Port network intrusion detection method based on Bayesian network
A network intrusion detection, Bayesian network technology, applied in data exchange networks, instruments, character and pattern recognition, etc., can solve problems such as unconvincing, difficult to visualize, and difficult to explain black box models
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
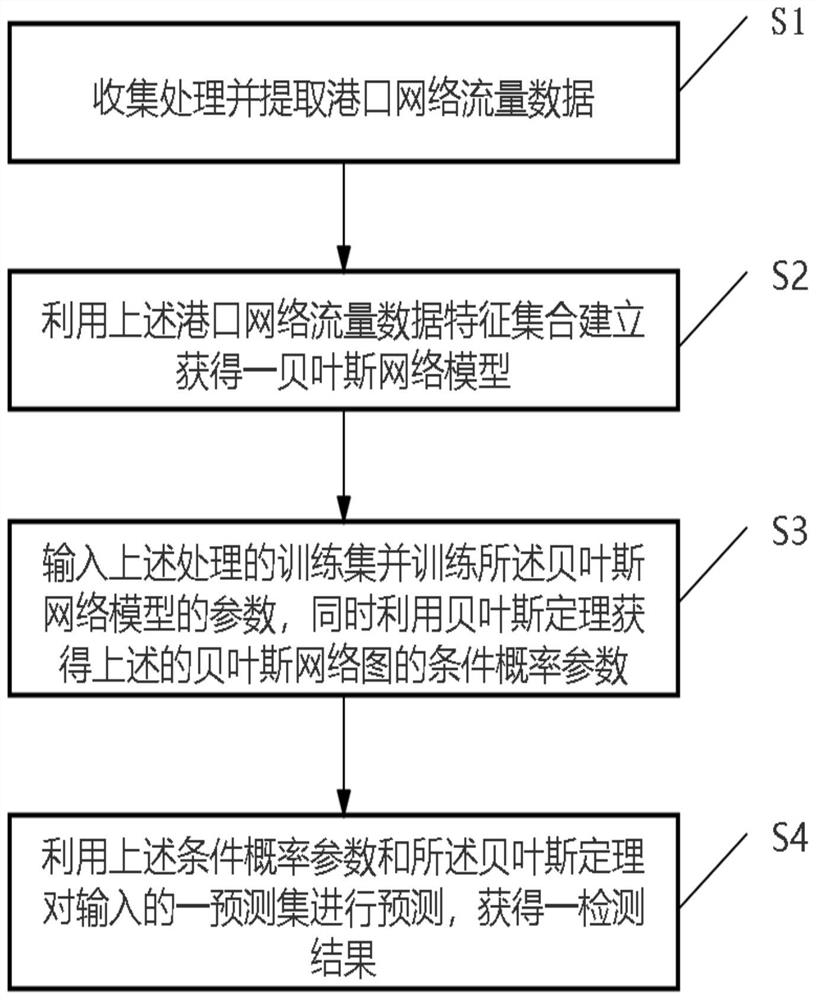
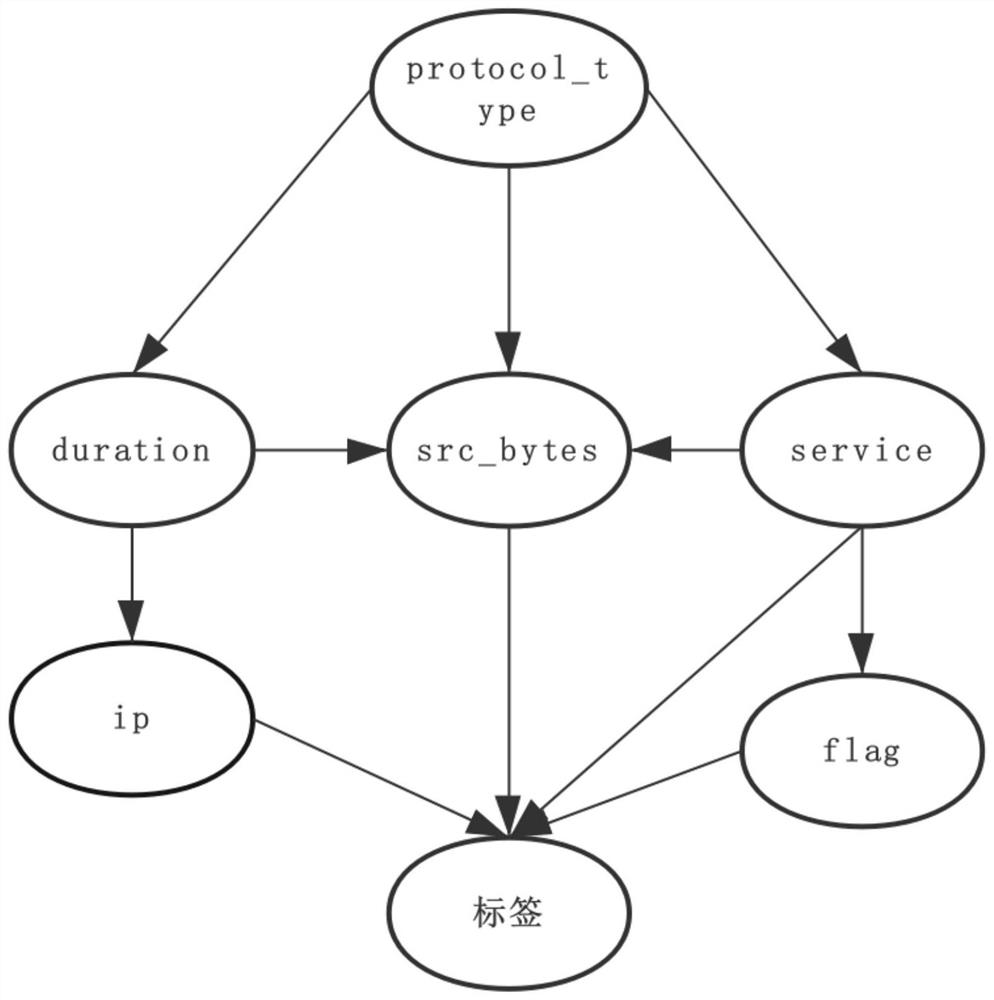
[0060] According to the attached Figure 1 ~ Figure 2 , give the preferred embodiment of this study, and give a detailed description, so that the functions and characteristics of the present invention can be better understood. In this embodiment, the algorithm environment is based on: Python, Pgmpy Bayesian network model, Pandas analysis library and Numpy library.
[0061] Multiple data sources in this embodiment specifically refer to data sets obtained by multiple port data receiving interfaces; network flow data specifically refer to network data packets captured from port data interfaces through tcpdump and wireshark packet capture.
[0062] see Figure 1 ~ Figure 2 , a Bayesian network-based port network intrusion detection method in the embodiment of this study, comprising steps:
[0063] S1: First, collect and preprocess the network data packets in the port data interface through packet capture software (such as wireshark) to obtain a network traffic feature set S.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com