Anti-phishing method and system based on blockchain
A blockchain and anti-phishing technology, applied in the field of network security, can solve problems such as illegal use of user reserved information, and achieve the effect of reliability and security guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
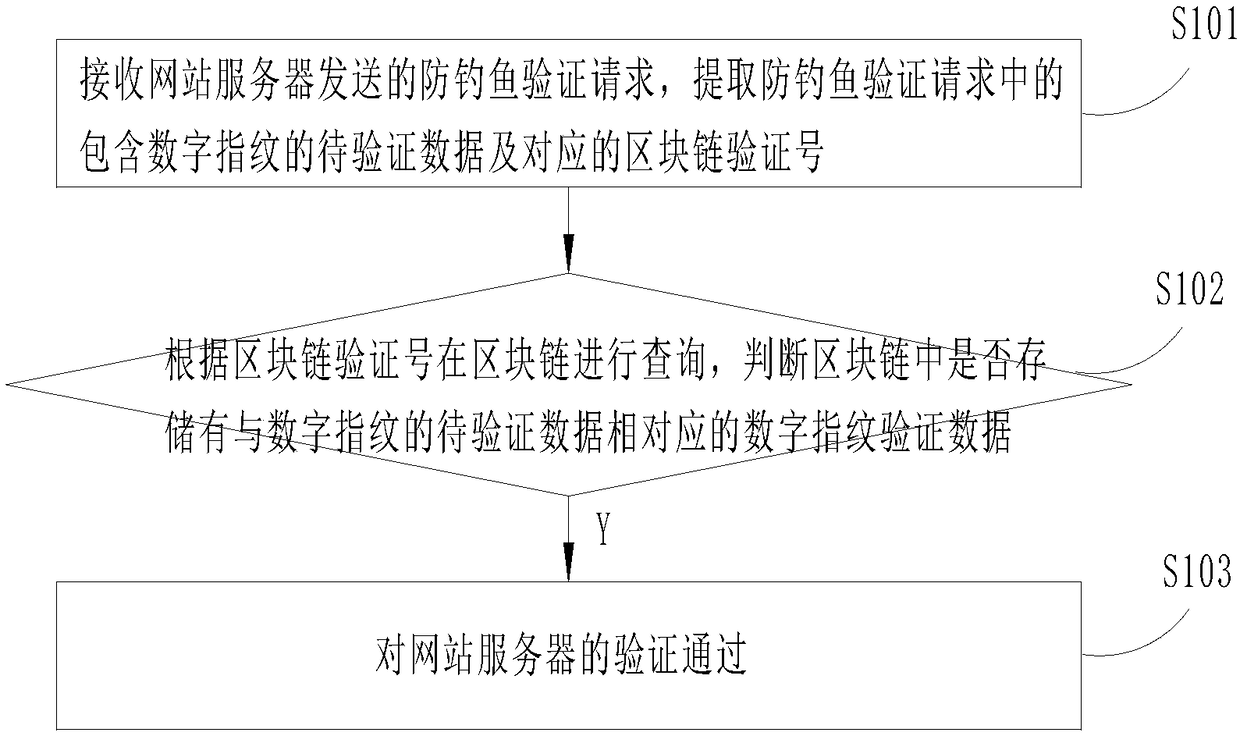
[0024] Embodiments of the present invention provide a blockchain-based anti-phishing method, such as figure 1 As shown, the anti-phishing method includes the following steps:
