Network access control method and system and related equipment
A technology for network access and network equipment, applied in the field of communication, can solve the problems of complex network deployment, poor client security, poor isolation of different services, etc., to achieve the effect of increasing security, enhancing isolation, and reducing the complexity of network deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
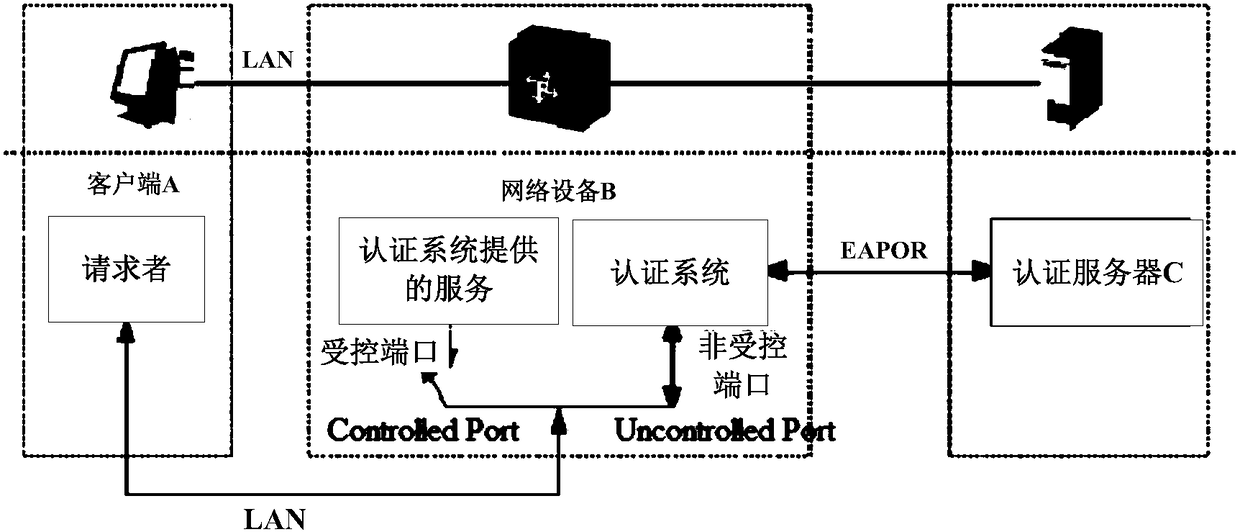
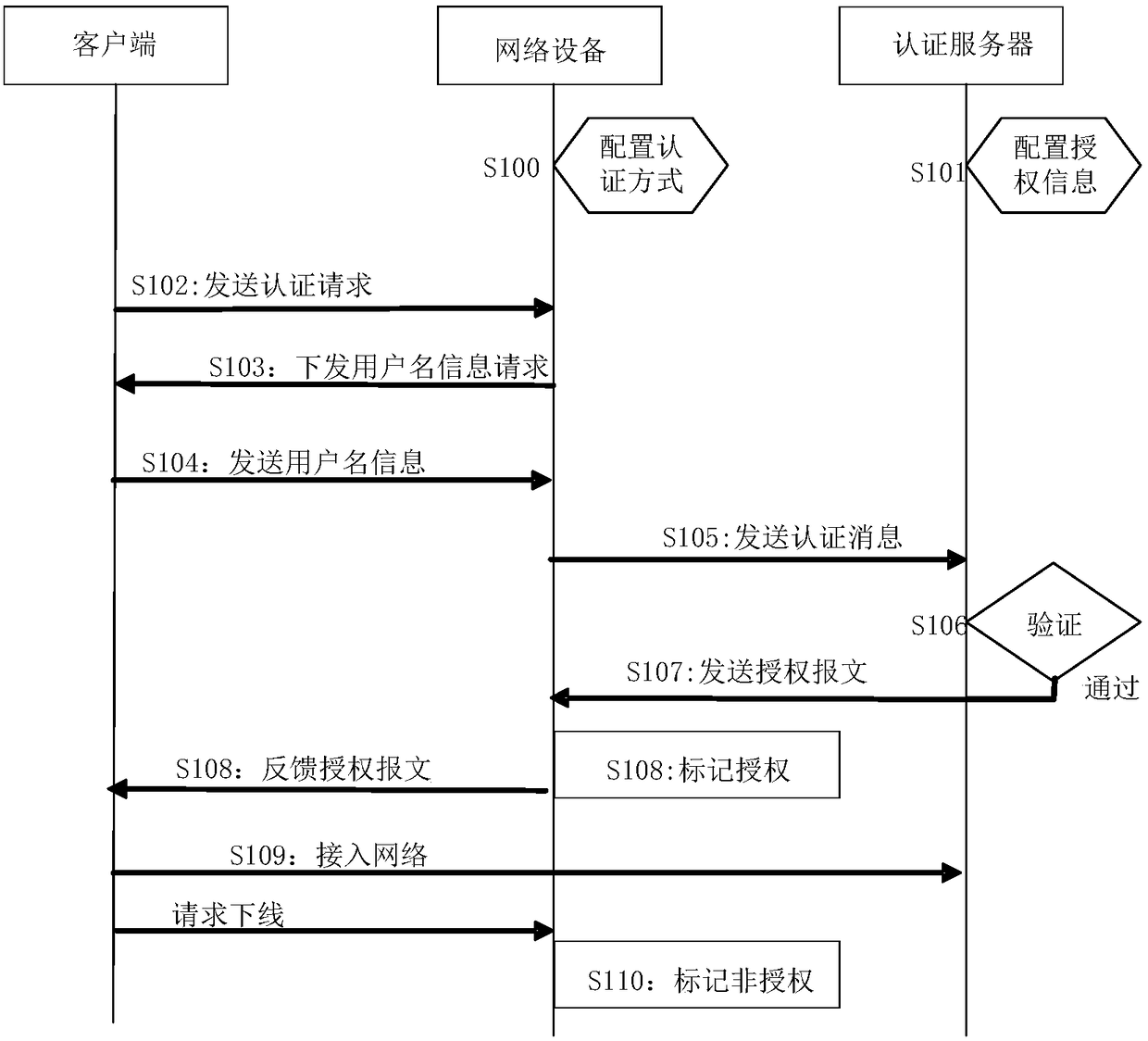
[0078] like figure 2 As shown, it is a schematic flowchart of a network access control method provided by Embodiment 1 of the present invention. The network access control method is applicable to network devices in the network access control system. In this embodiment, through service-based authentication, only services that pass the authentication can access the network, so that different services do not interfere with each other. It achieves the purpose of enhancing the isolation between different services, and achieves the purpose of greatly increasing the security of network access compared with only one user authentication, and realizes the purpose of reducing the complexity of network deployment by authenticating each user Purpose.
