A safe routing method realized by aodv or dsdv protocol
A protocol implementation and routing technology, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve problems such as poor scalability and inability to maximize network security performance, and achieve strong practicability and good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be described in further detail below with reference to the accompanying drawings.
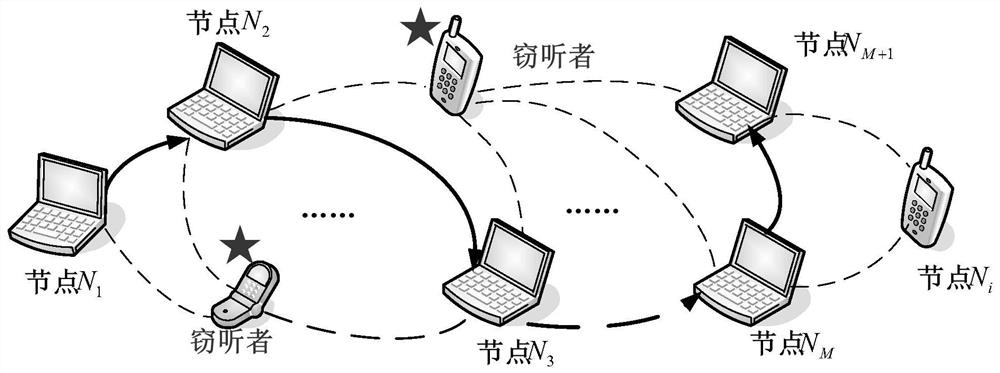
[0051] Such as figure 1 Shown, the distribution of nodes and eavesdroppers.
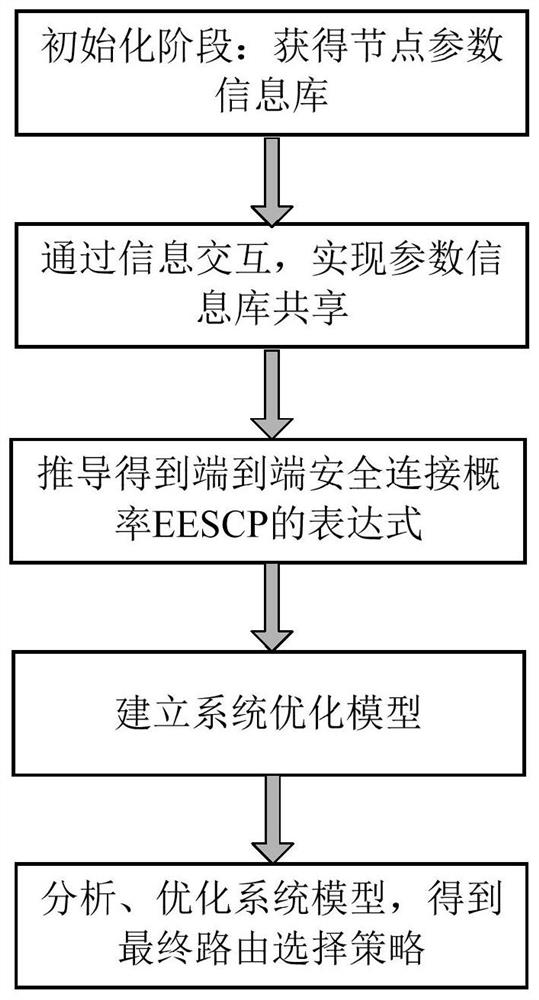
[0052] Such as figure 2 As shown, the process of a secure routing method that can be implemented using the AODV or DSDV protocol can be summarized as follows: initial stage: obtain node parameter information database; realize parameter information database sharing through information interaction; derive end-to-end secure connection probability The expression of EESCP; establish the system optimization model; analyze and optimize the system model, and get the final routing selection strategy.
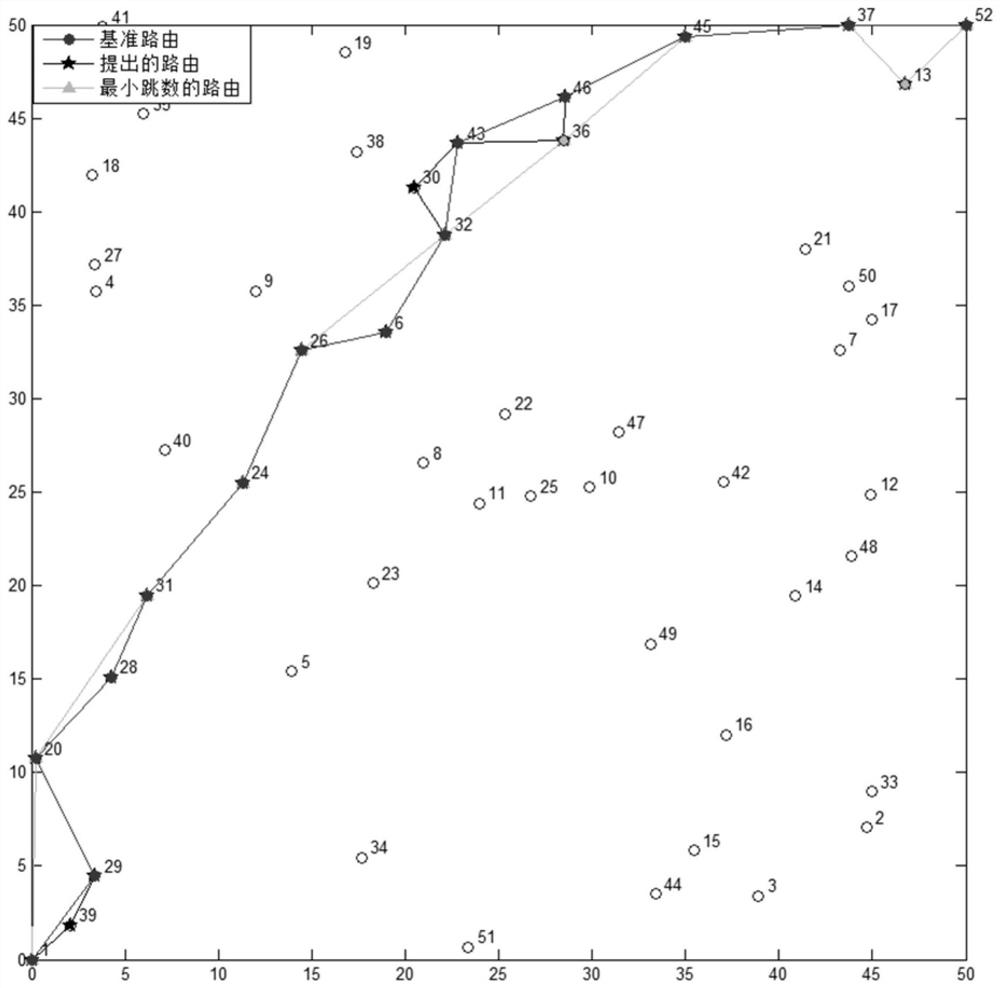
[0053] image 3Several routing algorithms are compared when the eavesdropper density is λ=10 -5 time safety performance. Algorithm (I), (II) and algorithm (III) respectively represent the shortest path algorithm, the improved shortest path method, the traversal method and the minimum hop r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com