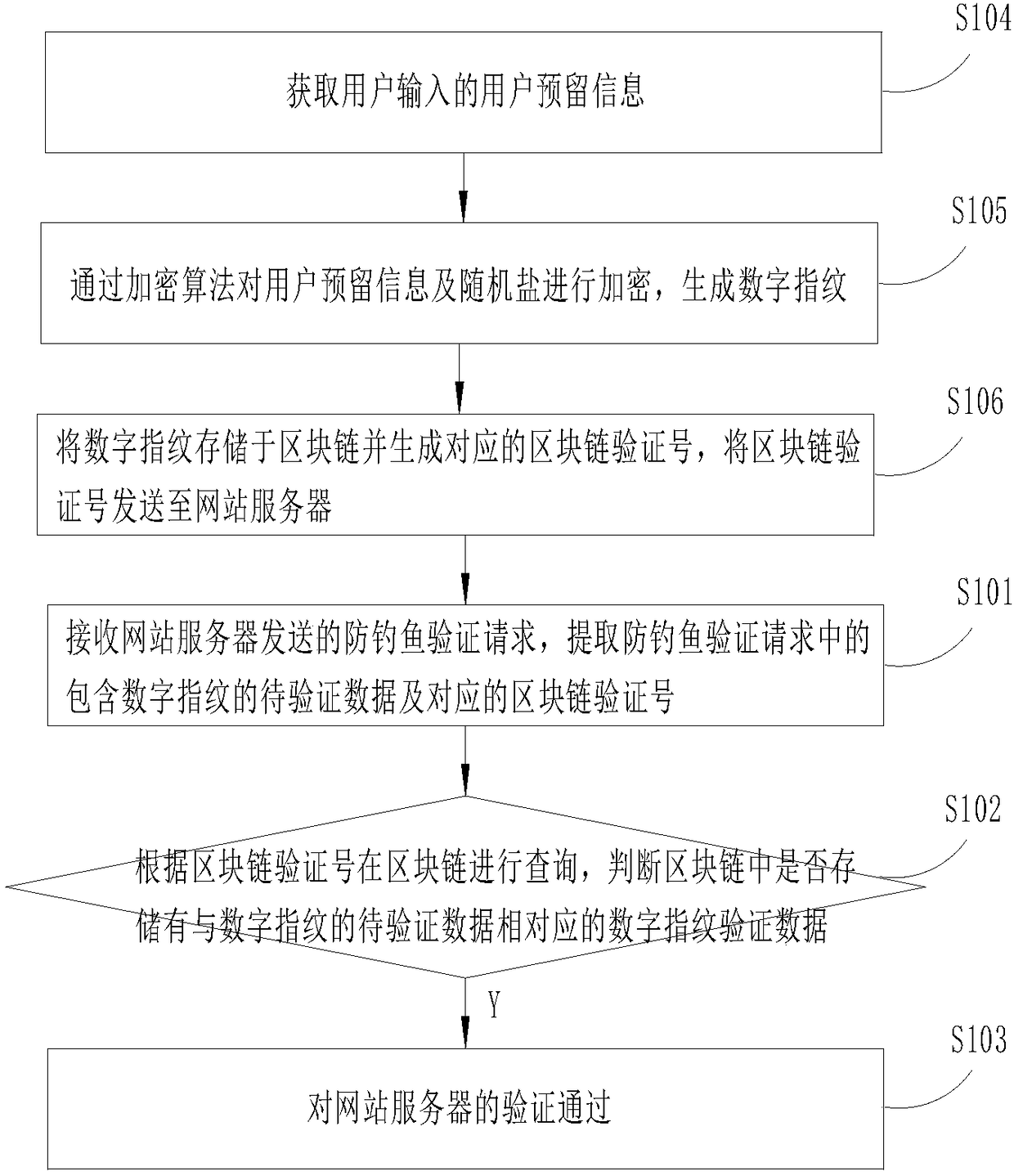
[0025] Step S101: Receive the anti-phishing verification request sent by the website server, and extract the data to be verified including the digital fingerprint and the corresponding blockchain verification number in the anti-phishing verification request. In a specific embodiment, the digital fingerprint is an encrypted character string generated by encrypting the data including the user reserved information and the random salt through an encryption algorithm.
