Self-owned post quantum key distribution method
A quantum key distribution and key technology, applied in the field of quantum communication, can solve the problems of data loss and tampering, not really storing data, deliberate deletion, modification, etc., to achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
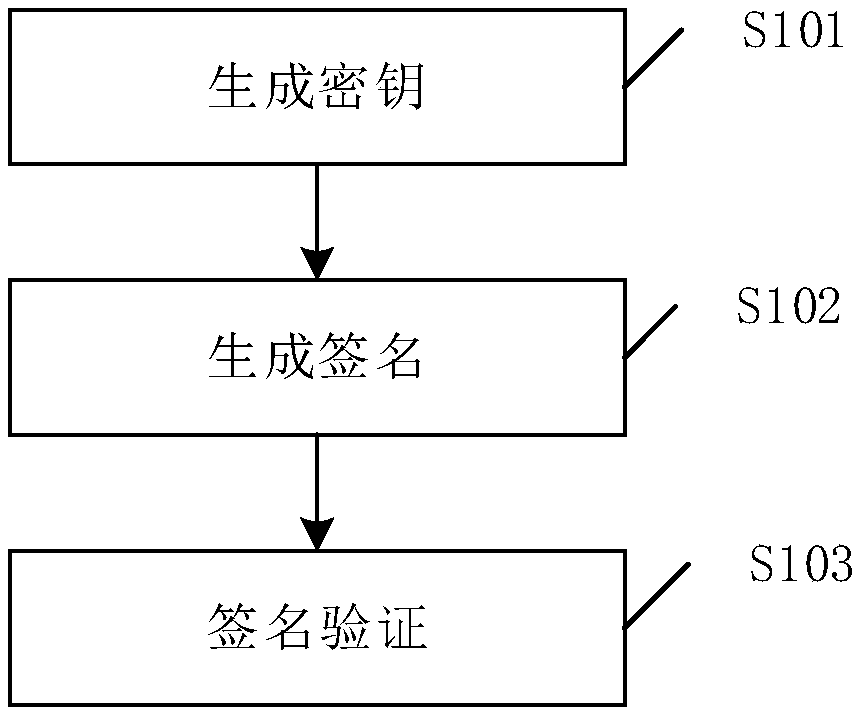
[0024] Such as figure 1 As shown, a self-owned post-quantum key distribution method of an embodiment of the present invention is provided, the method includes steps S101-S103:
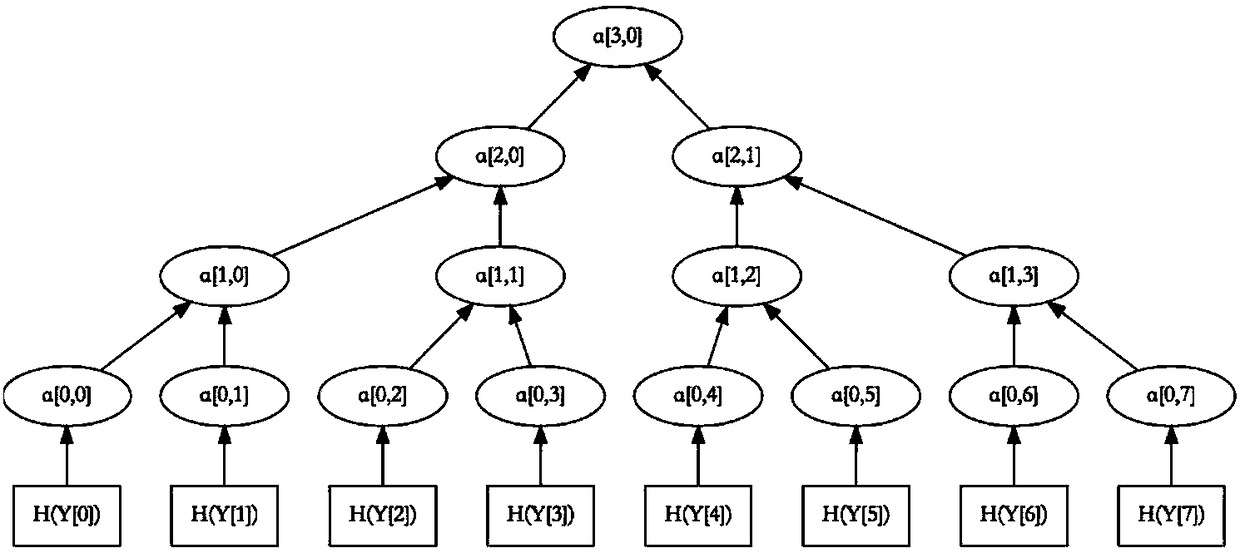
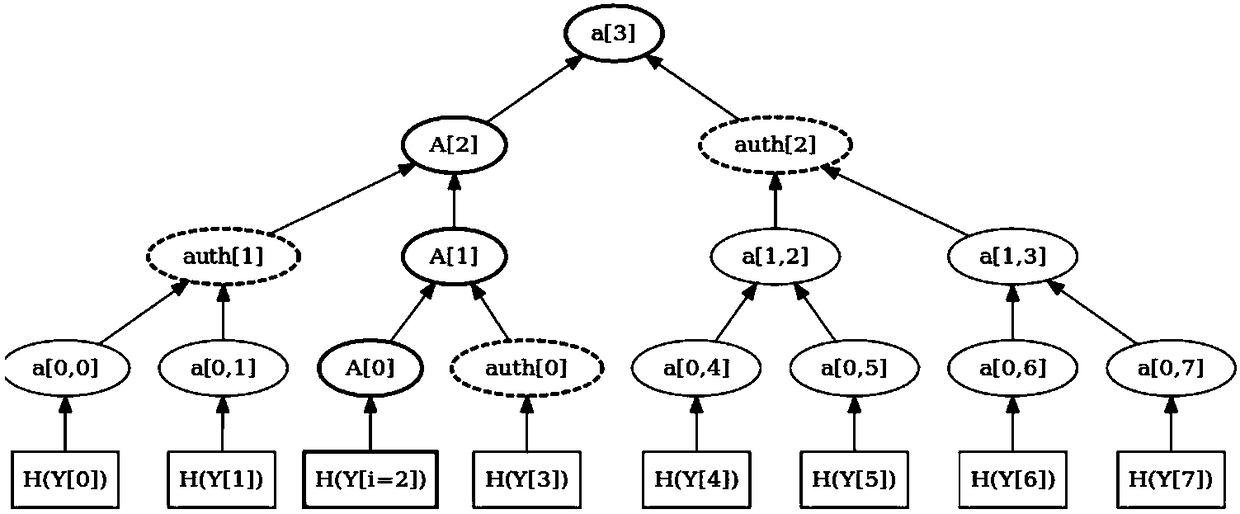
[0025] S101. Generate multiple keys: the sender uses a hash tree to generate multiple keys. When there are multiple public keys, the hash tree first calculates the public key Y i Get the initial hash value of the initial node, and then continue to calculate the hash value of the i-1th node of the initial node, the value pair of the i-1th node is the key X i , and then continue to calculate the hash value Y of the jth node j , the value pair of the j-1th node is the key X j , until only the hash value of the last node is left; if the public key of the jth node is Y j , then set the key X j and public key Y j is the key pair (X j , Y j );
[0026] The public key refers to the public key, which is stored at the sending end and the receiving end.
[0027] Hash tree (HashTree) is an ideal data stor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com