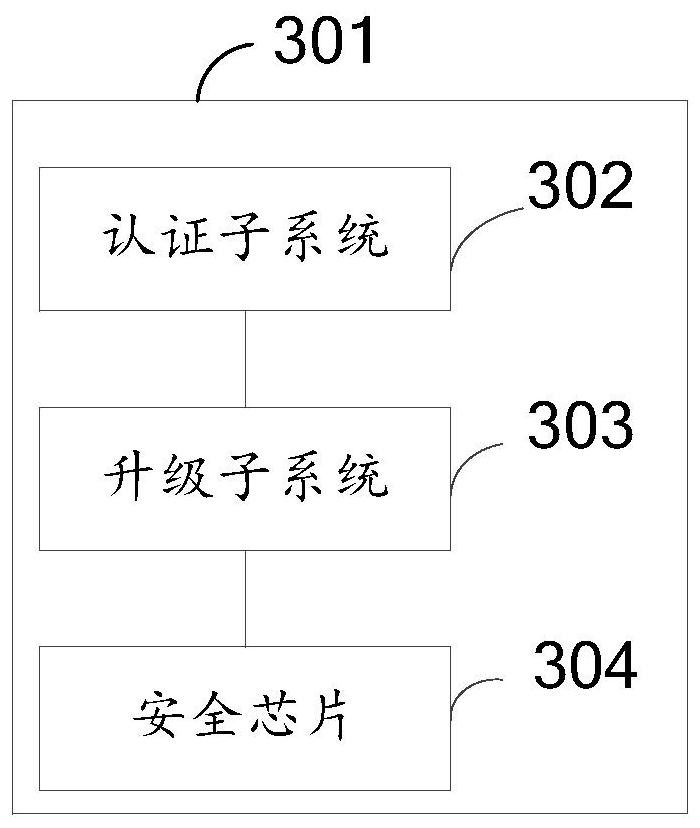
[0154] Such as image 3 As shown, a vehicle is provided, the vehicle includes a vehicle body 301, and further includes:
[0155] Authentication subsystem 302, said authentication subsystem establishes trust system between remote service provider, vehicle communication box, gateway and automobile special-purpose microcomputer controller by public key infrastructure (Public KeyInfrastructure, PKI); And establish identity authentication by PKI system, assigning a corresponding unique root certificate to the vehicle manufacturer of the vehicle through the identity authentication system;
[0156] An upgrade subsystem 303, the upgrade subsystem adopts Over-the-Air Technology (OTA) to establish an upgrade channel for the vehicle communication box, the gateway and the vehicle-specific microcomputer controller.
[0157] In the embodiment of the present application, the vehicle also includes a security chip 304, a digital certificate assigned to the vehicle by PKI (including the unique...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com