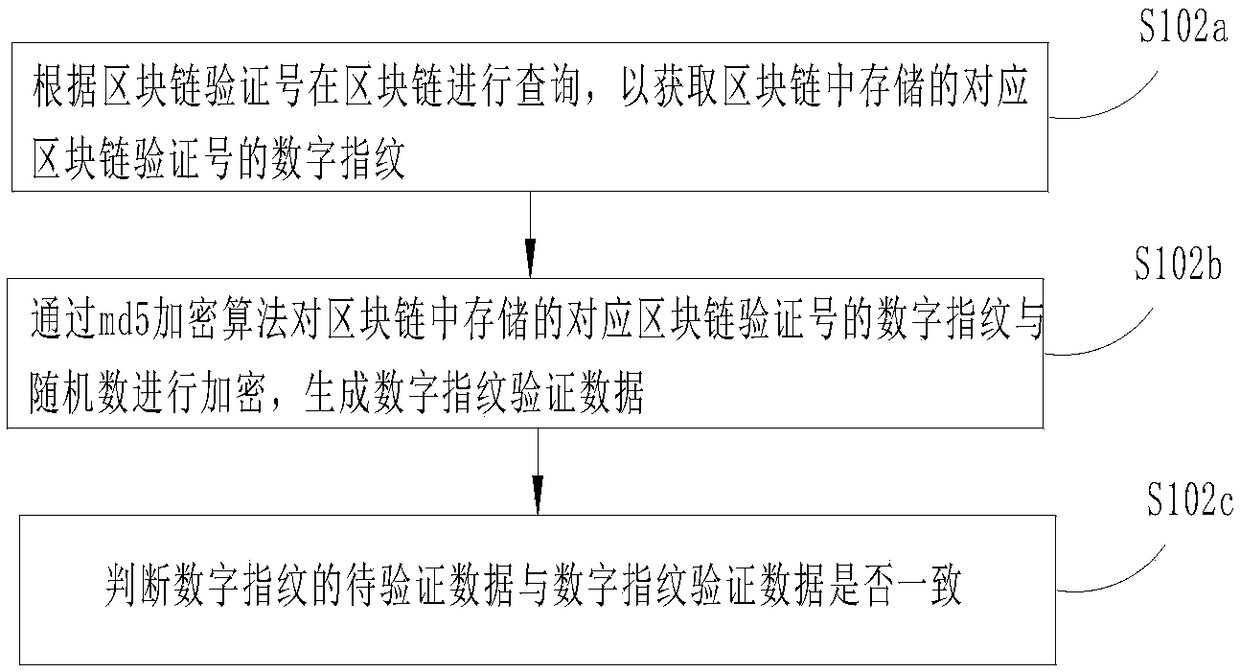
[0026] Step S102: Query the blockchain according to the blockchain verification number to determine whether digital fingerprint verification data corresponding to the data to be verified of the digital fingerprint is stored in the blockchain.
[0027] Step S103: When the digital fingerprint verification data corresponding to the digital fing...
Embodiment 2
[0044] The embodiment of the present invention provides a blockchain-based anti-phishing system, such as Figure 5 As shown, the anti-phishing system includes: a receiving module 1 and an inquiry and verification module 2 . Wherein, the receiving module 1 is used to receive the anti-phishing verification request sent by the website server, extract the verification data containing the digital fingerprint in the anti-phishing verification request, and decrypt the verification data to extract the digital fingerprint. For details, please refer to step S101 and step S102. The query and verification module 2 is used to query the block chain according to the digital fingerprint to determine whether the digital fingerprint verification data corresponding to the digital fingerprint is stored in the block chain; when the block chain stores the digital fingerprint corresponding to the digital fingerprint When verifying the data, the verification of the website server is passed. For deta...
Embodiment 3
[0046] An embodiment of the present invention provides a non-transitory computer-readable storage medium, where the computer-executable instruction is stored in the computer-executable instruction, and the computer-executable instruction can execute the anti-phishing method in any of the above method embodiments. Wherein, the storage medium may be a magnetic disk, an optical disk, a read-only memory (Read-Only Memory, ROM), a random access memory (Random Access Memory, RAM), a flash memory (Flash Memory), a hard disk (Hard Disk Drive, abbreviation: HDD) or a solid-state drive (Solid-State Drive, SSD), etc.; the storage medium may also include a combination of the above-mentioned types of memory.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com