Image encryption method for decryption area limitation using directed area and poker mapping
An encryption method and technology for playing cards, which are applied to encryption devices with shift registers/memory, image communication, and secure communication through chaotic signals, etc., and can solve the problems that the key does not consider the limitation of decryption position and potential safety hazards.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
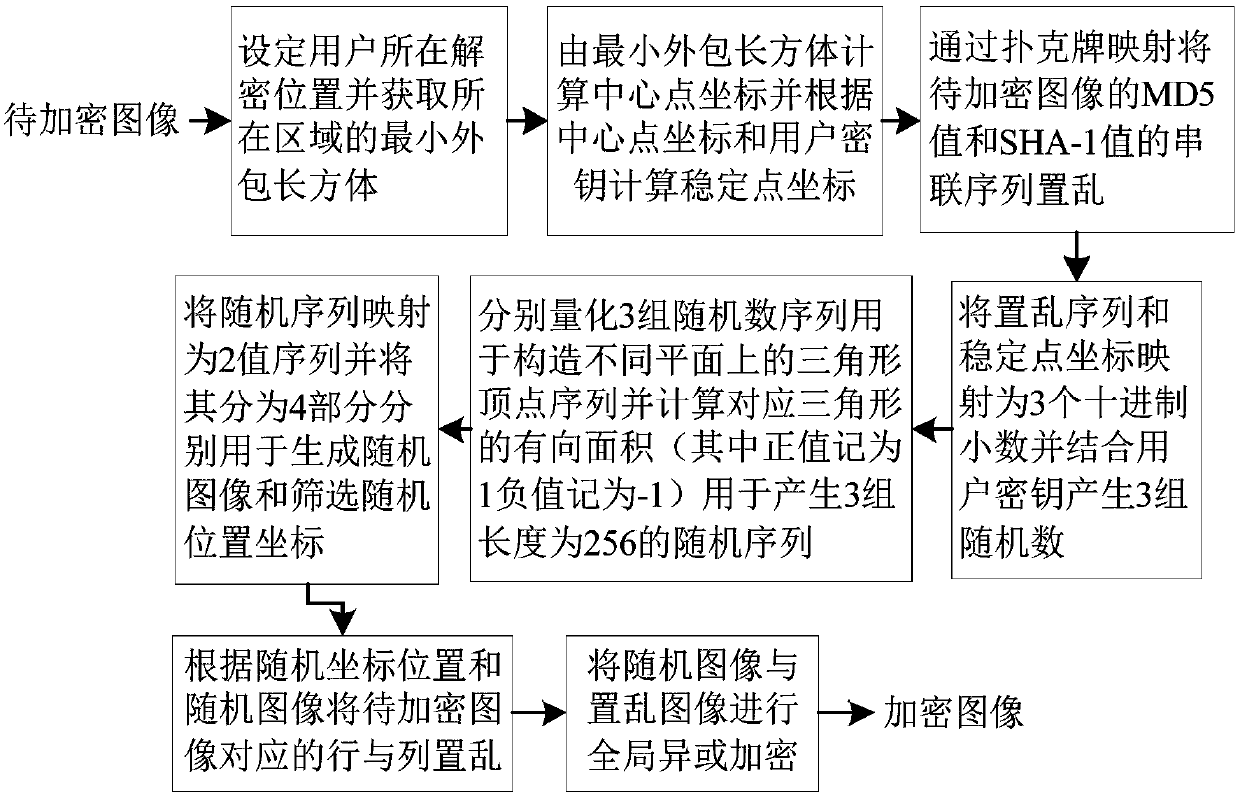
[0198] The following takes JAVA jdk1.8.0_131 as the case implementation environment, and describes the implementation of the present invention in detail in conjunction with the accompanying drawings, but is not limited to this implementation case, where figure 1 is the flow chart of the encryption process, figure 2 Is the flow chart of the decryption process.
[0199] The concrete implementation steps of image encryption method:
[0200] Step 1: record the image to be encrypted as A=(a i,j ) m×n , set the decryption location of the user (x 0 ,y 0 ,z 0 ) ∈ region, according to formula (1) to obtain the smallest outsourcing cuboid of the region region where x min ,x max ,y min ,y max ,z min ,z max Respectively represent the starting and ending ranges of the corresponding x-axis, y-axis, and z-axis coordinates on the cuboid;
[0201] Suppose the selected image matrix to be encrypted is Set the decryption location of the user (x 0 ,y 0 ,z 0 ) ∈ region, assuming...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com