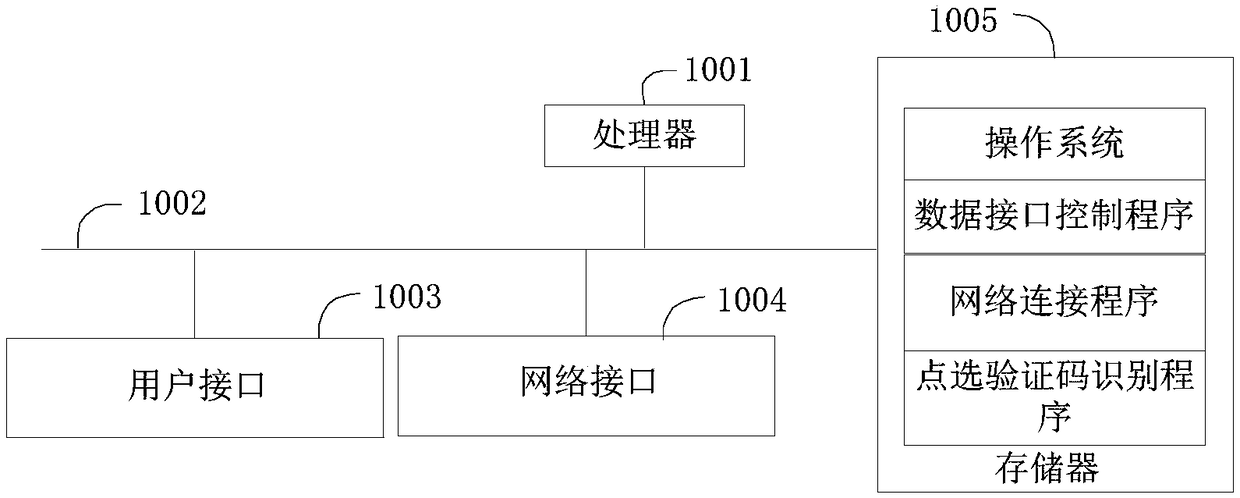
Click verification code identification method and device, and user terminal
An identification method and verification code technology, applied in the field of verification code testing, can solve the problems of identification failure, low accuracy, complex algorithm, etc., and achieve the effects of convenient security testing, improved accuracy, and high identification efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
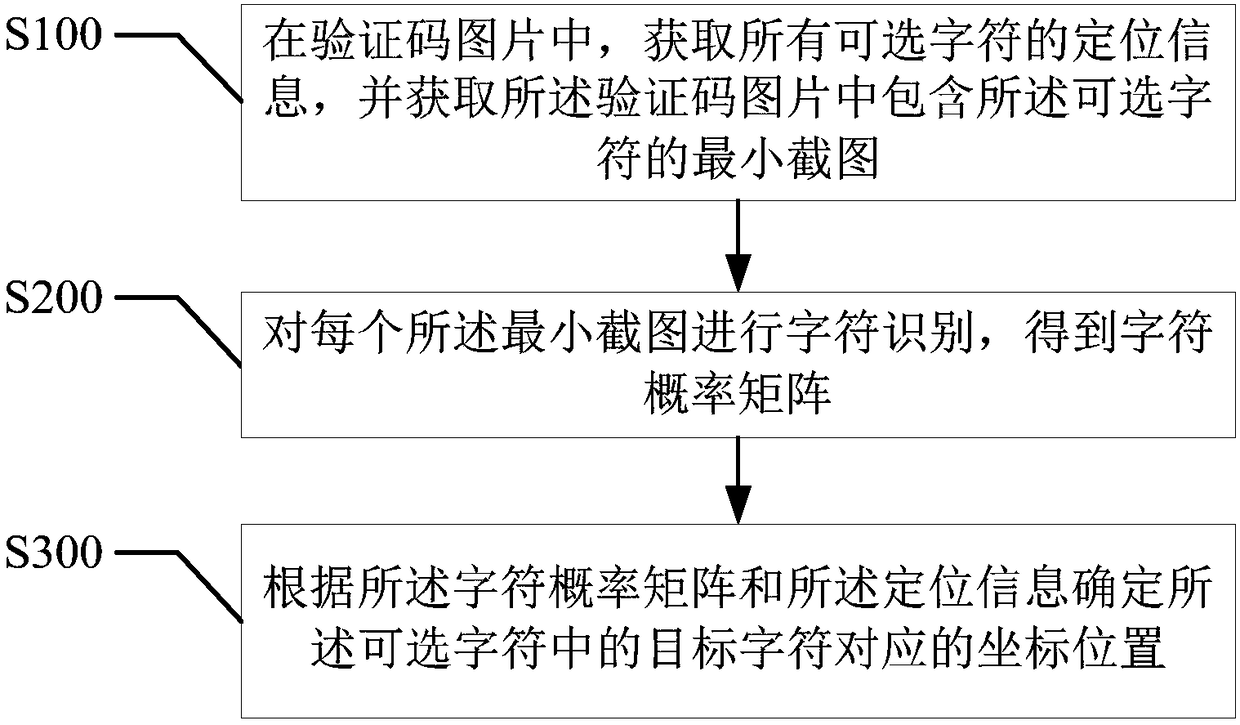
[0056] refer to figure 2 , the first embodiment of the present invention provides a verification code recognition method, including:
[0057] Step S100, in the verification code picture, obtain the positioning information of all optional characters, and obtain the smallest screenshot containing the optional characters in the verification code picture;
[0058] As mentioned above, what needs to be understood is that point-and-click verification is also called point-touch verification, and its working principle is as follows: first, the server randomly generates N (any number, usually 5) Chinese characters (or other characters, symbols), and uses the graphic library Generate images of Chinese characters and add noise backgrounds to the images. Then randomly generate 5 locations in a large background image, and fuse 5 Chinese characters with the background image. Randomly select three Chinese characters from the five Chinese characters and store the corresponding positions in ...