[0079] When executing the network access control method, such as figure 2 As shown, first execute steps S100 and S101 to pre-set network devices and authentication servers; then execute steps S102 to S110 to perform service authenticatio...
example 1
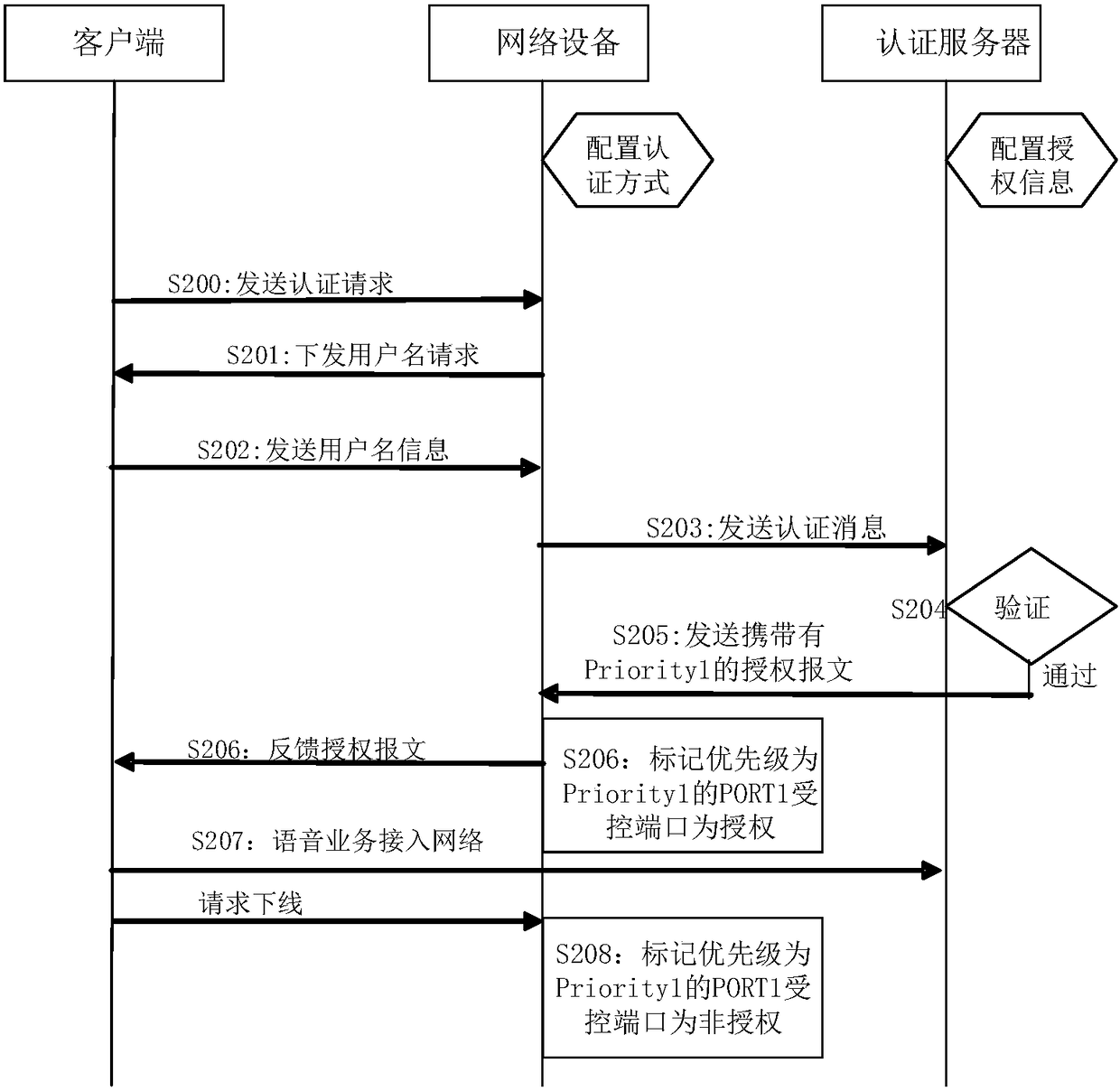
[0105] Based on the above-mentioned network access control method disclosed in Embodiment 1 of the present invention, taking the specific application scenario of configuring a controlled port as an example, when the IEEE 802.1p priority of the PORT1 controlled port of the network device is preset as Priority1 and Priority2; The user service authorization information pre-configured by the authentication server indicates that the priority of the service that can be authorized is Priority1;
[0106] When the service types currently available to the user are voice services and streaming media services, the user service types are distinguished through the IEEE 802.1p priority, and the priority of the user's voice service is set as Priority1 (priority 1), and the user's The priority of the streaming media service is set to Priority2 (priority 2); that is, the PORT1 controlled port with the priority of Priority1 corresponds to forwarding the data traffic of the voice service, and the ...
Embodiment 2
[0125]Based on the network access control method disclosed in the above-mentioned embodiments of the present invention, the authentication method adopted in the process of network access control is service authentication. In addition to using the service authentication method, Embodiment 2 of the present invention also discloses Authentication mode network access control, and network access control combined with VLAN authentication mode;
[0126] When combining service authentication and MAC authentication, specifically combining the above-mentioned network access control method disclosed in Embodiment 1 of the present invention, only the difference between the two will be described, and the principles of other execution steps are the same. The description in Embodiment 1 of the invention will not be repeated here:
[0127] When step S100 is performed to pre-set the network device, the network device classifies the service type of the user through the IEEE802.1p priority on th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com