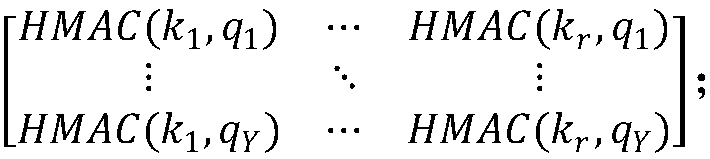Verifiable ciphertext data range query method
A technology of data range and query method, applied in the field of cloud computing, can solve problems such as inability to obtain correct conclusions and analysis deviations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
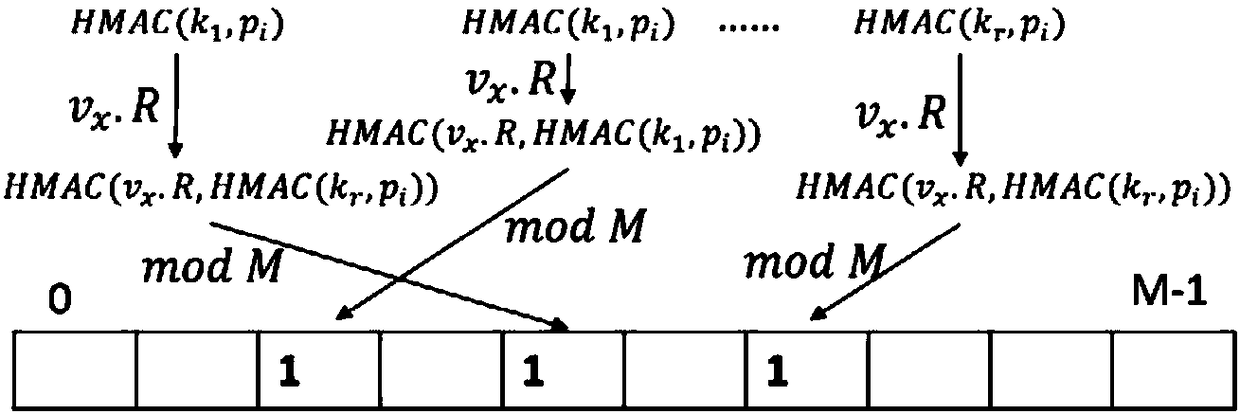
[0068] This embodiment discloses a verifiable ciphertext data range query method, the steps are as follows:
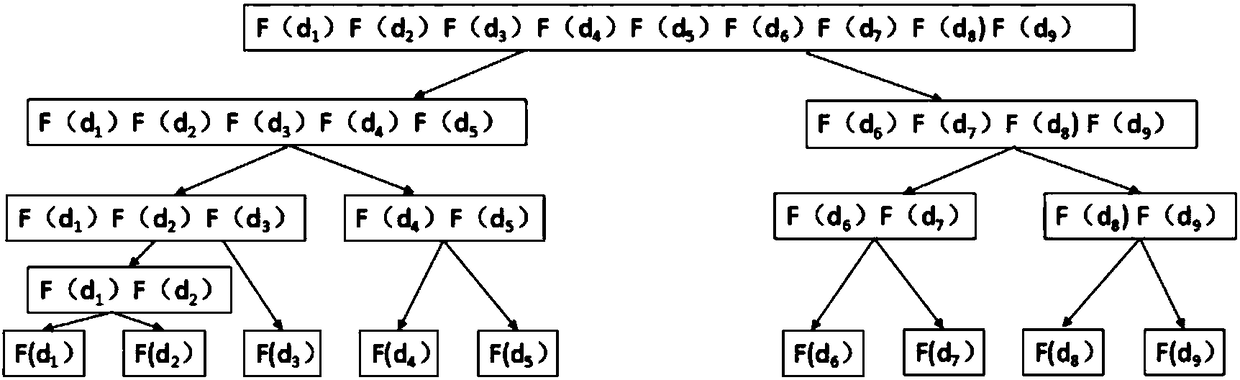
[0069] Step S1, for each local data that the data owner needs to upload to the cloud server, first sort the local data that needs to be uploaded to the cloud server at the data owner terminal according to the order from large to small or from small to large, and then for For each local data, record the front and rear data of each local data at the same time, and obtain the triplet data of each local data; at the same time, convert each local data into a prefix set, and according to the sorting of each local data, the prefix set of each local data Stored in a tree-like PBtree;
[0070] Wherein, in this step, when sorting the local data that needs to be uploaded to the cloud server according to the order from large to small, the first local data and the positive infinity symbol and the second local data form triplet data, The last local data, the penultimate local data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com