Embodiment 2
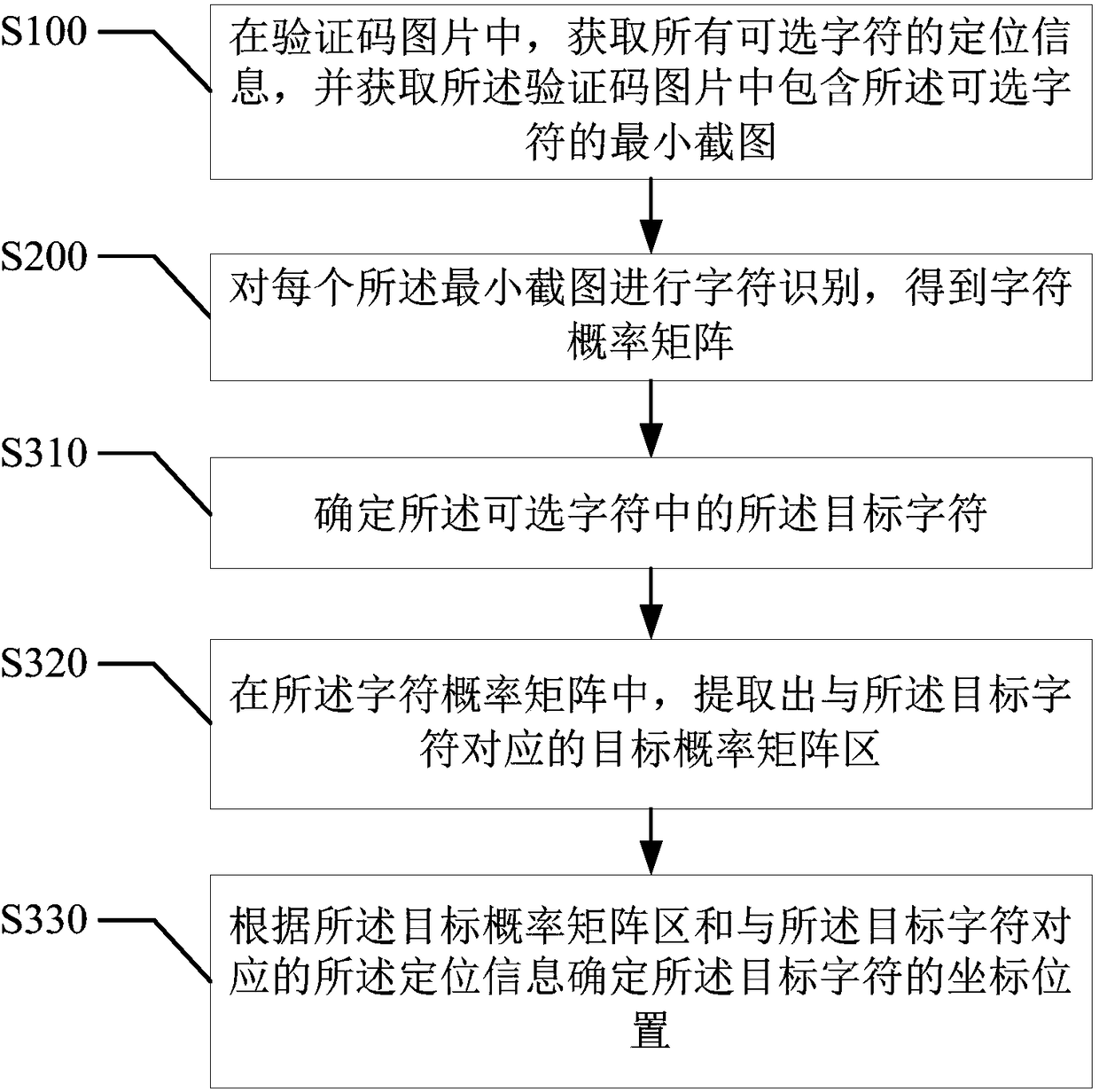
[0071] refer to image 3 , the second embodiment of the present invention provides a verification code identification method, based on the above figure 2 In the first embodiment shown, the step S300 includes:
[0072] Step S310, determining the target character in the optional characters;
[0073] As mentioned above, in the security verification technology of clicking the verification code, generally a plurality of different characters are provided, and then the system prompts to select some of the characters. For example, there are 6 optional characters in the verification code picture on the website, which are "Water Margin Westward Journey to the Red Mansion", and the website prompts that the target characters in it are water, west and red.
[0074] As mentioned above, in this embodiment, it is determined which of the plurality of optional characters prompted by the website or the system is the target character. Several of the optional characters can be selected, or the...
Embodiment 3
[0081] refer to Figure 4 , the third embodiment of the present invention provides a verification code identification method, based on the above image 3 In the second embodiment shown, step S330 includes:
[0082] Step S331, extracting the maximum probability value corresponding to each minimum screenshot in the target probability matrix area;
[0083] As mentioned above, in the target probability matrix, each smallest screenshot corresponds to a large number of results with different probabilities, and the results appear in the form of probability data. Select the maximum probability value among different probability values, which is the system judges that it is the closest to this implementation. The character of the smallest screenshot taken in the example. Through the determination of the maximum probability value, the corresponding relationship between the target character and the positioning position of the character in the verification code picture is determined.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com